More than 14,000 people every month are looking for what to do in order to reset and recover the login and password of the Windows 7, 8 or 10 administrator account, because they cannot remember it and change it to unlock the login to their computer or laptop. I also had such a case - they brought a PC and asked me to install several programs on it. But it turned out that the login to the system was blocked, and the previous owner, of course, forgot the Windows password. Unfortunately, at that time I did not have sufficient knowledge to reset and unlock it - I had to reinstall the operating system. But today we have become more savvy in this matter, so I am sharing this information with you.
How to reset your account and unlock login if you forgot your Windows password?
So, the problem appears to us in the following form - we turn on the computer, the Windows account login screensaver lights up, but we have forgotten the password for it. Of course, we won’t be able to get into the system in the usual way. There are two ways to recover your password:
- built-in tools without installation disk
- from the disk or flash drive from which the system is installed
- using a recovery disk with a set of special programs for resetting the password
I assume that most readers do not have a flash drive with a system recovery software package, although I would strongly recommend having one in the house, as they say “just in case” (I have already told you in detail how to make one).
So let's start with more realistic options.
Hacking a password for a user with limited access rights
If this is the case when you cannot remember the combination to your account and are not a system administrator, then you need to use safe mode login (press F8 before starting the system startup). Next, in the User line, you need to enter the name of the User, who is the Administrator, and enter the key. This will allow you to log in to the system as an Administrator.
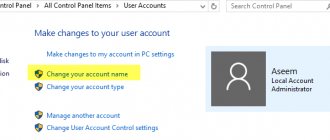
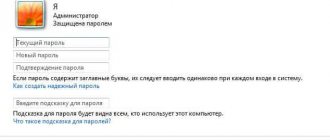
When you are logged in, you need to go to the “Start” menu and through the “Control Panel” go to the “Accounts” menu. In front of you you will see a list of user profiles, among them you need to select your account. In the User Features menu options, you will find the Edit Features option. Here you need to select the option “Remove password” or “Change password” and enter a new one. All these changes must be saved, otherwise they will not be relevant.
Reset Windows 10 password without disk and programs
The easiest way to reset your account password is as follows: However, please note that ALL DATA WILL BE DELETED! The PC will return to its full factory state, as if Windows 10 had just been installed.
- Turn on the computer and at the authorization stage click on the shutdown icon in the lower right corner of the screen
- Next, hold down the “SHIFT” key and select “Reboot”
- Confirm your choice
- After restarting Windows, select “Troubleshooting” from the boot menu
- And then “Return the computer to its original state”
After this, Windows will reset all settings, including the local account password.
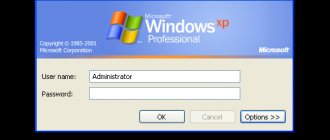
Test 1 - complex password in Windows 7
To begin with, I downloaded Ophcrack LiveCD for Windows 7 (for XP there is a separate ISO on the site), set the password to asreW3241
(9 characters, letters and numbers, one capital) and booted from the image (all actions were carried out in a virtual machine).
The first thing we see is the Ophcrack main menu with a proposal to run it in two GUI modes or in text mode. For some reason, the graphics mode did not work for me (I think due to the nature of the virtual machine, everything should be fine on a regular computer). And with text - everything is in order and, probably, even more convenient.
After selecting text mode, all that remains to be done is to wait for Ophcrack to finish and see what passwords the program was able to identify. It took me 8 minutes, I can assume that on a regular PC this time will be reduced by 3-4 times. First test result: password not defined.
Resetting the Windows administrator password using a recovery flash drive without BIOS
There is a similar algorithm of actions for XP, but for it, as for any other version, there is an easier way. Usually, to reset the Windows administrator account password, I use my favorite recovery flash drive with the Passware Reset Windows Password program written on it. The program interface is intuitive, and in terms of functionality - the program automatically performs the same actions that we did manually - it resets the Windows administrator password in the registry and creates a new one.
If you are interested in learning about it in more detail, and if after reading this article you still have questions, what to do if you forgot your Windows password, ask in the comments.
How to change a user's password?
If you have not yet logged out of the system and are in the Administrator panel, then you can easily reset the key without performing any special actions. You just need to go through “Start” to “Settings”, select the “User Accounts” menu and in the tab of the user you are interested in, select the “Reset Password” menu. The system will prompt you to enter a new one, you can do this procedure or leave the fields blank. Next, save the settings by clicking “OK”. This will complete the work of changing the key.
Reset using the Command Sheet
From the Start menu, select Run and type cmd, then click OK. In the open window, you need to enter control userpasswords2 and among the accounts, select the one that is needed to reset the password. In Settings, uncheck “Require username and password” and save. Or go to the “User X Password” section, select “Change Password” and enter a new one (or leave it blank), save by clicking “OK”. Having done all this, close the window and try to reboot the system.
Reset via Microsoft miniPE disk
If you have such a disk, you can use it or download this utility from the official website and burn it to a disk or flash drive. When booting the system, you need to enter the Bios system (F1, F2, DEL or Esc) and select loading the OS via CD-ROM or other media (USB port). After the next system restart, booting will occur from external media with the ability to log in via miniPE. Here you need to go to “Start”, then to the “Programs” menu, then to “System Tools” and select the Password Renew option. Here select Select Windows Folder, specify the Windows system folder and select the Renew existing user password option for the desired system user (from the drop-down list). Enter and confirm the new key combination, save and restart the system using the Reboot command. Don't forget to go into Bios and restore boot settings from the hard drive. That's all - the new password for the Administrator is ready to use.
Hacking the admin password
This is a more complex, but possible procedure for hacking an administrative account. It occurs using a resuscitation disk with a specific set of software. In the disk menu, you need to select a copy of the OS to edit and go to the “System Restore” section. Here in the dialog settings you need to select “Command Line”, enter regedit and confirm the launch of the program to edit the contents of the registry. Then you need to find the section called HKEY_LOCAL_MACHINE and select the “Load hive” command in it. Next, open the subsection with 888 Setup and edit the value after the CmdLine key by double-clicking it. In the open command line, enter the cmd.exe configuration and save by clicking “OK”. In the next step, you need to set the value “2”, focusing on the SetupType key. Save all configurations for changes to the subkey for 888, specify the hive dump file, and reboot the computer. Then enter the net user login in the username field and create a new password when you turn on the computer. And this issue with hacking the admin panel will be resolved.
Using Mimikatz in pass-the-hash attacks
If the user has a fairly complex password and it cannot be obtained quickly, you can use Mimikatz for a pass-the-hash attack (hash reuse). In this case, the hash can be used to run processes on behalf of the user. For example, given the NTLM hash of a user's password, the following command will launch a command prompt as a privileged account:
privilege::debug sekurlsa::pth /user:Administrator /domain:srv01 /ntlm:e19ccf75ee54e06b06a5907af13cef42 /run:powershell.exe
You can also use the Invoke-TheHash utility to use the NTLM hash to execute commands on remote computers. Allows also
userLevel2system and find out the administrator account password
We increase privileges to system privileges using the KiTrap0d exploit, and also extract the admin password using PWdump and L0phtCrack.
So, I will state the essence of the matter. Let's imagine a very familiar situation (for students and secretaries): the administrator account is locked from crooked hands with a password, and we are in a regular (guest) account. Without knowing the password or not having administrator rights, we cannot rummage around on the administrator’s desktop (like “C:Usersadmin” - Access is denied), we cannot change the Program Files and Windows folders... - and we really need it! What to do?
At the beginning of 2010, hacker T. Ormandy published a 0-day vulnerability that allows privilege escalation in any version of Windows. This exploit was named KiTrap0d and in current antivirus databases it is listed in a section like Win32.HackTool (“hacker tool”).
So, turn off the antivirus (well, you trust me!). Next, download it from my documents at https://www.box.net/shared/1hjy8x6ry3 (password nagits - so that the antivirus does not swear) or search on the site https://exploit-db.com named Tavis Ormandy. The compiled exploit consists of 2 files: the library vdmexploit.dll and the executable vdmallowed.exe. By clicking on the exe file, the exploit starts and the cmd.exe command line opens with NT AUTHORITYSYSTEM system privileges!
And now, as they say, the flag is in your hands! With these rights, you can copy the files you need, find out valuable information...
..., but still it will be much more useful to know the admin password.
Account passwords in Windows are stored as hashes in special registry branches HKLMSAM and HKLMSECURITY and access to them is denied even to administrators. The corresponding Security Account Manager database files are located in the %SystemRoot%system32config folder in the SAM and SYSTEM files, but you cannot simply copy them, however, more on that a little later. That’s why it’s so important that we get system rights.
I will talk about two approaches to obtaining a known password. One concerns, as you probably understood, the registry - password dump. The second approach, as Captain Obvious advises, is to obtain the SAM file.
We will use the fairly well-known pwdump utility, which you can download from My Documents at https://www.box.net/shared/9k7ab4un69 (password nagits). Switch to the cmd.exe command line with system rights and run pwdump.
The utility will dump passwords to a file.
For example, pass_dump.txt might look like this:
It can be seen that Uzver is a regular user, not protected by a password, and VirtualNagits is an administrator, and the hash of his password is given.
Next, all that remains is to use a brute force to decrypt the dump.
For example, I will use the l0phtcrack program. You can download the bloomer at www.l0phtcrack.com/.
Starting with Windows NT 3.1 (July 27, 1993), passwords are stored in the so-called. NTLM hash. Unfortunately, the l0phtcrack program will agree to attack NTLM hashes only after registering the purchase of the software product. By the way, the installation must be run with administrator rights - at a minimum. Therefore, we run the installation file from cmd.exe with System rights.
So I have l0phtcrack v5.04 installed and registered and pass_dump.txt:
In the l0phtcrack program, click on the Import button:
Select import from the PWDUMP file (From PWDUMP file), specify our pass_dump.txt.
Now you need to check the options for cracking NTLM passwords:
Confirm your selection by clicking OK and click Begin Audit.
Eat! The tricky administrator password “123456” has been received!
Normal 0 false false false RU X-NONE X-NONE MicrosoftInternetExplorer4 Instead of pwdump and l0phtcrack, I also recommend using the freeware program Cain&Abel. I will show off this wonderful tool in another article).
In general, you cannot copy the SAM file from C:windowssystem32config even with SYSTEM rights, since they are “occupied by another application.” The task manager will not help, because even if you find the culprit process responsible for Security Account Manager, you will not be able to terminate it, since it is a system one. Basically, all of them are copied using a boot disk, in which case we don’t even need administrator rights. But often you don’t have a LiveCD in your hands...
Well, you can read these files using low-level disk access.
This is very well described on the website https://wasm.ru/article.php?article=lockfileswork under the title (Reading a file using direct disk access).
Here is a link to the compiled program: https://wasm.ru/pub/21/files/lockfileswork/RawRead.rar (An example of reading SAM using direct access to a volume).
Using the command (from cmd.exe with system rights, remember KiTrap0D?):
the program copies the SAM file from the configSAM system directory to the file specified in the parameter, i.e. D:TMPSAM
The l0phtcrack brute forcer supports importing SAM files, but the program vehemently warns about SYSKEY encryption:
L0phtcrack does not have the ability to break the advanced SYSKEY encryption of the SAM database. Therefore, if the system being hacked uses SYSKEY encryption (I think it is used starting with Service Pack 3 for NT 4.0, in 2000/XP - by default), you must additionally decrypt the SAM file, or use method 1.
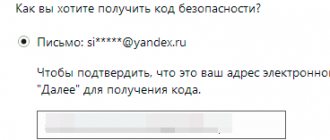
If you've forgotten your Microsoft account password on your phone, Windows 10, or another device (such as an XBOX), it's relatively easy to recover (reset) it and continue using your device with your old account.
This instruction details how to recover a Microsoft password on a phone or computer, what is required for this, and some nuances that may be useful during recovery.
Is it possible to reset a user's key?
This is only possible when you are in an administrator account and have not yet logged out of the system. Then you can simply change the key without knowing the old one. To do this, go to the “Settings” menu through the “Start” button, select “User Accounts”, then click “Reset Password”. Write a new one in the line that opens.
Where is the computer key kept?
The operating system registry acts as a repository for all device data. When you turn on the computer, it checks the characters entered and stored in the registry. If they do not match, you will be asked to enter them again.
How to remove user password?
If you are a regular user (not an administrator) and accidentally forgot the code. To do this, you just need to enter the software in safe mode by pressing the F8 key. How to enter safe mode in new versions of Windows was written in this article. After that, log in as an Administrator by entering his name and password. Open, find “Accounts” through the “Control Panel”. Among the many, find the account you need and edit (through the “Withdraw” or “Delete password” items). This method will be relevant if you know the Administrator’s details; if you don’t have them, then read below.
How to hack windows 7 administrator password?
Link to a thematic video from YouTube (another way to reset your password).
For Windows 7. When you turn on the computer, press F8 to open the following window:
Select with command line support.
After opening the command window, enter:
Thus, we copy the sethc file, where the administrator password is stored, so as not to lose it, because it will be replaced.
copy c:windowsSystem32cmd.exe c:windowsSystem32sethc.exe
With this command we replaced the password file with the command line.
We boot the computer in normal mode.
After loading, press Shift 5 times. cmd will open. Enter:
We will see the name of the main admin. If the administrator account is disabled, you can enable it:
If the name consists of two or more separate words, they must be enclosed in quotation marks.
Set a new key for the administrator:
net user admin username password
After this, restart the computer and enter the new key.
After a successful procedure, you need to return the sticky keys file to its place:
copy from: empsethc.exe from: windowssystem32sethc.exe
Resetting your password on Windows 8 and 10
For Windows 8, Windows 10. In these versions, the F8 key does not work. You need to create a bootable USB flash drive with your version of Windows. This was written about here, creating a bootable flash drive. Then boot through it, as described here.
After loading, select the keyboard layout and follow the path “Diagnostics” - “Advanced options” - “Command line”.
Then follow all the steps as in the case of Windows 7, which is described just above. The only difference is that instead of sethc you need to write utilman.
How else can you reset your password?
There is also a reset option using a special Microsoft miniPE disk. If you don’t have this at hand, you can download this utility on the Internet. Write it to a disk or flash drive and run it from there. The procedure for launching from external media was written here, loading from a flash drive or from a disk.
So, we can conclude that you can reset your password in various ways, depending on the access you have to the device. If you are its Administrator, then this will be much easier to do than for an ordinary user.
Thus, it is almost impossible to obtain the key; you can only reset it and replace it with a new one. However, nowadays almost everything is available. There are special spy programs for this. But using them is risky, as they can harm your computer: destroy some files, introduce malicious spyware.
To avoid all of the above problems, it is enough to simply create complex and at the same time memorable passwords.
Today, perhaps, every home has a computer, and often more than one. Like a smartphone, it is used not only for entertainment and communication, but also for work, often related to financial transactions. In addition, on a home PC, as a rule, there is confidential information, personal accounts of online banks, bank card data, and electronic wallets. Therefore, it is logical that access to such devices is not intended for outsiders, and is therefore password protected . Everything would be fine, but there are 2 problems associated with this:
- You might forget your computer password;
- the system may “fail” and refuse to let its owner in, even if he enters the correct password.
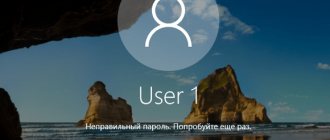
And if the first option is unlikely - after all, you use your computer every day, so it’s unlikely that you’ll suddenly forget your password, then the second option is just as likely. Owners of computers based on Windows 8 especially often encounter this problem, but there have also been cases on Windows 10.
Unfortunately, I was “lucky” enough to encounter exactly the second scenario - a laptop with an 8.1 system refused to let me onto the desktop, assuring me that the password I was entering was incorrect. Although entering the same password on another computer to log into my Microsoft account confirmed that I do not suffer from multiple sclerosis. The problem was eventually solved, and then I will tell you how. However, first I would like to give a brief overview of all the main ways to convince Mr. Gates' brainchild to let you into the workplace.