The areas of application of modern personal computer devices are varied and represented by a significant list. Devices are used everywhere. And if previously the boundaries of the regions were clearly demarcated, today the degree of interchangeability of devices has increased many times over. A common factor, in addition to the increased functionality of devices, both stationary and mobile, was the development, implementation and widespread distribution of the international computer network “Internet”.
Possessing the largest database of various types of data and the unique ability to provide, subject to appropriate conditions, unlimited access to the network from any device, the Internet has become the main platform for performing a wide variety of actions. Conducting professional activities, carrying out various business, educational, consulting procedures, social communication between users, official and private correspondence, creating, viewing, sharing and distributing various digital images and video compositions and much more on the Internet has become much faster and much more convenient , increasing the speed of data processing and transmission many times over.
Initially, connecting to the Internet involved the use of wired methods, but with the development of new standards and methods of remote data transfer, the widespread use of the network has risen to a significantly new level.
The main universal way to connect to the Internet has become a family of standards for a wireless protocol for digital data exchange over radio channels, represented by the general name “Wi-Fi” wireless local network technology.
The popularity of the wireless connection “Wi-Fi” has reached enormous proportions. In almost any public place and private home there is the ability to access the Internet via Wi-Fi, allowing you to access a variety of necessary information instantly from anywhere and on any device that supports a wireless connection. Many public organizations give away free Wi-Fi connections to increase the attractiveness of their establishments. But for private users, connecting third-party subscribers is undesirable, especially when such a connection is not authorized.
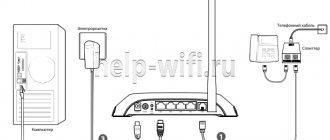
Using a Wi-Fi connection to access the Internet requires special equipment capable of processing, receiving and distributing the signal. And the most often used is a universal router, which comprehensively combines wired and wireless methods of accessing the Internet, and is capable of simultaneously servicing several different devices using different or the same network access.
To connect confidently through a router, it is enough to know the network account name and password previously set by the owner of the device. And if the credentials were transferred by the owner not only to trusted users, but also to third-party subscribers (friends or acquaintances for a one-time connection), then anyone who owns the remote connection data will be able to freely use unlimited access to the Internet from any number of third-party devices.
And if the owner of the connection wants to limit the access of third parties, excluding any devices other than their own or authorized ones, then the options presented later in our article can help him with this.
Signs of connecting other users
Sharing something with people around you is good, but only if it does not come to your own detriment. Each user connected to a wireless network takes on part of the traffic, and thereby reduces the overall data exchange speed. In other words: the more people connect to the router, the more the Internet slows down. Separately, it is worth noting the possibility of intrusion into the network by attackers conducting illegal financial or other types of transactions using your network address. This way they remain in the shadows, and all the troubles with the law will be transferred to you.
The main sign of parasitism on home WiFi is frequent and periodic blinking of the data packet transmission indicator. To check, disconnect all your devices from the router and watch the indicators. If the rapid blinking continues, strangers have infiltrated the network. An indirect sign may be a sharp drop in data transfer speed, especially if the drop occurs periodically over a long period of time. At the same time, there is a deterioration in the quality of the connection, glitches, and freezing of the browser.
Once you have determined that, in addition to your family and guests, your home Internet is used by strangers, you can safely begin blocking access for illegal devices. Below we have given several ways to disconnect other users from Wi-Fi.
Physical key(s)
Instructions for ASUS laptop here:
You can disable and enable Wi-Fi on a laptop using the key with a wireless network connection icon in the form of an antenna that distributes the signal. Older laptop computers have a special button. In most new ones, it is combined with one of the function keys F1 - F12.
To enable additional features (to use the second function of the button instead of F2), hold it down together with Fn. Typically, an icon will then appear on the display indicating the status of the wireless connection.
The laptop may also have a special button to activate the wireless module. Typically located on the side or top of the keyboard.
Disabling extraneous MAC addresses from WiFi
The most common option for protecting your own network is blocking Wi-Fi via MAC address. The method does not require the use of third-party software. All we need is a browser and a login with a password for the router.
We start in this order:
- In the search bar of the browser, enter the IP address of the router 168.0.1 or 192.168.1.1 and press “Enter”.
- In the authorization fields, enter the router's login and password. By default, they are of this type: “admin”, “1234”, “0000” (provided that you did not change the authorization data in advance).
- Go to the router statistics item called “DHCP Clients List” or “Status LAN”. Pay attention to the number of connected devices and their MAC address - these are unauthorized users (provided that all your devices are disconnected from the WiFi network).
In the router settings from TP-Link it looks like this:
- Go to the “Basic/WLAN Filtering” filtering settings, check the “Enable” box, select the “Blacklist” and enter the MAC address of the parasitic user. We confirm this with the “Submit” button.
In the TP-Link interface this is presented a little differently:
After clicking the “Enable” button, filtering will become active for blacklisted addresses and will block Wi-Fi from other users.
If desired, you can use a white list. The white list is created to store a limited number of addresses with access to the connection. This way you can block Wi-Fi from anyone with a new MAC. To do this, move the checkbox to “Whitelist” and add your MAC and your loved ones to the list.
Ways to determine who is connected to your Internet
There are two most convenient ways to identify an unwanted user.
In the router settings. Disconnect all your devices from the wireless Internet except your computer. Find out the IP address and MAC address of your computer. This can be done through the command line using the ipconfig command. The router address will be indicated next to the “Main gateway” item. It is often written on the device sticker, and the default login and password are also indicated there. Next, go to the router settings, enter the device address in the browser address bar, then enter your data. You will see the MAC addresses and IP addresses of all connected devices if you go to the “Clients” and “Statistics” sections.
How to view router clients:
- TP-Link. On the left menu, select the “Wireless Mode Statistics” section. Here you can see a list of connected devices. Through MAC Address Filtering, you can disable an unwanted user.
- Asus. The “Customers” circle is displayed on the main page. Click on it. A table will be displayed on the right where all clients will be listed.
- D-Link. Go to “Advanced settings”, then select “Station list” in the Wi-Fi item. There you can also disconnect the connection to a third-party MAC address by clicking “Disconnect”.
- Zyxel. Select the “System Monitor” section, go to the “Home Network” tab, and below you can see a list of devices.
Using the program. In order to determine who is connected to your Wi-Fi, there is a very convenient utility called Wireless Network Watcher. You can download it from the official website. Run the program directly from the computer that is connected to the router via a cable. The utility scans the network, identifying connected devices. Based on the results of the scan, their data and the name of the manufacturer will be displayed. After identifying dishonest users, they can be disabled through the router settings.
Find out if anyone is connected to Wi-Fi
Method one. Program. SoftPerfect WiFi Guard
This method is for those who do not want to bother too much and who will carry out diagnostics through a personal computer. To determine who has connected to the router, you will need the SoftPerfect WiFi Guard program. We find it, for example, through Google and install it. The program is in Russian and installs quickly. Minimum settings required.
In the “main” tab of the “settings” item of the program, we find the column “network adapter”. We select the item, in my case it is Qualcomm Atheros. Click "OK". Then click “scan” in the program window.
The program will show all devices that are connected to our Wi-Fi. If only you are connected, you will see two devices (the “Info” column), which will be designated as “This computer” and “Internet gateway”. That is, your computer and the router itself.
If there are strangers, the program will show them - neighbors’ devices will be displayed in red circles. This is either your neighbors or your other devices.
Method two. Router admin panel
This method does not require additional software. We go to the admin panel of the router. After connecting to the WiFi network, enter the IP address of the router. Typically this is 192.168.1.1. The address may be different on different models; you can check it on the device body. Then enter your username/password. As a rule, this is admin/admin (you can check on the device body).
This is where the difficulties begin. The menu may be different on different router models. On my device, in the “Status” tab we find the “Wireless” item. There is a sign with the MAC addresses of connected devices. If you are connected alone, then there is only one MAC in this table. There are other addresses - neighbors steal Wi-Fi. But it’s important - at this point you can get information about the devices that are connected right now.
More information can be seen in the “Interface Setup” tab, “DHCP” item.
How to turn off the mode using Windows
The Windows operating system has several different methods for disabling a wireless connection. Most methods require you to use System Settings, Control Manager, or Sharing Center. However, there is another fairly simple way - creating a shortcut with which you can quickly turn off Wi-Fi if it is not needed.
How to find out your Wi-Fi password on your phone
To do this, you need to carry out a set of certain actions:
- open the folder called “Network Connections” in the “Control Panel”;
- find the user access icon with the required name, on which you need to right-click and select “Create shortcut”;
- To deactivate the connection, you need to right-click on the shortcut and select “Disable”.
Important! For Windows 10, the presented method does not work.
There you can only turn on the Internet by clicking on the shortcut and selecting the appropriate button. However, if you need to disable it, the “Enable” button does not turn into “Disable”.
There is also a second method. It works by creating two special files with which you can quickly perform all actions. Thus, turning on the access point is done like this:
- It is recommended to create a text document on your PC desktop and name it with any name, but only using the .bat extension.
- After this, the document should be opened and a special launch command should be inserted into it. For example, if the network module is called "Ethernet", then the connection file is netsh interface set interface name="Ethernet" enable. Accordingly, you should write netsh interface set interface name="Ethernet" disable in the file to disable.
- When finished, you need to save your changes.
Option 1. Change the Wi-Fi access password
If you need to protect yourself from unauthorized connections of third-party users via a Wi-Fi wireless network, you can use an easy and guaranteed method, which consists of simply changing the user Wi-Fi network password on your personal router. After updating the credentials, any devices directly connected to this network, including all devices of the router owner that have permission to connect, will be forcibly disconnected. And to reconnect to the network, you will need to re-enter new passphrase values on all devices that require such a connection. A third-party user who does not have new login data will no longer be able to connect.
For some users who necessarily use a Wi-Fi network for many of their devices, such as a computer, laptop, tablet, smartphone, SMART TV and a number of other devices that have the appropriate ability to connect to the Internet via wireless Wi-Fi connection, the procedure of manually reconnecting each object may seem too tedious. However, of all the different options, changing your password is truly the only reliable way to ensure that third-party devices are disconnected from your “Wi-Fi” network.
Even blacklisting a specific device from your router to subsequently block its “Internet connection” leaves it possible to connect to your network from another new device using a known password. And if the password has been forgotten, there are various ways to recover saved Wi-Fi passwords on personal computers running the Windows operating system and other types of devices. Therefore, changing the passphrase will help remove any connections and provide network access only to truly necessary devices.
Changing the password for the Wi-Fi wireless connection is carried out in the settings of the network router, which can be accessed in a web browser by specifying the appropriate address in the address bar. Using their own credentials, the user must enter the settings management system, look for a section that often contains the words “wireless”, “Wi-Fi”, “Wireless” in the name and is responsible for assigning a specific name to the Wi-Fi network (which can also be change to any name of the user's choosing) and passphrase, and set new values. If it is difficult to find the corresponding section in the router’s web interface, users can use the device brand to find the manufacturer’s instructions with an official description of the characteristics of the parameters of all sections present. Ensure that secure encryption (WPA2) has been used and a strong passphrase has been set (avoid simple and common passphrases that involve a simple ascending or descending number sequence, such as "123456" or "654321", forward or backward sequences of letters, such as "qwerty", common and popular words or your own name). And once the changes are completed, the user’s network will become inaccessible to devices of third-party users who do not have the new password, and their subsequent connection will become impossible.
Where do “strangers” come from and what does this mean?
When strangers connect to your network unauthorized, this will definitely lead to a drop in Internet speed, because the channel now has to be divided among everyone, and its width is not infinite. Pages will load slower, video streaming will be slower, in general, not much pleasant. In addition, attackers can use special sniffer programs to intercept your data that you send to the Internet.
An unauthorized connection is a consequence of neglecting the protection of your network, when you do not set a password at all or set up entry-level protection - WEP encryption. What to do? First you need to find out who is connected to the network (to the router), then block all other people’s users, and then create serious protection for your network.
What to do if traffic is stolen?
There are many software tools that allow you to quickly and effectively solve the problem of how to identify and block an unauthorized WiFi user.
But this can also be easily done using the router itself, and there is no need to download and install additional software, so first we will describe methods using the web interface of wireless equipment.
In the case when the Internet provider is, for example, Rostelecom or Beeline, as well as other popular providers that often provide routers to their subscribers, then you should also use the device software.
The principle of operation is the same for all router models, and it does not matter which manufacturer released it, for example, Netis, Netgear or another.
The essence is always the same and is as follows: the instrument control panel has tools for identifying connected devices, and, most importantly, a convenient function has been implemented that allows you to block their access.
Methods for working with various equipment models are described below. Routers have their own software programmed into them, however, due to the lack of built-in means of input and output of parameters, all control is carried out through a PC or mobile gadget connected to them.
In order to enter the device settings, you need to take into account the features of its model, since the provider does not produce its own routers, but simply sells them, purchasing them from well-established manufacturers.
How to improve security?
Well, useful material? And which of our readers has encountered the fact that a neighbor has joined the Wi-Fi? What did you do? Share your experience, ask questions! Always happy to chat! Thank you for choosing us!
It is always better to call a spade a spade, so we can say with confidence that an outsider who connects to a Wi-Fi network without the knowledge of its owner is a thief. Such people should not be encouraged, but their actions should be stopped immediately.
Of course, you can diplomatically contact the “freeloader” personally and tell him not to connect to your Wi-Fi anymore, however, it’s no big secret what this will ultimately lead to.
Experienced specialists recommend using software methods to effectively solve the problem.
Netcut program
To cut people off Wi-Fi on a Windows computer, you can use a special program called Netcut. Although it was released in 2007 (and hasn't been updated since 2011), the program works great on all versions of Windows (we tested on Windows 8 and 10). The user interface of the program is reminiscent of the 90s.
Download Netcut from the official website and install it on your computer. You may also need another program called WinpCap. Don't worry, you don't need to do anything because the Wincap installation screen will be automatically displayed after installing Netcut.
After launching the Netcut program, you will receive a list of all devices (MAC addresses) that are connected to your Wi-Fi network. Select the MAC address you want to disconnect from the network and click the "Cut" button. This way you will disconnect the device from your internet. To regain access to the Internet, press the “ON” button.
pros
- Free program, easy to use and works on all versions of Windows.
Minuses
- The user interface is a bit outdated (doesn't look good)
Scanning with Wireless Network Watcher
To view devices connected to the router, you can use special scanner programs like Wireless Network Watcher from the NirSofer programmer. It is capable of displaying the IP and MAC addresses of users on the network. You will also be able to save this information as a report file until you decide to disconnect the person from your Wi-Fi. The software interface is initially in English, but can be easily changed with a separately downloaded localization tool.
To get started with Wireless Network Watcher, follow our tips.
- Download and install the free program from the official developer website https://www.nirsoft.net/utils/wireless_network_watcher.html.
- Download, unpack and copy the crack file “WNetWatcher_lng.ini” to the folder with the installed program.
- The working window of the program opens in front of us.
In the screenshot below we see the active router, as well as the computer and mobile device connected to it.
The utility provides information about the device manufacturer, its status, the date of the first and last discovery, and the number of recorded connections. What we are most interested in is the MAC address, which will be required to subsequently disconnect users from Wi-Fi via a computer in the manner described above.
Advantages
- Interface in Russian.
- Absolutely free software.
- Can scan wired and wireless network connections.
- It is minimized to a tray and used as a signal when new users enter/exit.
- Displays IP and MAC.
- Saves the scan result.
Flaws
- The crack needs to be downloaded and copied separately.
Solving the problem through the web interface of routers
It is necessary to perform the following sequential steps:
- Before starting the procedure, disconnect all gadgets from WiFi so that only the computer remains, through which you entered the device settings;
- Accurately determine the MAC and IP addresses of the PC (the easiest way to find this out is by running “ipconfig” on the command line). In the “Default gateway” column, look at the router address. Sometimes it is applied by the device manufacturer to a sticker located at the bottom of the device body (the name and code for logging into the web configurator are also written here);
- Upon entering the router interface, the “Clients” and “Statistics” tabs will display the addresses of devices connected to the router.
For TP-Link, the steps in the settings menu are as follows:
- Expand the “Wireless Mode” section;
- Next, go to “Wireless Mode Statistics”;
- A list of connected devices will appear on the monitor;
- Then, using the MAC filtering function, disable unauthorized users.
If you are using a D-Link model, you must first open “Advanced Settings” and then, moving to the “WiFi” section, enter the “Station List”. Here you can conveniently disconnect any address with one click on “Disconnect”.
For Asus, the setup steps are as follows:
- After opening the main menu, the user can immediately get to the “Clients” tab;
- When you enter this list, a complete list of connected devices will appear.
In the Huawei configurator, everything is also quite simple and comes down to sequential execution of simple actions:
- Click “Status”;
- Then click “LAN”;
- After that, go to the “Ethernet” tab;
- Examine the contents of the “LAM Side Device” section, which displays a list of all clients.
In the Zyxel web configurator, the algorithm consists of the following steps:
- Open the “System Monitor” tab;
- Next, go to “Home Network”;
- The list you are looking for will appear at the bottom of the screen.
Disabling and blocking freeloaders via the web interface
You can block access to Wi-Fi from the web interface of your router. Depending on which model you're using, the menu options may differ, but the steps are similar. Let's see how to disconnect other devices from Wi-Fi using a PC using popular routers as an example.
Asus
To disconnect users from the Wi-Fi network through the web interface of the Asus router, you need to:
- Open the “Network Map” section and click the “Clients” icon.
- Copy the MAC address of the device that we will block. After that, go to the “Wireless Network” section and look for the “Wireless Network MAC Address Filtering” tab at the top of the window.
- On this page, we allow filtering by checking the “Yes” box. From the drop-down list below, select “Reject”. Click “plus” to add the desired MAC address.
- Save the changes made. Now the blocked device will not be able to connect to your network.
If necessary, you can restore connectivity by simply removing the MAC address from the list.
TP-Link
To disconnect the user’s device from Wi-Fi on a TP-Link router, open the “Basic setup” tab and get into the “Network diagram” window. On it we see a list of devices connected to the computer and their MAC addresses. We identify and remember the address of the offender.
Now open the “Advanced Settings” tab, go to the “Protection” – “Access Control” section.
Set the switch at the top to the “On” position. To block devices, check the “Black List” box. In the list of connected devices, select the one you want to disable and click “Block”.
The device will be added to the black list. Save the changes.
The algorithm for other firmware versions is green and blue.
- Go to the “Wireless Mode” section, then “Wireless Mode Statistics”. We find other people’s devices in the list and copy their addresses.
- In the same section, go to the “Mac Address Filtering” item. Turn on filtering, add the device to the list and select “Deny access”.
D-Link
Open the Wi-Fi section and find the “List of Wi-Fi clients” section there. Here we identify an illegally connected client. Copy its MAC address.
After that, go to the “MAC filter” section. Set the value for the restriction mode to “Prohibit”. Click the “Add” button at the bottom of the page and indicate the MAC address that you want to block. Usually the shutdown occurs immediately. But you may have to reboot your router.
If you have the old interface, all operations are performed exactly the same in the same sections. Click on “Advanced settings” at the bottom of the page, go to the Wi-Fi – MAC filter section and configure the blocking.
Zyxel
Blocking freeloading neighbors from Wi-Fi is done like this. Enter the menu and open the Wi-Fi section. First, select the “Clients” subsection. Active connections to your wireless network will be displayed here. We look for a freeloader and copy his MAC address.
At the next stage, in the same section, open the “Blocking” item. Select “Black List” from the drop-down menu. In the MAC address field, enter the address of the client to whom you want to deny access. Click the “Add” button. Save the settings using the “Apply” button.
Keenetic
In the “My Networks and Wi-Fi” section, in the “List of Devices” section, we look for extraneous connections.
Then go to the “Network Rules” section, select “Wi-Fi Access Control”. On the “Home Network” tab, select the “Black List” blocking mode. Check the box next to the device you want to block.
After that, save the settings by clicking the button at the bottom of the page.
Huawei
We look at the list of connected devices on the Status – WLAN tab. To create a black list, go to the Basic – WLAN section. Open the WLAN Filtering tab.
Here we enable address filtering (check the Enable box) and select the blacklist. We add to it the device that needs to be disabled.
Rostelecom
To disconnect a stranger from your Internet on routers with firmware from Rostelecom, open the “Wi-Fi Client List” tab - DHCP. Here you will see a list of clients connected to your network. Next to the device you want to deny access to, click Disable.
To block someone else’s user and turn off their Wi-Fi, on the “Network” tab, go to the WLAN section, “Access Control List”.
Set the access mode to “Deny specified”. Enter the desired MAC address in the box below and add it to the list.
When to be wary
When someone establishes a connection with your router, the speed and quality of data transmission immediately decreases. Plus, there are financial risks and risks of confidentiality violations.
You can determine if someone is connected to your network by the following signs:
- Internet connection speed has dropped;
- After disconnecting all devices connected through the router, the router indicator lights do not stop blinking.
The owner of the network can view Internet traffic statistics at any time. It is freely available on the provider’s official website.
To track whether your network is actually being used by unauthorized users, all you need to do is:
- go to the modem settings, having first entered your login and password;
- open an item that displays devices that have access to your modem.
Find out the names of your devices so you don't get confused. They may have a serial number consisting of Latin letters and numbers, or a unique one (invented by you personally). If there is a problem with the names, then it will be easier to disconnect all home devices. The personal account data will be updated in 15 seconds, and only the devices of other users will remain there.
A special program - Wireless Network Watcher - can identify illegal users. It will quickly scan your network and identify users who were previously unknown to you. The main property of this program is that it is able to distinguish your devices from others. There will be no need to first disconnect them from the network.
Using a guest network
Sometimes there are situations when people have to provide temporary access to the Internet. In such cases, it is recommended to create and configure a guest network. In this way, it will be possible to create a separate access point that temporary users can use. However, they will not be able to connect to the main wireless network.
Thanks to this, you won't have to change her password. The fact is that a separate password will be created on the guest network, which is in no way connected with the main access point.
Guest network - allows you to provide temporary access to the Internet
People who are going to use the guest network will be able to configure it in the router settings. This is done as follows:
- Open the network adapter web interface on your computer or laptop.
- Go to additional settings and find the “Guest Network” section.
- In the menu that appears on the screen, find the “Wireless Mode” subsection.
- Set up a guest network.
During the setup process, you must specify the operating frequency. You also need to set the name of the access point. It can consist of both letters and numbers. In addition, you will have to choose a method to secure the new connection.
It is recommended to use WPA2 technology, as it is considered the most reliable.
After this, you need to come up with a strong password that will be used to connect to the guest access point.
Important Tips
Cases of illegal use of someone else's Internet are so widespread that many people do not even know that they are sharing their router network with other people. It’s even worse if these users conduct prohibited activities on the Internet, because they can easily avoid responsibility, unlike you. If you did not consent to this, then apply the above knowledge to block Wi-Fi from random parasites and unscrupulous neighbors.
In our article, we have given comprehensive information on “how to block people connecting to my Wi-Fi.” Use screens and scans to check the network. You can configure the router only through a browser and the interface of its own OS (described at the beginning of the article).
At the same time, we advise you to regularly change your Wi-Fi password to a more complex one. In order not to accidentally forget it, write down the combination on a piece of paper and store it in a secluded place - it’s banal, but simple and reliable. We do not recommend giving your wireless connection password to strangers. Sooner or later more people may find out about it and then you will have to change it again.
Possible problems and troubleshooting
Depending on which method you use to disable the wireless network, different problems may appear. Among them:
- The physical shutdown button (on some modems there may be no button at all) of the network device or the router itself does not work. Why this happens and what to do, read our other article at the link.
- Bugs in the software. It also happens that faults in the firmware interfere with the operation of some functions, including disabling the distribution of the Wi-Fi network through the control console. The problem is solved by updating the software version.
- Sometimes the router does not have the function of remotely turning off the Wi-Fi module: the required item is not in the settings menu. Then you will have to turn off the signal transmission using a physical button or removing the power supply from the outlet.
The reasons why you have to turn off your wireless network were discussed earlier. Depending on the specific circumstances, it will be more convenient to use one method or another.
Using special applications
Applications specially developed for this purpose are designed to quickly and effectively remove a parasite that has “attached” to someone else’s Internet from the list of clients.
One of the most popular utilities is Wireless Network Watcher. It is available for free installation on the developer's official source.
The application displays all devices connected to Wi-Fi. Once launched, the program can work in the background and display messages on the monitor about connected gadgets.
Another well-proven utility is “SoftPerfect WiFi Guard”.
Unlike the previous program, the possibility of stopping “freeloaders” from using other people’s Internet has been implemented.
The Netcut application was developed specifically for Windows PCs in 2007. Despite the outdated appearance of the interface, this program still works perfectly in the latest versions of Windows.
A free version of the application is available on the developer's website.
After installing it on your PC, you will need to complete the following steps:
- Run the program;
- Wait until the analysis is completed and the list of devices is displayed;
- Select the line with the “thief’s” address and click “Cut”;
- Ready.
If over time you need to unlock a device that has fallen out of favor with the network owner, you just need to click “ON”.
The developers of this utility also took care of people who do not have computers and created an application for Android gadgets “Pixel NetCut”. The utility is also very simple and effective to use.
Once you launch the application, you only need to perform a few steps:
- Touch “Scan”;
- Wait for the analysis to complete;
- Ready. The list of clients is already on the smartphone display;
- Next, click on the connection you are interested in. This will display information about it;
- Any device is blocked by simply switching the slider in the desired line;
- If over time you need to unlock a device that has fallen out of favor with the owner of the network, you simply need to set the slider to its previous position.
The name of the next utility speaks for itself about its purpose: “Who's On My Wifi”. Like all of the above, it is also freely distributed on the global web. Able to quickly display a list of devices connected to Wi-Fi.
Blocking technique
If the owner of the Wi-Fi network managed to see the list of connected devices, then blocking uninvited guests will no longer present significant difficulties.
This is done using the built-in MAC address filtering feature.
In some cases, the “thief” may be particularly persistent. If the attacker changed his address and immediately re-entered the WiFi, which is possible if he is not blocked by a new complex code, you can also simply deny access to all addresses except those on the router owner’s exclusion list.
For this:
- Open the “MAC Address Filtering” tab;
- Click “Enable” and check one of the sorting options. As stated above, selecting "Allow stations specified in included entries to gain access" is the most reliable.
How to disable everyone except the owner?
Many people ask how to disconnect all people from my WiFi and leave only their devices accessible. To do this, you need to know your MAC address. To get it on your computer, click Start, and then Run (Win + R). Type cmd. Enter the command ipconfig /all, and then press Enter.
The physical address is the MAC of the computer. As for the router, this data can be viewed at the bottom of the device.
To disable all users, go into your router settings and create a whitelist. Enter only your MAC address into it. After saving the information, all unauthorized users will be cut off. The blocking principle is discussed above (it differs for different WiFi routers).
Alternatively, you can use the applications discussed above. They also allow you to remove all third-party users via your computer or phone (if you have a mobile version) and leave only yourself.
Additional Information
As you may have noticed, when you execute the commands given in the instructions, Wi-Fi network filters are added to Windows. You can view the list of active filters at any time using the netsh wlan show filters command
And to delete filters, use the netsh wlan delete filter command followed by specifying the filter parameters, for example, in order to cancel the filter created in the second step of the second option, use the command
I hope the material was useful and understandable. If you still have questions, ask in the comments, I will try to answer. See also: How to find out the password of your Wi-Fi network and all saved wireless networks.
How to stop internet sharing manually
Let's start with a simple method that does not require any knowledge. To stop the router from working, you can use the physical on/off button, which is usually located on the back of the case.
Depending on the model and manufacturer, this key may be located in different places, and on some routers it is completely absent. If you cannot find the button you need, simply unplug the power cord from the outlet and turn off the power to the device. There is no need to worry about a malfunction, or about resetting any settings: everything will remain as it was.
This is the most commonplace option for how you can completely disable the router and stop distributing the Internet along with it. If you need Wi-Fi to work only for a selected list of devices or you need the router to continue working, distributing the connection using cables, you will have to use other methods.
The shutdown button itself usually looks like this: