Have you ever downloaded an executable file (.exe file) but were afraid to run it for fear that it might just blow up your entire system? You want to have a test machine, or better yet, a virtual PC on which to experiment with suspicious software, but you also don't want to build one from scratch. Microsoft tried to solve this problem with a new Windows feature called Sandbox.
What is a sandbox
Sandboxes reproduce at least the minimum functionality needed to accurately test programs or other code being developed (for example, using the same environment variables or accessing a database identical to that used by the stable previous implementation intended to change; many other capabilities, as specific functional needs vary greatly depending on the nature of the code and the applications it is intended for). The developers also offer alternative ways to use the sandbox features. For example, the Sandbox program.
What is a sandbox on a computer? The concept of a sandbox (sometimes also called a working directory, test server, or development server) is commonly built into version control software such as CVS and Subversion (SVN), in which developers "check out" a copy of the source code tree to examine and continue working on. Only after a developer has fully tested code changes in their own sandbox should those changes be checked in and merged into the repository and thereby made available to other developers or end users of the software. In computer security terms, a sandbox is a mechanism for running programs safely in an environment from which they cannot influence other programs and have limited resources to use.
Here are a few places where sandbox technology is used:
- Browsers like Chrome/Firefox use sandboxing to run pages/plugins/parts of pages like iFrames inside the sandbox.
- Network software – programs such as FTP have options for setting up Chroot. In this case, the user will be limited within the directory.
- Virtual machine - they emulate the entire OS in a sandbox.
- Linux Chroot – Linux systems have a chroot (change root) command in which the user can change the root from/to some subfolder like /mnt/new/root and hence all programs launched subsequently will process /mnt/ new/root as /. This way, all their actions are limited within the subfolder.
Whatever you want to do, Windows probably has software to make it easier. The only problem is that you cannot trust every download from free software sites or from an unknown developer. The reason for this is simple: the software you download on your PC may be unstable, come with adware, or may even be infected with a virus or malware. To deal with this, you can sandbox the application and try it out.
Microsoft has added a way for Windows 10 users to easily scan unknown apps without putting their PC at risk in the process. Once the sandbox instance is created, it acts like a clean installation of Windows, which only takes up about 100 MB of hard drive space. Simply create an instance, run whatever application you want to test, and exit the sandbox when you're done. Introducing the sandbox feature directly into Windows will certainly be a boon for corporate and private users who need to keep their PC running at all times. Microsoft hopes this will be an effective replacement for the process of setting up a virtual machine every time you need to test a new executable without the risk of harming your full Windows installation.
It is a lightweight virtual machine built on technologies used with Windows containers. It's a lightweight virtual machine that emulates Windows 10 installed on a PC using what's called a dynamic base image, a set of clean copies of files that can change and references to them. Therefore, the size of the sandbox virtual machine is only 25 MB if it is not installed, and will increase to 100 MB if it is installed. The software is similar to a regular application that you can search and find directly from the Start menu. When activated, it runs just like another virtual machine running on top of your current system, except that the sandboxed system is essentially a fresh new version of your main system. From there you can copy and paste executables and run them internally.
How to automatically run an application or script in Windows Sandbox.
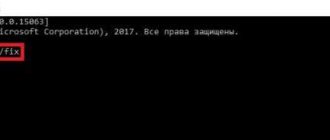
Sandbox also allows you to open an application (executable file) or script immediately after launch. To do this, in the .wsb configuration file, you must add this code:
command to call
Command: The command can be the path to any executable file or script available inside the Windows sandbox. This means that you can, for example, automatically open Explorer, Notepad or other system applications.
Note: Although very simple commands will work (running an executable or script), more complex scripts involving multiple steps must be placed in a script file. This script file can be mapped to a container via a shared folder and then executed using the LogonCommand directive.
How to install and configure sandbox
To install and use this great new feature in Windows, you'll need a computer that:
- runs at least Windows 10 Pro or Enterprise build 18305;
- 64-bit version;
- has virtualization capabilities in the BIOS;
- has at least 4 GB of RAM, 1 GB of free space and 2 CPU cores.
How to enable and configure Windows Sandbox:
- Click "Start", type "Windows features" and click "Turn Windows features on or off";
- Select the Sandbox checkbox in the Windows Features window and click OK.
Once completed, restart your computer and you're done.
Launch more than two windows. Peculiarities
Now we should look at how to run more than 2 windows in Sandboxie. To do this, you need to create new sandboxes in which you can open the necessary programs. This cannot be done in the free version of the program. After creating a new sandbox, trying to open a new window in it, the program displays the following warning on the screen.
In order to be able to open more than two windows in the sandbox, you must purchase the full paid version.
Why the sandbox doesn't work
First of all, make sure that virtualization is enabled on your system. You can find this out by going to the Performance tab in the Task Manager. If all the requirements are met, let's check if the KB4483214 update is installed. Apparently it breaks Windows Sandbox while trying to fix another error. Go to Installed Updates in Control Panel, right-click on the patch and uninstall it. Restart your computer and Windows Sandbox will work again.
How to use Sandboxie
Naturally, when thinking about personal safety and data security, users are interested in a number of questions related to Sandboxie - how to use it, what capabilities it has, what to do to remove the sandbox if such a need arises, etc.
We do a lot of things on the internet that put our identity, data and PC at risk. Sometimes we don't even realize that what we do can cause harm. If you surf the internet, watch cat GIFs, or try experimental software, you could be doing harm, no matter what you do on your PC. This is where Sandboxie comes in handy. Sandboxie lets you isolate programs, websites, and more so they can't make changes to your computer. Sandboxie is easy to use. To add a sandbox, open Manage Sandbox, click Sandbox, and select Create New Sandbox. If you decide not to restore the files, you can always view and run them in the sandbox later: open Control, right-click the desired sandbox and select Quick Recovery.
To install Sandboxie, go to the Sandboxie website and download the program. During installation, you will be prompted to install drivers for Sandboxie. This may seem like a strange ball request from such a program, but it is necessary for the problematic Sandboxie integration to work on your computer. You will also be alerted to software compatibility issues on your system. Review each one and choose to add settings to make them work in Sandboxie. If you don't plan to use these programs in Sandboxie, you can choose not to change these settings and move on.
When you first open Sandboxie, you'll be introduced to what the program does, its basic settings, and several features. Sandboxie looks like a primitive UI-based program, but its simplistic design allows it to focus on the background to isolate what you're opening. Click "Customize". Sandboxie allows you to have almost complete control over your system. You can create alert programs. They alert you when certain programs, processes, and more are opened outside of Sandboxie. This can alert you to malware and things opening up on your computer that programs can't detect. You also have full control over how Sandboxie integrates into the Windows shell. It allows you to add shortcuts, context menu shortcuts, and more. Experimental protection mode provides more granular protection settings for the 64-bit version of Sandboxie.
Now click "Help". Sandboxie can be a complex program, and the developers have created a variety of help files and documentation to help users get up to speed. It is recommended that even after reading our guide, you take the time to study Sandboxie's help files. Now click on Sandbox/DefaultBox. From here, you can name your sandbox, delete it, change settings, and even delete content or terminate programs running in it. Click "Launch Sandbox". From here you can launch a web browser, email reader, any program, Start menu items, or Windows Explorer process.
Click "Launch Web Browser." This will open your default web browser, such as Chrome. Sandboxie does not support full screen mode. While the program is surrounded by a yellow frame, it is in the sandbox. This protects the browser, program, or anything you open from making any changes to your operating system. If you go back to the Sandboxie window itself, you'll see the various processes involved in running the program. If something is malfunctioning or causing problems, you can abort the process by right-clicking on it and selecting End Process.
Click "DefaultBox" again, then click "Start Sandboxed Environment". Select "Run any program." Now you can go to any program in Windows and run it in the sandbox. You can even check the "Run as UAC administrator" checkbox to get full access to the program's features. If you select "Run from Start Menu," you can navigate through the rudimentary Start menu to open an item in Sandbox. Sandboxie also uses right-click commands to open any document, program, or other item in Windows in a sandbox. This is just the basics of how to get started with Sandboxie. The more you use Sandboxie, the more you'll see how it can protect your computer from unauthorized changes. Sandboxie offers a fun way to use programs and browse the web on your Windows computer.
How to remove a program
Despite the fact that the presented program makes it possible to run various applications in a virtual isolated environment and control all processes, some users have a desire or need to get rid of the Sandbox.
The question now is how you can completely remove Sandboxie from your computer. It is not so easy to do this correctly, since the program leaves behind a lot of traces.
Before proceeding with the uninstallation itself, you need to get rid of residual files. They appear when using the tool and can significantly clog up your computer. This preliminary cleaning will allow you to avoid manually cleaning the entire PC later.
In this situation the sequence will be as follows:
- launch Sandbox;
- all data requiring deletion is available in the sandbox list;
- You need to right-click on each of the objects;
- a context menu will open;
- here you should click on “Delete content”;
- then a window appears with the caption “Delete sandbox” and the specific name of the object;
- here you need to left-click and then click “Delete sandbox”;
- if no cleanup is required, the system will report that this sandbox is empty.
Next comes the standard sequential uninstallation procedure.
Usually it is enough to use the installation file, that is, find SandboxieInstall.exe and run it. In this regard, it is worth giving several recommendations:
- First make sure the program is closed. To do this, you need to open Device Manager.
- In the list of running processes, check if there is an exe file with the name of the tool to be removed.
- If it is there, left-click on the name once, and then select the “End task” option.
- You should also go to the section with startups and make sure that the current status of the program being deleted is displayed as “Disabled”;
- Hold down the Win and R keys at the same time. In the window that appears, enter the msconfig command, and then click “OK”.
- In the "System Configuration" section, select the "Boot" menu and check the box next to Safe Mode.
- Next click on the “Apply” and “OK” button.
- After this, the computer restarts, and the system is logged in in safe mode.
- Now you can run the installation file itself. After launch, click the “Next” button.
- A list of available options will appear. Here you need to select the “Delete application” option.
- After this, the automatic uninstallation procedure of all components will begin.
But that's not all. After completing the removal process, it would be a good idea to clean your computer of any remaining files:
- Here, first you need to open the Program Files section and look for folders and files called Sandboxie. If there are any, simply select everything found and send it to the trash.
- You should also press the combination of the Win and E buttons. An explorer window will appear, where you need to select “This computer” and go to drive C to the “Users” directory. Open the folder of the user under whose name the Sandbox tool was installed. There should be a hidden AppData folder here.
- There are several more directories inside the hidden folder. Each of them needs to be checked for the presence of sandbox-related files.
- By analogy, the hidden ProgramData folder on the same drive C is checked.
In addition to standard Windows tools, you can also use special programs to remove sandboxes. Among them, the best software developments are CCleaner, Revo Uninstaller and Reg Organizer.
Each tool has its own instructions for operating and removing programs.
Additional Information
This may be useful:
- Work between Windows and the sandbox is done through a single clipboard, with which you can easily transfer various files.
- You can only save data to Sandbox using a shared folder. This is due to the fact that after each shutdown of the environment, all information is completely cleared.
- Virtualization is the basis without which you won’t be able to run a sandbox.
- If you are encountering error 0x80070002 “The specified file cannot be found,” then it is likely that your system is not updated to the latest version. The problem was fixed in update KB4512941.
To summarize, I would like to say that Windows Sandbox is the best solution for those who want to quickly and reliably check the performance of a particular program. With it there is no need to download additional software for several gigabytes - everything is built into the system. It is enough to activate the sandbox, and it will appear in the list of programs.
The best sandboxes for Windows 10
A sandbox is a virtual environment in which you can install and run new or untrusted applications without harming your system. Here are some of the best sandbox apps for Windows from the many available.
BitBox
This tool is specially designed for browsing web pages in a sandbox environment. It comes in both Chrome and Firefox versions, and is pretty much a Linux instance of VirtualBox designed specifically for browsing, which means it requires a little more memory than other apps on this list. BitBox has the ability to download files to your actual PC, so it's important that you decide whether you want this to happen and configure it accordingly. It takes important precautions such as muting the microphone and monitoring all host-beatbox interactions, making it a reliable and safe choice.
BufferZone
BufferZone is a sandboxing tool that means that if you head to parts of the internet that could be dangerous to your PC, or someone hands you a flash drive that you don't really trust (this happens to everyone, right?) , then it’s worth running them through BufferZone. It's easy to add different programs to run through BufferZone, and every major web browser works well inside it. One advantage of the app over other software is that you don't have to do a lot of setup to get it up and running. By storing your selected actions in a secure virtual zone, BufferZone makes it impossible for malicious software over the Internet to infiltrate your computer because everything you do through it becomes read-only, so no malware can write its data to your hard drive .
Shade Sandbox
Shade Sandbox is another popular free sandbox app. Compared to Sandboxie, Shade's user interface is much simpler, clearer, and beginner-friendly. To sandbox an application, all you have to do is drag it into the Shade Sandbox window. The next time you launch the application, it will be automatically sandboxed. When using Shade Sandbox, all your browsing history, temporary files, cookies, Windows registry, system files, etc. will be isolated from the operating system. Any files downloaded while using Shade will be stored in the Virtual Downloads folder, which can be accessed from the Shade interface.
ToolWiz Time Freeze
ToolWiz Time Freeze works completely differently from the two sandboxes described above. When you install ToolWiz Time Freeze, it creates a virtual copy of all your system settings and files and saves the state of your PC. After using the application you want to test, simply reboot your system and it will be restored automatically. This type of application is very useful when you want to fully test the program without restrictions, but do not want it to make any changes to the OS.
Shadow Defender
Shadow Defender is similar to ToolWiz Time Freeze. When you install and initialize the software, you will be prompted to virtualize your system drive and any other drives you choose. Once the system has been virtualized, any changes made to it will be undone the next time the system is rebooted. Of course, you can always specify files and folders to exclude from shadow mode. This allows you to choose which changes to keep and which to discard. In shadow mode, if you want to save a downloaded file or commit a system change, all you have to do is click the Run Now button in the main window.
What all of the above applications do is commonly known as “lightweight virtualization.” That is, the applications you are testing still run on the host operating system, albeit in a limited way. If you want full virtualization, there is no better way than to create a virtual machine with the operating system of your choice in Virtual Box or VMware. If you already have experience with one of the described applications, or you use another sandbox, share it in the comments below the article.
Afterword
Oh yes, we almost forgot, of course, that the sandbox consumes an increased amount of machine resources, because it bites off (virtualizes) part of the capacity, which, naturally, creates a load that is different from running it directly. But, logically, security and/or privacy might be worth it.
By the way, the use of sandboxes, chroot or virtualization, partly relates to the anti-virus security methodology that we teach as part of our training packages.
That's probably all for now. As always, if you have any questions, thoughts, additions, etc., please feel free to comment on this post.