How to enable screen lock on Android
The Android operating system contains a whole set of functions for locking the screen. This is a pattern key, a digital PIN code, a multi-character password and even a fingerprint. To activate protection, you need to go to the OS settings, select the best option and configure it correctly. By default, the display lock is removed with a simple swipe. However, this method is considered unreliable because by swiping the screen, anyone can access the contents of the smartphone. Therefore, it is advisable to replace it with a more reliable and safe one.
Graphic key
This method of protection is the most common. Its essence lies in the use of a unique pattern that the user creates in a grid consisting of nine points. By connecting them in a certain sequence, he gets a drawing known only to him. To configure the key, you need to follow a simple algorithm:
- Open “Settings” of Android;
- Select the “Security” category;
- Go to the “Screen Lock” tab;
- Select the “Graphic key” option;
- Create a defensive combination in a grid of dots;
- Re-enter the key to confirm correctness;
- Choose a mode to display notifications on the lock screen.
To log in using this method, the system gives 5 attempts, after which it blocks access, which can only be restored through a Google account.
A graphic key is the simplest and most reliable protection option. To correctly identify a pattern consisting of only 4 positions, a fraudster will need to go through 1624 combinations, and from 9 points – 140704! It is estimated that the various connections of the dots contain a total of 389,112 compositions, and if you spend 1 second entering each of them, it will take 106 hours.
Fingerprint
To increase the security of data protection from theft on the vast majority of mobile gadgets of the latest generations, the protection functions have been supplemented with a new type - a special sensor for scanning a fingerprint. This method is completely reliable because the screen turns on only after the system identifies the unique papillary line pattern on the owner's finger. This option has a great advantage - you do not need to remember a password, code or graphic pattern. The only risk of using a scanner is breaking it (or losing a finger).
If your smartphone has a similar sensor, setting up protection will take no more than a minute. For this you will need:
- Open “Settings”;
- Go to the “Security and Privacy” section;
- Select the “Fingerprint” function from the list.
On the control page, you will need to activate the option by moving the slider to the right, and then create several fingerprint IDs so that the device remembers them and later allows you to turn on the device using them.
In order to increase the reliability of protection, you can connect any other locking option (password, code, pattern) in parallel with the scanner.
PIN code
Those who trust numbers more than complex patterns made up of dots will enjoy another locking method - using a four-digit numeric PIN. You can activate this protection method as follows:
- Enter “Settings”;
- Open the “Security” section;
- Find the category “Screen lock”;
- Select the “PIN code” protection option;
- In the special field, enter 4 digits in sequence;
- Re-enter the four-digit code for verification;
- Choose a mode to display notifications on the lock screen.
From now on, you can remove the screen lock only after entering your PIN code.
Password
Based on the number of combinations, this method is recognized by users as the most reliable. The password must have a minimum of 4 and a maximum of 17 characters. Taking into account the fact that in its compilation it is allowed to use mathematical signs, numbers and letters (in Latin or Cyrillic) in different registers, it is possible to create multi-million dollar combinations. Therefore, choosing the only correct sequence can be extremely difficult even with the help of special utilities.
To set a password, you should perform similar manipulations:
- Enter the settings menu, open the “Security” section, and go to the screen lock tab.
- This time select the “Password” option;
- Enter a unique combination in the special field;
- To confirm correctness, duplicate it again.
Finally, specify the option for displaying notifications on the screen.
Using the app
To activate the Lockscreen feature, Google offers many convenient applications available for download in the Play Store. You can configure protection correctly using the MagicLocker application as an example.
- Install and launch the program by tapping the icon on the desktop.
- After skipping several pages of information, go to the “Complete action using” page and select “MagicLocker”.
- Open the settings menu to select one of the protection options.
In addition to standard options (cipher password, pattern), the developer suggests using vibration or menu buttons. At the same time, it allows you to customize the lock screen theme as you wish.
Setting up locks
Locking can be configured using locking hints or the LOCK_TIMEOUT of the SET statement. These features are described in the following sections.
Locking hints
Lock hints specify the type of lock that the Database Engine uses to lock table data. Table-level lock hints are used when you need more granular control over the types of locks placed on a resource. (Lock hints override the current isolation level for the session.)
All lock hints are specified in the FROM clause of the SELECT statement.
The following is a list and brief description of the available lock hints: UPDLOCK
Sets an update lock on each row of the table during a read operation.
All update locks are held until the end of the transaction. TABLOCK
Sets a shared (or exclusive) lock on a table.
All locks are held until the end of the transaction. ROWLOCK
The existing shared table lock is replaced with a shared row lock for each qualifying row in the table.
PAGLOCK
The shared table lock is replaced with a shared page lock for each page that contains the specified rows.
NOLOCK
Synonym for READUNCOMMITTED, which we will look at when discussing isolation levels.
HOLDLOCK
Synonym for REPEATABLEREAD.
XLOCK
Sets an exclusive lock that is held until the transaction completes.
If the xlock hint is specified with a rowlock, paglock, or tablock hint, exclusive locks are established at the appropriate granularity level. READPAST
Specifies that the Database Engine should not read rows that are locked by other transactions.
All of these options can be combined together in any order that makes sense. For example, combining TABLOCK with PAGLOCK prompts does not make sense because each is used for different resources.
LOCK_TIMEOUT parameter
To prevent a process from waiting indefinitely for a locked object to be released, you can use the LOCK_TIMEOUT parameter in the SET statement. This parameter specifies the period, in milliseconds, that a transaction will wait for the lock to be released on an object. For example, if you want the timeout period to be eight seconds, then this should be specified as follows:
SET LOCK_TIMEOUT 8000
If the given resource cannot be provided to the process within this period of time, the statement fails and an appropriate error message is issued. A LOCK_TIMEOUT value of -1 (default) indicates no waiting period, i.e. the transaction will not wait for the resource to be released at all. (The READPAST lock hint provides an alternative to the LOCK_TIMEOUT parameter.)
How to change the blocking method
Sometimes, after a certain period of time, the selected screen lock option no longer satisfies the user, and he wants to replace it with another one. This is easy to do even for beginners. For this you will need:
- Open “Settings”;
- Go to the “Security” section;
- Select the “Screen Lock” category.
From the list of possible protection methods, select the best option and use one of the configuration algorithms suggested above.
For the development of intelligence
What if you don’t just look at the beautiful lock screen wallpaper, but also learn, for example, English at the same time. This is also possible when installing the Semper application.
It offers the user a set of puzzles for 3-5 seconds when the person unlocks the screen. To solve the puzzle you need to enter a word in English. This method allows you to memorize words much better and also promotes the development of cognitive functions. The effectiveness of Semper has been scientifically confirmed by researchers from the University of Potsdam. They found that learning in microblocks through puzzles allows you to remember information much more productively than with regular “cramming.”
The app has more than 50,000 packages with more than 50 languages. Semper independently adapts to the user’s level of knowledge, gradually increasing the complexity of the training program.
- Author: Elena
Rate this article:
- 5
- 4
- 3
- 2
- 1
(2 votes, average: 2 out of 5)
Share with your friends!
How to disable screen lock
The presence of one of the ways to protect a smartphone from prying eyes does not attract all users of mobile gadgets. For some of them, it causes inconvenience (it’s difficult to remember the code, the OS slows down when unlocking). The only way to fix the problem is to disable the function in the settings.
To disable screen lock, you need to follow this algorithm.
- Go to the general phone settings menu.
- Depending on the model, select the “Security”, “GPS and Security” or “Security and Privacy” section;
- In the “Screen Lock” tab, disable the option by selecting “No”.
From now on, you will be able to access the contents of the smartphone (system functionality and information) immediately after turning it on.
Display information about locks
The most important tool for displaying locking information is the dynamic management view sys.dm_tran_locks . This view returns information about the currently active lock manager resources. Each row in the view displays a currently active request for a lock that has been granted or is pending. The view columns correspond to two groups: resources and queries. A resource group describes the resources that are being locked, and a request group describes the lock request. The most important columns in this view are the following:
- resource_type - indicates the resource type;
- resource_database_id — specifies the identifier of the database to which this resource belongs;
- request_mode — sets the request mode;
- request_status - sets the current request status.
The following example shows a query that uses the sys.dm_tran_locks view to display pending locks:
USE SampleDb; SELECT resource_type, DB_NAME(resource_database_id) as db_name, request_session_id, request_mode, request_status FROM sys.dm_tran_locks WHERE request_status = 'WAIT;'
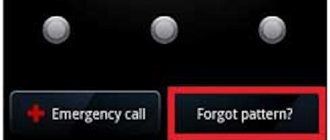
If you forgot your password or key
Users who frequently change screen lock methods on mobile devices often forget their password, code, and even graphic design. Therefore, they have difficulty accessing their phone. There are several unlocking options when such a situation arises.
Google Account Password
In most cases, after entering an incorrect combination of symbols or numbers five times, a window appears on the smartphone screen asking you to log into your Google account by entering personal identifiers. Typically, this method helps not only to unlock the phone, but also to change the password for logging into your own profile. If the protection was installed using third-party applications rather than built-in tools, this option will be ineffective.
Hard Reset
In this case, only rebooting the device will help - resetting the settings and restoring factory settings. During execution, all user data, contacts, SMS, applications, etc. will be deleted. The “Recovery” menu will help you implement this option. You can switch to this mode using the “Volume Down” and “Power” keys. Moving between options is done using the volume control carriage. The scheme is simple:
- Select the “wipe data/factory reset” or “Clear eMMC” or “Clear Flash” section.
- Run the command “yes – delete all user data” and wait a few minutes.
- After the process is completed, you will need to reboot the device by activating the “Reboot system” option.
An alternative to this method would be to flash the phone. But since this procedure is long and tedious, which, moreover, may be accompanied by some difficulties, it is advisable to contact a service center to complete it.
Automatic and controlled blocking in relation to typical 1C configurations
From time to time you have to understand the use of locking mechanisms in certain cases to implement various tasks. Although there is a lot of information on these topics, it is very scattered and over time the heap of material that had to be shoveled begins to be forgotten. We have to figure it out again...
As a result, the idea arose to structure and briefly outline the essence of the various locking modes in 1C in general and in relation to typical configurations. Hope this is helpful.
And so, let's go...
First, I will write about transaction isolation levels; I will briefly consider only those levels that are relevant to this article.
Transaction isolation levels
Read committed—reading of data in a transaction is allowed, changes to which have been completed by all other transactions. Default for most databases.
Read committed Snapshot (data versioning) - allowed to read the old version of data, changes to which have not been completed by other transactions. Natively supported by databases: Postgre SQL
and
Oracle
.
Starting from platform version 1C 8.3, it is implemented for working with databases: MSSQL
.
Repeatable read – prohibition on changing records in a transaction that have already been read previously as part of other transactions.
That’s all for now regarding transaction isolation; then I would like to say a few words about the mechanism for separating totals in accumulation registers.
Splitting accumulation register totals
The accumulation register at the database level consists of two tables: Main table
and
Table of totals.
When writing to the register (both for income and expense), data is written to both tables, the data is written directly to the main table, and the total row for the set of register dimensions is updated in the totals table. Accordingly, when parallel transactions are running, entries into the totals table for one set of measurements cannot be performed simultaneously, which reduces the speed of document processing.
To eliminate this problem, a mechanism has been created - separation of results.
Without going into details, this mechanism allows you to update data in the accumulation register totals table for the same set of dimensions,
simultaneously
.
Let's move on...
To reveal the main topic of the article, I will need to describe the general principles of residue control mechanisms that are used in typical configurations. In short, there is an old and a new control mechanism, both of which are currently in use, despite the fact that the new regime is already about 8 years old.
Mechanisms for controlling residues in standard 1C configurations
Old scheme, hereinafter OLD
– a query is generated to the database to perform control of free balances; in case of a positive decision, a movement is generated through the register. Currently used in Accounting 3.0 and in some algorithms UT 11, KA 2, ERP 2.
Flaws
:
- it is necessary to block records that are involved in the movement already at the moment of reading them, which worsens the parallelism of work.
New scheme, then NEW
– movement through the register is performed, then the presence of negative balances is checked; if they are present, the operation is rolled back. Currently used in UT 11, KA 2, ERP 2.
Advantages:
- there is no need to delete document movements in a separate operation; the data is overwritten without first writing empty sets. This seriously increases the speed of document processing.
- The speed of executing a query for balances has been increased, since in most cases, the query after execution produces an empty result.
- There is no need to pre-lock mutable data.
Flaws
:
- if in order to carry out the posting it is necessary to obtain data from accounting registers (for example, calculating the cost for write-off), in any case it is necessary to block the records already at the moment of reading them.
Summarizing what was written above, we can conclude that if to process a document you do not need to make additional queries to the database registers, it is better to use a new mechanism; if necessary, we use the old mechanism.
Well, it’s time to move on to presenting the main topic of this article - a description of blocking modes
.
In fact, there are only two modes: Automatic
and
Controlled
, they are indicated in the general configuration properties, I am sure that everyone knows this very well, so I will not dwell on this in detail.
You probably already guessed that you need to work with these two modes differently in relation to different document processing mechanisms. Let's look at this in more detail.
Automatic locking mode
In this case, the transaction isolation mode described above is used: Repeatable read.
Note:
this article discusses primarily the client-server version of work.
For file mode, an even higher isolation level will be applied, which we will not consider here. To avoid deadlocks when posting documents with balance control - OLD
FOR CHANGE
query language design is used , which allows, when reading data for the first time in a transaction, to impose on this data not a shared read lock, but an update lock.
Accordingly, it will no longer be possible to perform a similar procedure in another transaction, since it is impossible to impose two update locks from different transactions on the same data
.
The lock is applied only to those records that appear in the query (in the worst case, if the query plan is not optimal or is written incorrectly, more records than necessary may be blocked).
Note:
When working with a file database and P postgre SQL , the lock is applied entirely to the entire table.
Example:
SELECT Remaining Products.Nomenclature, Remaining Products.QuantityRemaining AS Quantity FROM Accumulation Register.Remaining Products.Remaining AS Remaining Products FOR CHANGE
Use balance control mode - NEW
together with the automatic locking mode it makes sense only for registers without separating the totals, in this case, no additional actions need to be taken.
a d ea dlock
may occur when reading data if the register was written to simultaneously, and this problem cannot be solved in any way.
Controlled blocking mode
In this case, transaction isolation modes are used: Read
committed
and
Read committed Snapshot
.
Using OLD
— the shared lock is released after reading the balance data, therefore, in order to exclude the possibility of negative balances, it is necessary to explicitly lock the necessary entries in the register before generating a request for obtaining balances. Actually, this is the principle of the controlled blocking mode.
Example:
DataLock = NewDataLock; Locking Element = Data Locking.Add("Accumulation Register.ProductsInWarehouses.RecordSet"); Lock Element.SetValue("Warehouse", Warehouse); Locking Element.SetValue("Nomenclature", Nomenclature); DataLockElement.Mode = DataLockMode.Exclusive; LockData.Lock();
Using Residue Control Mode NEW
:
In the case of using registers without dividing the totals, additional locks to those imposed by the database are not needed; the DBMS itself will lock the necessary data (in this case, records in the totals table of the accumulation register).
In the case of using accumulation registers with separation of totals (by default, registers with this flag are created for the configurator), the following negative situations can occur:
- Without versioning mode (MS SQL and 1C 8.2) – we will get a deadlock when trying to read data if the write in two transactions was performed simultaneously. When writing data, blocking will not occur, since different DBMS rows are used (separation of totals)
- With the Snapshot versioning mode (postgresql, oracle or 1C 8.3), blocking will not occur, but negative balances will appear, since control will be performed without taking into account all uncompleted transactions.
To avoid this situation, you must set the record set flag before writing to the register: BLOCK FOR CHANGE
. This design gives a command when writing to apply an exclusive lock on records of the register remainder table without taking into account the total separator; in essence, it simply temporarily disables the division of totals for the accumulation register.
Accordingly, the possibility of parallel writing to a data register with a similar set of measurements is excluded; a later transaction will wait for the completion of the previous one.
Example:
RecordSet. BlockForChange = True;
I hope this article was useful, and after reading it, a more holistic understanding of the operation of the 1C platform under various blocking modes is created, using different mechanisms for controlling balances.
If I missed something or was inaccurate in some way, I will see it in the comments to the article.
A special thank you if you mark the article with an asterisk, since nothing motivates you to write new articles more than your approval J
Bonus: TOP best screen lock apps
Many owners of mobile gadgets running Android OS try not to use built-in tools, but resort to the help of third-party blocking programs. Along with standard tools, such utilities offer users many other additional functions, such as changing the theme on the lock screen, the ability to select an image from the gallery to change the screensaver, etc. The rating of programs that, according to reviews, are easy to use and The following are popular.
| Application | Characteristics and description |
| Smart Lock Screen | The free program protects user data and allows you to customize the lock screen. It also allows you to:
|
| SnapLock | An Android application that simplifies the lock screen experience and turns it into an original and convenient tool. Among the advantages of the utility:
|
| ZUI Locker | A beautiful application and at the same time an alternative screen lock option. Users praise it for its convenient security settings and a huge variety of thematic functions. After installation, the program requires the provision of some user rights. To replace Locrscreen and allow access to notifications, you must follow the instructions. After completing the process, the standard screen will acquire an attractive appearance and original design. The application has one design feature - when you tilt the smartphone, the picture set as wallpaper begins to shift to the side. |
4.5/5 — (26 votes)
Lock granularity
Lock granularity determines which resource is locked in a single lock attempt. The Database Engine can lock the following resources: rows, pages, an index key or range of index keys, tables, an extent, the database itself. The system selects the required blocking granularity automatically.
A string is the smallest resource that can be locked. Row-level locking also includes both data rows and index elements. Row-level locking means that only the row accessed by the application is locked. Therefore, all other rows of this table remain free and can be used by other applications. The Database Engine can also lock the page that contains the row to be locked.
Clustered tables store data pages at the node level of the (clustered) index structure and therefore use index key locking instead of row locking.
Units of disk space called extents, which are 64 KB in size, can also be blocked. Extents are locked automatically, and as a table or index grows, additional disk space must be allocated to it.
Blocking granularity affects concurrent concurrency. In general, the higher the level of granularity, the more the ability to share data is reduced. This means that row-level locking maximizes concurrent concurrent access because it locks just one row of the page, leaving all other rows available to other processes. On the other hand, a low lock level increases system overhead because each individual row requires a separate lock. Page and table level locking limits the level of data availability but also reduces system overhead.
Why might you need to disable the touchscreen?
The simplest option that comes to mind is random clicks. For example, when listening to music or watching videos, they cause the track to pause or rewind, and some smartphones can still suffer from “ghost” clicks, when the screen responds to touches that you don’t actually make. This often happens when you take a photo or video, for example, in the rain. If you have other options in which disabling touchscreen would be appropriate, write about them in our Telegram chat.
Reset via iTunes
Now let's look at how to disable the screen lock on an iPhone using two programs. If the user cannot remove the lock screen, they should use a PC. First you need to press the key combination “Shutdown" and "Home". Then you need to release the “Power Off” button, but still hold Home. Only iTunes can recognize this mode, so the external state of the phone will not change.
After this, you can connect your smartphone to your PC and open the iTunes program. On your keyboard, click on the Shift key and at the same time click on the “Restore” item in the program. Next, the updated version of the operating system will be downloaded, and the password will be automatically reset. It is important to know that all user files will be deleted. It is recommended to make a backup before performing this operation.
In what cases is it necessary to lock your Android phone?
Locking a device is only necessary if important data is stored on the phone and the owner has no hope of finding the gadget. If you hope that the missing smartphone will still be found, then first of all you need to call it. If another person discovers your device, there is a chance that he will pick up the phone and be able to negotiate with you about the possibility of return.
Once your device is locked, you will no longer be able to call it. But in this case, all your data will be under reliable protection, since it will simply be deleted. True, this does not apply to information stored on the memory card.
Why set a password?
Before setting a password for Honor applications, make sure this step is necessary. For security, it is recommended to set entry restrictions for the most important utilities. After starting the smartphone and unlocking the screen, you will have to enter a password to log in. As a result, it is possible to protect confidential information and prevent unauthorized persons from accessing your software.
Such protection must be placed on Honor in the following cases:
- the utility contains information that cannot be seen by anyone;
- the phone is sometimes used by other people;
- there are children in the family who can take a smartphone without asking;
- the mobile device is periodically left unattended, for example, at work.
Knowing how to set a password for the Honor application, you can protect confidential information at any time. The choice of protection method is up to the owner, but it is better to give preference to standard methods. They are more reliable, and the likelihood of them being bypassed is minimal. Third-party utilities have more vulnerabilities and are easier to hack if necessary. In the comments, share which protection method you use and why.
Xiaomi and MIUI
It also makes sense to consider a way to disable blocking on Xaomi devices, which has its own personal shell. Therefore, to do this, you need to do the following:
- Simply swipe down and then find the settings icon. The same can be done if you first go to the program menu, and then click on settings.
- Since the models of this company support unlocking using fingerprints, you must select the appropriate section. It will be labeled as "screen and fingerprint lock".
- After that, we find a line that suggests changing the phone screen lock. In fact, in the menu that opens, you will need to find the screen lock.
- In the menu that opens, you will need to enter the corresponding PIN code numbers. Once you have entered it correctly, you must confirm it.
- Then a line opens that allows you to disable the blocking. We'll need to click on it. Once you do this, the system will ask you to confirm that you really want to leave your smartphone unprotected. Just click on the appropriate button and save all the settings.
Auto-lock on iPhone
The screen is the main energy consumer in a smartphone. When choosing maximum brightness, the user should know that the battery charge will last for a maximum of 6 hours. Automatically locking the display can solve this problem. Every iPhone has this function that is responsible for this process. The user will need to open “Settings” and click on “Display and Brightness”. Then you need to tap on the “Auto-lock” button.
The system will offer several time intervals, after which the screen will turn off. The user should select “Never”. As a result, the phone screen will not turn off on its own - only when you press the “Lock” button.
Reset via iCloud
To do this, you will need an Internet connection via Wi-Fi. Then you should take another mobile device and go to the ICloud website on it. Next, you need to go through the authorization procedure and open the “My Devices” section. It is worth making sure that the “Online” mode is set in the context menu opposite the “iPhone” icon.
Then you need to click on the name of the device and click on “Erase iPhone”. The system will require you to enter your Apple ID password. The device will begin the recovery process and reboot. It is important to know that resetting your password will deactivate the Lost iPhone feature.
What to do if the change is prohibited by the administrator
It happens that you did everything correctly, but the system does not allow you to change your password, because this function is prohibited by the administrator. In this case, you will need to do the following:
- Go to the settings section and select the line labeled “device administrators”.
- After we have switched to this tab, we need to check the box next to the line “Android remote control”.
- Then a list of powers will be displayed, including disabling the screen lock. Click on it, and then turn off the phone’s protection.
All methods of disabling blocking are relevant only for those systems and versions of the operating system that are presented above. Often the first version of Android is no longer used, so it is pointless to consider it. In any case, using the settings menu and knowledge of the current PIN code or pattern, you can remove the protection in literally a matter of seconds.
Check the number you called from
There are several ways to unlock your phone. The choice of one of them depends on the type of personal data protection established. How to remove screen lock on Android - detailed step-by-step instructions.