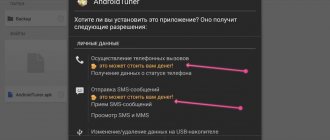
A Trojan is a type of virus. Hackers develop these types of malicious applications under the guise of useful programs. As soon as they arrive on the user’s computer, they are immediately embedded in startup, making it impossible to enter the task manager or registry editor. Windows begin to pop up, notifying the user that access to this application is blocked or disabled.
It is very important to know where these types of viruses are located so that you do not accidentally download them. Hackers prefer to post them on public resources with a wide audience. Each browser has its own vulnerabilities, thanks to which the virus penetrates the PC. We can say that no one is protected from the Trojan, which is why so many programs have been developed to destroy it.
It is urgent to take action, because... anyone who has gained access to a computer can steal personal data, including passwords for bank cards and classified materials.
How to remove a Trojan
Consequences of negative impact
When the Trojan penetrates the system, strange things begin to happen:
- USB connectors stop working;
- The system reboots itself;
- PC performance slows down as if something is consuming most of the resources;
- The language layout does not switch;
- The browser opens pages slowly, and some do not load at all;
- A notification appears on your desktop that blocks all your actions and asks you to send an SMS to remove the restriction.
These are just some of the unpleasant consequences of viruses entering Windows.
Signs of infection
First of all, it is necessary to recognize this virus in time. You should be wary if you encounter some of the following signs:
- the inability to display some pages on websites, although before this everything worked properly, these pages could be opened;
- the browser is slower, it freezes and stops responding to requests;
- the home page that the user set or was the default suddenly changed to another;
- an error appears when trying to access antivirus developer sites;
- if you want to visit a specific site, the browser redirects to another source of information;
- When working, advertising windows, intrusive messages and banners often pop up;
- new toolbars have appeared in the browser that the user is used to, although it did not exist before;
- When you turn on the computer, there is no response to requests, the PC freezes or simply turns off. Self-rebooting should also be a concern;
- the appearance of new icons, unknown files and applications;
- Frequently pop-up messages about system errors.
The computer is infected with viruses
Disk formatting
This path is undesirable for most users because all data on the media will be deleted. But sometimes this is the only way to save the situation.
If viruses are firmly entrenched in the system, then it is easier to format everything and reinstall the OS.
I recommend starting with other methods.
Stopping malware with RKill
Using “RKill” you can stop malware from running on your computer. This will help you in the future, using another antivirus, scan your computer and remove viruses that can no longer resist such a process. The specified program itself is not intended for removing viruses. Therefore, please note that after “RKill” has completed its work, do not restart the computer, as the “muffled” viruses will begin to operate again.
Do the following:
- Download “RKill” from here and run the utility
- Wait while the program scans your computer, checking for active malicious processes. If it detects any, it will automatically terminate their work without your participation.
Stopping malware with RKill
- As a result, you will see the window shown in the screenshot. There will be a report here. We remind you that you cannot restart your computer after this. Now you should proceed to the next step, which we will describe below.
Stopping malware with RKill
Full scan
As soon as you suspect something is wrong, you should use the installed antivirus and run a thorough scan. This may take several hours and will help remove malicious code from your computer.
Attention! It is advisable to perform this procedure in safe mode! To enter it, press F8 on the keyboard while Windows is loading. A menu will appear in which we select the appropriate item.
After starting the OS, most drivers and network services will not be enabled, which will allow you to conduct a full scan and get rid of the “disease.” In addition, anti-virus software will gain access to resources that would normally be blocked by Trojan software.
How to protect yourself from Trojans getting onto your computer
Trojans can mainly get onto a computer via the Internet. In rare cases, this happens through external storage media. Most often, it is the user himself who is to blame for infecting the PC with viruses. It may even lead to a complete reinstallation of the system with the loss of important documents.
What are computer viruses, Trojans and worms, and what is their difference?
To avoid such problems, you need to follow simple rules:
- Do not open suspicious sites/emails that talk about winning something valuable. Letters demanding payment for something.
- Use antiviruses from Russian companies, for example, such as: Kaspersky and Doctor Web (but they will work in full force only if a license is purchased , then the antivirus will be able to fully protect the computer). Since Western companies do not deal with Trojans that do not appear on their territory. Most often, when a PC is infected with a new virus or Trojan, defenders simply mistake the virus for a regular, non-malicious file, because it is not in the database.
- Make backup copies to removable media. Configure periodic creation checkpoints . Thanks to this, it will be possible to roll back the system to a point when the computer is not yet infected. And you can restore files even after reinstalling the OS.
Removing processes from startup
Open the “Run” console (Win + R) and enter the command:
Msconfig
After the settings window appears on the screen, go to the “Startup” tab and uncheck the boxes next to suspicious items. Here's an example:
Eliminate everything that you did not personally install. If in doubt, go online from your Android tablet (or any other device) and search for a suspicious line to find out its purpose.
I have already written many different articles on the topic of treating viruses, you can take a look there, maybe another method will work better.
We should also mention the Artemis virus, which copies its files to disk and then begins to duplicate them. Thus, free space begins to run out quickly. Most often, the Trojan only affects Win32-based systems.
In autorun its process is called (randomname).dll. If you come across anything like this, delete it without hesitation.
Standard antiviruses
New versions of viruses appear faster than protection against them.
Therefore, it is important to always have a good anti-virus program on your PC with updated virus databases. Well- proven antivirus programs:
- AVG AntiVirus Free;
- Avira Free Security Suite;
- Bitdefender Antivirus Free Edition;
- 360 Total Security;
- Kaspersky;
- Windows Defender (in Windows 10);
- Web.
They all protect your computer well. But they all have their weak points. And you need to be prepared for anything and be able to use at least one antivirus to search for Trojans. For example, Kaspersky:
- Let's launch Kaspersky.
- Go to “ Scan ”.
- Launch "Full Scan».
- If malware is detected, we remove it .
But even the best paid antivirus does not protect the system 100%. In addition to scanning the system with antivirus software, you also need to improve your computer literacy. Do not download files and programs from unknown, unverified resources. Do not download suspicious files sent by unknown recipients by email.
Disk Cleanup
I highly recommend clearing all files that are associated with restore points, as they may contain malicious code. Also, it is worth deleting temporary files in the Temp folders and viewed browser pages. You don't have to use the command line. Any third-party software is suitable for this purpose: Wise Care 365, CCleaner.
How does a virus or Trojan manifest itself in a production environment?
- Your computer periodically freezes or restarts
- Your PC or laptop is terribly slow
- USB ports are disabled
- Switching to the English keyboard layout stops working
- Internet pages open slowly
- money disappears from webmoney or other Internet wallets
- an iframe with a virus is added to your sites in index.php or index.html
- Incomprehensible adult-themed banners have appeared that are impossible to get rid of
- the virus infected the flash drive
- after booting the system you see a blank desktop
- or worse, the ransomware asks you to send an SMS to gain access.
All of the above problems occurred on my computers and on clients’ computers, but the problem was solved quite quickly after reinstalling Windows and formatting the hard drive.
It seemed to me that this is not the best option for fixing the problem, and now I want to share some points that will help rid your PC of all dirt. I hope that you have at least some kind of antivirus program, it could be Nod 32, Dr.web, Kaspersky, or the free Avast program. If you don't have access to WINDOWS. In this case, we will need a boot disk with which we will get rid of malware. Read how to do this and how to fight. If you don't have access to social networks. You cannot access the social network VKontakte, the virus requires confirmation via SMS, we will solve this issue in a separate topic. If you have access to Windows. Let's start cleaning.
First of all, you need to run your antivirus program and completely scan all hard drives for threats. It’s better to do this in safe mode, but before that I would recommend running “Loading the Last Known Good Configuration”; perhaps you don’t have a virus at all, but there was a failure in the system.
To enter WINDOWS safe mode, you must press the F8 key before loading the operating system, and a menu will open on your monitor in which you must select “Safe Mode.” If everything is pressed correctly, the following picture will be shown on the screen. Here you can also try running “Last Known Good Configuration”.
After selecting the desired “Safe Mode” item, WINDOWS will load, but most drivers and programs will not start, which will help you thoroughly check all files for viruses. The fact is that in normal mode the Anti-Virus program is unable to scan some files that are currently used by Windows.
Which utility can I use to check my system for viruses?
If checking with installed antiviruses does not bring the desired results, download the free Drweb Cureit utility and check the system again, preferably in safe mode. If you are cleaning the system, you will definitely find something.
Cleaning Startup.
To further clean the system, go to Start->Run and in the window that appears, enter the word “msconfig”. The System Setup program will launch on your screen. Go to the “Startup” tab and pay attention to the suspicious objects marked with a checkmark. Pay attention to the picture, in this case I highlighted the viruses that were loaded during boot.
Suspicious lines and their examples:
- C:WINDOWSINF*.exe
- %windir%system328353.exe
- Blank lines, but with a checkmark
- %windir%system32smhost.exe
- C:WINDOWSsecuritysmss.exe
- * means all files in the folder
In approximately this way, you can find out the loading of a suspected object. If you are sure that you have not installed a program that is in the list of objects, then immediately uncheck the box. Cleaning other objects
And that’s not all, for a more thorough disk cleanup, you need to delete all system recovery files, the folder with which various viruses and Trojans often end up, delete temporary Internet files, and also clean the temp folder. In principle, to clean your computer of any debris, you can use a special program, such as CCleaner.
Deleting hard drive recovery files.
Click on the icon on the desktop My Computer->Properties, and go to the system recovery tab. In the window that appears, select “Options” and move the slider to 0. After cleaning the entire system, the slider can be put back in place.
Scan your system for spyware and other malware.
We also do not forget that the so-called spyware module can penetrate the computer’s hard drive. In principle, any antivirus now catches them, but it still doesn’t hurt to use a program, for example Ad-Aware. Also try using the small utilities AVZ and Hijackthis, which in any case will be useful for removing other spyware and malware.
If your Desktop does not load, you can try running any program through the Task Manager. You can open it by pressing the key combinations ctrl+alt+delete and open it in the menu, File->New task->Browse. Conclusion
I think that all these recommendations will help you get rid of the dirt in your system, from which attackers are trying to make money, but if you have any problems, write, I will definitely help you. The archive contains 5 programs discussed in this article. Don’t get sick.
How often do you encounter viruses? On my personal PC, such problems do not arise, thanks to reliable security software, but friends often ask how to remove a Trojan virus from a laptop or desktop computer. In this article I will talk about the simplest methods that every user should know.
I have been working in the computer industry for several years, and during this time I have eliminated hundreds of malicious utilities. Sometimes even the most sophisticated antivirus is not able to solve the problem. You have to use specialized software specifically for each situation. Often built-in applications and Windows features come to the rescue.
THE CONTENT OF THE ARTICLE:
Table of tested anti-spyware programs
So what was tested and with what results we can finally see below. All programs were tested simultaneously to find malicious spyware before they were removed.
As can be seen from the table above, neither the built-in Windows Defender from Microsoft nor the domestic AVZ4 can boast of good results.
Winners - Best Anti-Spyware Software
Our winners were 2 programs:
- SUPER AntiSpyware (6th place in terms of downloads in the world) and
- Malwarebytes Anti-malware (1st place in downloads in the world, 3rd place in downloads, comss.ru)
Both programs complement each other. When SUPER AntiSpyware finds 1 type of spyware, Malwarebytes Anti-malware does an excellent job of dealing with other types.
Links to download anti-spyware programs
For those who want to test the main players in the anti-spyware market on their computer, I offer direct download links from my website:
| № | Logo | Link | Anti-spy |
| 1 | Malwarebytes Anti-Malware Free | ||
| 2 | SUPER AntiSpyware Free | ||
| 3 | AVZ4 Antiviral Toolkit | ||
| 4 | Spybot 2.2 Free | ||
| 5 | Spybot 1.6.2 (old version) Free | ||
| 6 | Windows Defender |
How to get free help removing spy/rootkit/virus
I want to immediately emphasize that the AVZ4 program is nevertheless a very useful tool for cleaning your computer from all sorts of nasty things. There are forums https://virusinfo.info, https://www.cyberforum.ru, which will help you if you have viruses or spyware.
On such specialized forums, you will most likely be asked to install the AVZ4 and/or HijackThis program (from Trend Micro). Then, following their instructions, you will do a mini-scan of your computer and post the results to the forum. This will allow the guys to better understand how to help you.
The use of the AVZ4 program is also necessary as the winners of this review.
Why Trojan?
The Trojan virus got its name in memory of the siege of Troy, a great city in Ancient Greece. The Greeks besieged Troy for 10 years, but were never successful. In the end, the Greek Odysseus came up with a wooden horse, inside which selected Greek paratroopers were hidden.
The simple-minded residents of ancient Troy decided that the Greeks had left them a horse as a gift and dragged it into the city. This is how the history of the Trojan civilization ended. Let's not dwell on history for a long time. And this virus also pretends to be useful, but in reality it brings trouble.
Should I pay the ransom?
It is generally not recommended to pay the ransom . As with the no-negotiation policy in a real-life hostage situation, a similar approach should be taken when “capturing” data. Paying a ransom is not recommended, since there is no guarantee that the ransomware will actually fulfill its promise and decrypt the data. In addition, receiving a ransom from criminals will encourage the commission of this type of crime, and this should be avoided at all costs.
If you do plan to pay the ransom, do not remove the ransomware from your computer. Depending on the type of ransomware or the cybercriminals' plan to decrypt the data, ransomware may be the only way to use the decryption code. If you remove the ransomware prematurely, the decryption code purchased at a high price will become useless. But if you did receive the decryption code and it worked, you need to remove the ransomware from the device as soon as possible after decrypting the data.
What else is on the market?
The following programs are familiar to me only by name, so I’ll limit myself to listing them:
- Hitman Pro ($25 for a quick scan) uses its own malware database. Comes in two versions: portable and with installer
- Zemana Antimalware – appeared quite recently. Cost – almost the same 25 $
- SUPERAntiSpyware has been on the market for a long time, but after several personal failures due to the unstable operation of the utility, I had to abandon it.
- Comodo Cleaning Essentials - I admit, I am not a fan of software from this manufacturer, although I honestly tried to come under their protection more than once. So my personal (and negative) experience did not extend beyond the Comodo Internet Security package. However, Comodo has its own free anti-malware utility, so give it a try.
In the next article, we will conduct field tests of anti-Trojans and see if they are as good as they are described.
Good luck to all of us
CategoryUseful programsConverting a registry file into a programThe Create item in the context menu is missingContents of the article:
Don’t despair and immediately call the repairmen, because to find Trojans, we will use special scanners. You can find and eradicate the Trojan for free! You don't need to be a super PC user.
From this article you will learn how to remove a Trojan from a computer or laptop on your own. Before we talk about removing Trojans, we need to understand what they are.
Delete Emotet files, folders and registry keys
Emotet files and folders
C:\WINDOWS\12345678.EXE C:\WINDOWS\SYSWOW64\SERVERNV.EXE C:\WINDOWS\SYSWOW64\NUMB3R2ANDL3373RS.EXE C:\WINDOWS\TEMP\1A2B.TMP PlayingonaHash.exe certapp.exe CleanToast.exe CciAllow.exe RulerRuler.exe connectmrm.exe
Emotet registry keys
HKLM\SYSTEM\ControlSet001\services\[Dropped_Filename]\Type: 0x00000010 HKLM\SYSTEM\ControlSet001\services\[Dropped_Filename]\Start: 0x00000002 HKLM\SYSTEM\ControlSet001\services\[Dropped_Filename]\ErrorControl: 0 x00000000 HKLM\SYSTEM\ControlSet001 \services\[Dropped_Filename]\ImagePath: %windir%\System32|SysWOW64\[Dropped_Filename].exe HKLM\SYSTEM\ControlSet001\services\[Dropped_Filename]\DisplayName: [Dropped_Filename] HKLM\SYSTEM\ControlSet001\services\[Dropped_Filename ] \ObjectName: LocalSystem HKLM\SYSTEM\ControlSet001\services\[Dropped_Filename]\Description: HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\1A345B7 HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\12C4567D
Remove Trojan using Kaspersky Virus Removal Tool
Undoubtedly, one of the best tools from one of the best market participants in the field of computer security. Briefly about the program: free and high quality. The installation file weighs about 100 MB. It gets along with the antiviruses installed on the system, does not require installation, but initialization takes time. It will also take a little to check the system. Everything, of course, is in Russian. Upon completion of work you will be greeted by a window:
False positives are extremely rare.