Recently, in my article, I told how I picked up stealer for the first time in many years without an antivirus on my computer. After the incident, I began a thorough study of the virus, all the traces it left, as well as their elimination. However, it is worth remembering that the fastest, best and most effective way in such a situation is to reinstall the system and completely clean the hard drive, including those volumes on which Windows was not installed. Of course, before this you need to save all important data in the cloud or on an external drive. It is advisable not to transfer old .exe files (executable) to a computer with a new system, as there is a high probability that the virus has left its mark on them.
Subscribe to our Telegram
Subscribe to our Telegram
If a situation arises that there is no time or opportunity to reinstall the system, you will have to clean it manually - our instructions, designed primarily for inexperienced users, will help with this. But it is worth remembering that even after all the steps taken, the virus can hide deep in the system only to appear again later. This is the reality of the twenty-first century - viruses develop no less rapidly than other software.
Content:
- How does virus infection occur?
- How to avoid infection?
- What happens when infected with viruses?
- How to get rid of viruses on a flash drive?
- How to get rid of a virus on your system hard drive?
- How to remove a virus from startup
Malware and virus software can have different effects on the operating system.
Some viruses delete data or steal important files from your computer. Others create shortcuts to arbitrary files or shortcuts with dubious advertising and Internet resources.
In addition, recently a high activity of viruses has been noticed, making shortcuts from important files through which it is impossible to open data .
Such viruses can be found on a hard drive or located on removable media , interfering with comfortable use or even replacing any connected device with a useless shortcut.
Windows restore checkpoints
Many problems could be avoided if home users worked with minimal privileges, but all the correct words of security specialists about this are broken in real life. Any home user who tries to follow this simple, useful advice is faced with Windows messages that you need to be an administrator to recognize a new flash drive, and you need to be an administrator to burn a DVD. And in the end, he spits on useful advice, turns on administrative rights and continues to live happily, and, interestingly, for a long time, since modern malware does not harm its guardian until the appropriate command is received. But when the command is received and you are asked to send an SMS to a short number or transfer money for decrypting your own DOC files, it’s definitely time to act.
Working with minimal privileges is not a panacea for all ills
From time to time, Windows finds ways to elevate your privileges to administrator. For example, even this year a vulnerability was found that allowed one to become an administrator of both Windows XP SP3 and Windows 7. A description of the vulnerability can be found at CVE-2010-0232 (https://xforce.iss.net/xforce/xfdb/55742 ) Thus, even working with minimal rights, you do not have a 100% guarantee that malicious code will not be able to gain administrator rights. Therefore, it is recommended to disable vulnerable services and constantly install component updates for Windows of all versions.
Before starting treatment, you need to remember the day when you could have become infected. This could, generally speaking, be visiting any website, downloading any program, viewing any PDF or video on the Internet, a USB flash drive plugged into a USB flash drive, or an attack from a nearby computer. Now you can get infected everywhere, even on quite decent websites and even by viewing completely harmless documents: PDF, XLS, DOC. There is no need to be afraid when choosing a date: even if you make a mistake with the date, you can always roll back the changes or choose an even earlier date. By default, System Restore in Windows XP and Vista saves system files and the registry once a day, and Windows 7 - once a week.
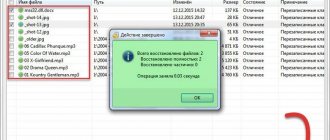
Then you launch the standard System Restore utility from the Start menu and return the system to its pre-infection state by specifying the desired date in the corresponding program window. System restore point is information about the state of the system at a specified date and time. Therefore, by selecting the desired restore point, you can return the system state to that moment. That's all. I repeat: if the treatment was unsuccessful, then you can roll back the changes back or select an even earlier restore point.
This is what the screenshot looks like for WindowsXP.
This is what the screenshot looks like for Windows 7.
When restoring in Windows 7, you can view the programs that will be affected during the restore. In Windows XP, System Restore monitors only a key set of system files and applications, but in Windows 7, the system monitors changes to the entire disk. However, on both operating systems, user files are not included in system restore points, so returning to a previous point will not result in the loss of your documents.
In Windows XP, if you stored documents in the “My Documents” folder, they will remain safe and sound, but the desktop will be returned to its previous state, and system files, including the registry, will be restored. In Windows 7, neither the My Documents folder nor the desktop changes during recovery.
If you are reading this article before you are going to use restore points, then check whether you have this function enabled - this will help you restore your system in the future in case of any emergency. In Windows XP, select: My Computer – Properties – System Restore , in Windows 7: Computer – Properties – System Protection .
Screenshot from Windows 7 with C drive protection enabled:
How does virus infection occur?
Malicious programs can get onto your computer in a variety of ways.
This could be either visiting an infected Internet resource or installing unlicensed software or games that can secretly infect the system during the program installation process. Viruses can also spread through removable media, flash drives or external HDDs. An infected removable storage device can transmit a virus to the computer during connection.
The most common virus programs are: viruses with the abbreviation Troj and Trojan , W32 , VBS , Mal , Worm and others.
Instructions for use:
After starting the program, you only need to start the verification process, wait a while, I want to say right away that sometimes the verification can last several hours, depending on the amount of information on the computer and the power of your PC. If you look in the program itself, it looks like this: Open the “Start new scan” tab, uncheck the quick scan box and press the play button. Let's look at the picture clearly.
We uncheck the quick scan checkbox for a reason. This is done to achieve maximum effect, so do not forget to strictly follow the instructions, so as not to write malicious comments later that you cannot cope on your own.
This is how the verification process will go:
And this is what the threats will look like, if of course you have them:
At the end of the scan, you will see the result, where the number of threats is indicated and a button to neutralize threats, this is what it looks like:
The SpyHunter program has the ability to add any programs to the exclusion list so that the application does not catch them as not being trusted. Typically, this effect occurs on programs that you use without a license (hacked, cracked, unknown). The exceptions section itself is shown in the picture:
To be more correct, the programs that you yourself allow to be skipped during the scan will be displayed here. Be careful and skip only those programs whose reliability you are at least 99% sure of.
Another useful category is “system guards” in which you can see what the program is doing, which files it recognized as dangerous and blocked, and which it scanned and decided were safe. You can say this is a small report for your personal analysis and making further decisions, it looks like this:
The system security function should always be turned on to avoid infection and blocked programs getting out of control. I hope I conveyed my thoughts to you as simply and usefully as possible, I look forward to your comments, I’m always interested to know if the article turned out good or if it’s just a bunch of useless text for you. Ask your questions and don’t be shy, together we can deal with all situations much faster, good luck friends!
How to avoid infection?
Since virus programs can be waiting for a user almost anywhere, a comprehensive approach should be taken to prevent infection:
- Using proven antivirus software , updating it regularly and checking the system.
- Using Windows 10's built-in security systems .
- Timely OS updates (system updates also include items that eliminate vulnerabilities).
- Using antiviruses for the Internet browser .
- Refusal to visit advertising and dubious resources, as well as download files, videos, games and programs from unverified sources.
What happens when infected with viruses?
Depending on the type and purpose of the virus software, it can have different effects on the system.
For example, some viruses spy on your computer, stealing personal information, electronic keys, bank card codes, as well as login information for social networking accounts, websites, etc. Other viruses pose a threat to files by simply deleting them or replacing them with meaningless shortcuts.
If you encounter a virus that deletes information, do not despair! Recovery Software specialists have developed a special utility, RS Partition Recovery, that can quickly recover any data that was destroyed by a virus, accidentally formatting the media, or was simply deleted. RS Partition Recovery allows you to recover deleted data from hard drives, flash drives and other storage devices. In addition, the functionality of the program allows you to recover long-lost data.
Windows SteadyState or disk snapshot
An even better free system recovery feature found in Windows is the SteadyState component. It is available for Windows XP and Vista and must be downloaded from the Microsoft website and installed additionally. This feature is not available in Windows 7 at the time of writing (May 2010). In principle, similar solutions exist from third-party developers, I will list them: ShadowUser, Deep Freeze, Renurnil, Shadow Defender. Some of them also have free versions. And some of them also work under Windows 7.
Windows SteadyState and other similar systems were originally designed for use on public computers in hotels and Internet cafes. But this technology is also very useful for home users as a system for constantly maintaining Windows in working order.
To understand how all such systems work, you need to imagine that your Windows starts up and takes a snapshot of all the information on the disks and then runs not on your real disk, but on this copy of the disk, it is called a shadow copy. It's as if you made a backup and worked on it instead of a real disk. You can change and delete anything on this shadow copy, but your real disk always remains the same. If you feel that it’s time to “cure”, then you can simply press the reset button and Windows will boot again from a “clean slate”, that is, from an unchanged copy of your disk. You spend 0 seconds cleaning the system.
Naturally, in order to remember all the changes on the copy, Windows SteadyState requires some disk space. To do this, a special cache file is allocated and used, the size of which you can adjust. This file records all "changes" that are not actually made to the disk. In similar products listed above, there are more original solutions when the available free space on the real disk is used, where information about changes during operation is stored. When you restart, all this information about changes is reset. Screenshot where hard drive protection is enabled.
Thus, the advantage of Windows SteadyState is that any changes that have occurred in the system can be cured by simply restarting the system. The downside is that you must take care of the safety of your documents that are stored on your disks. Since Windows SteadyState only protects the partition where the system is located, you can store documents on adjacent partitions. And if you store your documents (or movies or music) on network drives, you will make your life even easier. It should be noted that the third-party products listed above offer more advanced functionality for this type of protection, but at the same time ask for money for it.
How to get rid of viruses on a flash drive?
If a user finds a virus on a flash drive or removable drive using an antivirus program, the infected files should be quarantined . If the virus program is not removed by the antivirus or bypasses its protection, you should resort to manual removal using the built-in diskpart .
For this:
Step 1. Launch the Diskpart utility. right- click on the “Start” “Run” . In the window that opens, enter diskpart and “Ok” .
Step 2. Enter the list disk and look for the infected drive. In our case, this is a flash drive designated number 1. And enter the command “select disk 1” .
Step 3. Clean the disk with the Clean and wait for the cleaning process to complete.
Step 4. Next, you need to create a partition on the cleaned flash drive. To do this, enter crate partition primary , confirm the Enter and select the created partition with the select partition 1 .
Disable suspicious services in Task Manager
CTRL + SHIFT + ESCAPE keys . Next, end all suspicious services in the “ Services ” section.
2. In the task manager window, click on “ File ” and select “ Run new task ”. Type msconfig and click OK .
3. Next, open the “ Services ” tab and check the list again for any suspicious services. If you don't like any of the services, uncheck the box next to it and click " Apply ".
4. Now go to the next tab “ Startup ”. Here, look through all suspicious and unwanted programs, and if something happens, disable it.
5. Once you have identified all suspicious services, processes and programs, open Command Prompt and change the file attribute as described in the first method.
How to get rid of a virus on your system hard drive?
Viruses that get onto the system hard drive pose a great threat to files and data. The best way out of this situation is to completely reinstall the operating system or roll back Windows using restore points.
In addition, you can conduct a deep scan with antivirus programs.
More experienced users can use the built-in system checkers.
A complete list of points for the comprehensive removal of advertising and regular viruses can be found in the topic “How to remove a virus that displays advertising in the browser.”