Today we'll dig a little deeper into the topic of wireless connection security. Let's figure out what type of WiFi encryption is - it is also called “authentication” - and which one is better to choose. Surely, when setting up your router, you came across abbreviations such as WEP, WPA, WPA2, WPA2/PSK, WPA3-PSK. And also some of their varieties - Personal or Enterprice and TKIP or AES. Well, let's take a closer look at them all and figure out which type of encryption to choose to ensure maximum WiFi network security without losing speed.
How to fix invalid PSK?
Fix incorrect PSK provided for network SSID error
- Step 1: Reboot your modem and router.
- Step 2: Update your router's network driver.
- Step 3: Delete the existing wireless network profile.
- Step 4: Connect to your wireless network manually.
- Step 5: Use an elevated command prompt to connect to your existing network profile.
- Step 6: Update Windows.
3 Feb 2022
Wireless network security, WPA: theory and practice (part one)
The topic of wireless network security still remains relevant, although reliable (at the moment, of course) methods for protecting these networks have existed for quite some time. Of course, we are talking about WPA (Wi-Fi Protected Access) technology.
Most of the currently existing Wi-Fi equipment supports this technology, but, unfortunately, we still come across equipment in our laboratory that does not know about WPA. This is more than strange - 2005 is ending, and some manufacturers still believe that WEP technology will save wireless network users from information leakage. WEP has long been obsolete. This technology has been replaced by WPA, and the new 802.11i standard is also on the horizon (some manufacturers present it as WPA2).
WPA technology, designed to temporarily (pending the transition to 802.11i) close WEP gaps, consists of several components:
- 802.1x protocol is a universal protocol for authentication, authorization and accounting (AAA)
- EAP protocol - Extensible Authentication Protocol
- TKIP protocol - Temporal Key Integrity Protocol, another translation option - Temporal Key Integrity Protocol
- MIC - cryptographic packet integrity check (Message Integrity Code)
- RADIUS protocol
The TKIP protocol is responsible for data encryption in WPA, which, although it uses the same encryption algorithm - RC4 - as in WEP, but unlike the latter, uses dynamic keys (that is, the keys change frequently). It uses a longer initialization vector and uses a cryptographic checksum (MIC) to verify the integrity of packets (the latter being a function of the source and destination addresses and the data field).
The RADIUS protocol is designed to work in conjunction with an authentication server, which is usually a RADIUS server. In this case, wireless access points operate in enterprise mode.
If there is no RADIUS server on the network, then the role of the authentication server is performed by the access point itself - the so-called WPA-PSK mode (pre-shared key, shared key). In this mode, a common key is pre-registered in the settings of all access points. It is also registered on client wireless devices. This method of protection is also quite secure (relative to WEP), but is very inconvenient from a management point of view. The PSK key must be registered on all wireless devices; users of wireless devices can see it. If you need to block access to a network for a client, you will have to re-register a new PSK on all network devices, and so on. In other words, WPA-PSK mode is suitable for a home network and perhaps a small office, but nothing more.
This series of articles will look at how WPA works in conjunction with an external RADIUS server. But before we get to it, let's look a little more closely at the mechanisms of WPA. Before that, let’s look at WPA2 technology.
WPA technology was a temporary measure until the 802.11i standard came into use. Some manufacturers, before the official adoption of this standard, introduced WPA2 technology, which uses technologies from 802.11i to varying degrees. Such as using the CCMP protocol (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol), instead of TKIP, the advanced encryption standard AES (Advanced Encryption Standard) is used as an encryption algorithm. And the 802.1x protocol is still used for key management and distribution.
As mentioned above, the 802.1x protocol can perform several functions. In this case, we are interested in user authentication functions and encryption key distribution. It should be noted that authentication occurs “at the port level” - that is, until the user is authenticated, he is allowed to send/receive packets related only to his authentication process (credentials) and nothing more. And only after successful authentication, the device port (whether it is an access point or a smart switch) will be opened and the user will have access to network resources.
Authentication functions are assigned to the EAP protocol, which itself is only a framework for authentication methods. The beauty of the protocol is that it is very simple to implement on the authenticator (access point), since it does not need to know any specific features of the various authentication methods. The authenticator serves only as a transmission link between the client and the authentication server. There are quite a few authentication methods:
- EAP-SIM, EAP-AKA - used in GSM mobile networks
- LEAP - proprioretory method from Cisco systems
- EAP-MD5 - the simplest method, similar to CHAP (not persistent)
- EAP-MSCHAP V2 - authentication method based on user login/password in MS networks
- EAP-TLS - digital certificate authentication
- EAP-SecureID - method based on one-time passwords
Fig. 1, EAP frame structure
In addition to the above, the following two methods should be noted, EAP-TTLS and EAP-PEAP. Unlike the previous ones, these two methods first create a TLS tunnel between the client and the authentication server before directly authenticating the user. And already inside this tunnel the authentication itself is carried out, using either standard EAP (MD5, TLS), or old non-EAP methods (PAP, CHAP, MS-CHAP, MS-CHAP v2), the latter work only with EAP-TTLS (PEAP used only in conjunction with EAP methods). Pre-tunneling improves authentication security by protecting against man-in-middle, session hihacking, or dictionary attacks.
Figure 1 shows the structure of an EAP frame. The PPP protocol appeared there because EAP was originally planned to be used over PPP tunnels. But since using this protocol only for authentication over a local network is unnecessary redundancy, EAP messages are packaged in “EAP over LAN” (EAPOL) packets, which are used to exchange information between the client and the authenticator (access point).
Fig. 2, 802.1x in action
The authentication scheme consists of three components:
- Supplicant - software running on a client machine trying to connect to the network
- Authenticator - access node, authenticator (wireless access point or wired switch supporting 802.1x protocol)
- Authentication Server - authentication server (usually a RADIUS server)
Now let's look at the authentication process itself. It consists of the following stages:
- The client can send an authentication request (EAP-start message) to the access point
- The access point (Authenticator) responds by sending the client a client identification request (EAP-request/identity message). The authenticator can send an EAP request on its own if it sees that any of its ports have become active.
- The client responds by sending an EAP-response packet with the necessary data, which the access point (authenticator) redirects towards the Radius server (authentication server).
- The authentication server sends a challenge packet (a request for information about the client’s authenticity) to the authenticator (access point). The authenticator forwards it to the client.
- Next, the process of mutual identification of the server and client occurs. The number of stages of packet forwarding back and forth varies depending on the EAP method, but for wireless networks only “strong” authentication with mutual authentication of the client and server (EAP-TLS, EAP-TTLS, EAP-PEAP) and pre-encryption of the communication channel is acceptable.
- At the next stage, the authentication server, having received the necessary information from the client, allows (accept) or denies (reject) access, forwarding this message to the authenticator. The authenticator (access point) opens the port for the Supplicant if a positive response (Accept) is received from the RADIUS server.
- The port opens, the authenticator sends a success message to the client, and the client gains access to the network.
- After the client is disconnected, the port on the access point goes back to the “closed” state.
The described process is illustrated in Fig. 3 (one of the simplest EAP methods is shown there):
Fig.3, authentication process
As can be seen from the figure, EAPOL packets are used for communication between the client (supplicant) and the access point (authenticator). The RADIUS protocol is used to exchange information between the authenticator (access point) and the RADIUS server (authentication server). When transiting information between the client and the authentication server, EAP packets are repackaged from one format to another at the authenticator.
A detailed consideration of encryption algorithms, as well as methods for generating session encryption keys, is perhaps beyond the scope of this material, so I will consider them only briefly.
Initial authentication is performed on the basis of common data that both the client and the authentication server know about (such as login/password, certificate, etc.) - at this stage the Master Key is generated. Using the Master Key, the authentication server and client generate a Pairwise Master Key, which is passed to the authenticator by the authentication server. And based on the Pairwise Master Key, all other dynamic keys are generated, which close the transmitted traffic. It should be noted that the Pairwise Master Key itself is also subject to dynamic change.
Now let's move from dry theory to reality, namely the implementation of WPA in Windows XP. Normal WPA support (with AES support) appeared only starting with windows service pack 2.
Fig.4
In the Authentication
methods available
- MD5-Challenge is the most primitive and weak, we will not consider it;
- PEAP (Protected EAP) allows authentication based on certificates or login/password. It is interesting to us primarily because of the ability to authenticate the user using a login/password. In this case, we do not need to configure a public key infrastructure (PKI). It is enough to connect the RADIUS server to any database (regular file, mysql, ldap) with stored users and authenticate users using it.
- Smart Card or Other Certificate - regular EAP-TLS. Requires a configured PKI, uses certificates for client authentication. More flexible (of course, after setting up PKI) than login/password authentication. It is also the only way to get a working bunch of wireless users working in a Windows domain.
The second part of the article will discuss setting up Windows clients (Windows XP SP2), RADIUS server (FreeRadius), and PKI based on OpenSSL. The last two components run on the Gentoo Linux operating system.
Navigation
- Part One - Theoretical Aspects of the WPA Protocol
- Part two - WPA in EAP-PEAP mode
- Part three - WPA in EAP-TLS mode, creating certificates and setting up FreeRadius
- Part four - WPA in EAP-TLS mode, setting up clients
- Part five - EAP-TLS authentication of computers in Windows domain networks
Why do you need to encrypt WiFi?
I note that it is imperative to protect your WiFi with a password, no matter what type of encryption you choose. Even the simplest authentication will avoid quite serious problems in the future.
Why do I say this? It’s not even a matter of the fact that connecting many wrong clients will slow down your network—that’s just the beginning. The main reason is that if your network is not password-protected, then an attacker can attach itself to it, who will perform illegal actions from under your router, and then you will have to answer for his actions, so take wifi protection very seriously.
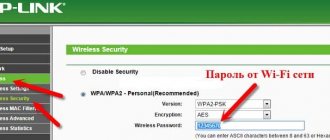
Wi-Fi access password
Everything is simple here. The password for your wireless access point (router) must be more than 8 characters and contain letters in different case, numbers, and punctuation marks. And he should not be associated with you in any way. This means that dates of birth, your names, car numbers, phone numbers, etc. cannot be used as a password. Since it is almost impossible to break WPA2-AES head-on (there were only a couple of cases simulated in laboratory conditions), the main methods of cracking WPA2 are a dictionary attack and brute force (sequential search of all password options). Therefore, the more complex the password, the less chance attackers have.
... in the USSR, automatic storage lockers became widespread at railway stations. The lock code was one letter and three numbers. However, few people know that the first version of storage lockers used 4 digits as a code combination. It would seem what's the difference? After all, the number of code combinations is the same - 10,000 (ten thousand). But as practice has shown (especially the Moscow Criminal Investigation Department), when a person was asked to use a combination of 4 digits as a password to a storage locker cell, a lot of people used their year of birth (so as not to forget). What the attackers used quite successfully. After all, the first two digits in the date of birth of the absolute majority of the country's population were known - 19. All that remains is to determine by eye the approximate age of the baggage check-in person, and any of us can do this with an accuracy of +/- 3 years, and the remainder we get (more precisely, the attackers) is less 10 combinations for selecting an access code to an automatic storage locker...
Most popular password
Human laziness and irresponsibility take their toll. Here is a list of the most popular passwords:
- 123456
- qwerty
- 111111
- 123123
- 1a2b3c
- Date of Birth
- Cell phone number
- Name
Security rules when creating a password
- To each his own. That is, the router password should not match any other password you have. From mail, for example. Make it a rule that all accounts have their own passwords and they are all different.
- Use strong passwords that cannot be guessed. For example: 2Rk7-kw8Q11vlOp0
The Wi-Fi password has one huge advantage. You don't need to remember it. You can write it on a piece of paper and stick it to the bottom of the router.
Router (router) security settings
When you set up Wi-Fi, you have several options for router security. If your router is left unsecured, third parties can gain access to it, use it for illegal activities on your behalf, monitor your Internet usage, or even install malware.
When you set up wireless security, you will have several options available to you, such as none, WEP, WPA, WPA2-Personal, WPA2-Enterprise, and possibly WPA3. Depending on how you plan to use the Internet, you may need more or less reliable protection.
What is WPA2?
The WPA2 protocol appeared in 2004. It is an updated version of WPA. WPA2 is based on the High Security Network (RSN) mechanism and operates in two modes:
- Personal Mode or Shared Key (WPA2-PSK) – uses a shared access password and is typically used on home networks.
- Enterprise mode (WPA2-EAP) – more suitable for corporate networks and commercial use.
Both modes use CCMP, which is based on the Advanced Encryption Standard (AES) algorithm to verify message authenticity and integrity. CCMP is more secure than WPA's original TKIP protocol, making it more difficult for attackers to attack.
However, the WPA2 protocol also has disadvantages. For example, it is vulnerable to key reinstallation attacks (KRACK). Key reinstallation attacks exploit a WPA2 vulnerability to imitate a real network and trick users into connecting to a malicious network instead of the real one. This allows attackers to decrypt small pieces of data that, when combined, can crack the encryption key. However, devices can be patched, so WPA2 is considered more secure than WEP and WPA.
Certificates and Standards
Although WPA2 is a certification program, it is often referred to as a standard and sometimes as a protocol. "Standard" and "protocol" are descriptions that journalists and even the developers of these certificates often use (and at the risk of being pedantic), but these terms can be misleading when it comes to understanding how standards and protocols relate to Wi-Fi. Fi. certification, if not outright false.
We can use the analogy of a vehicle being certified as roadworthy. The manufacturer will have instructions that define safety standards
.
When you buy a car, it will be tested
as safe to drive by an organization that sets vehicle safety standards.
So while WPA2 should be called a certification, it can loosely be called a standard. But calling it a protocol confuses the meaning of the real protocols - TKIP, CCMP and EAP - in Wi-Fi security.
What is WPA3?
WPA3 is the third version of the Wi-Fi Protected Access protocol. The Wi-Fi Alliance released WPA3 in 2022. WPA3 provides the following new features for personal and corporate use:
Individual data encryption . When logging into a public network, WPA3 registers a new device in a way that does not involve the use of a shared password. WPA3 uses DPP (Device Provisioning Protocol) for Wi-Fi networks, allowing users to use NFC tags or QR codes to connect devices to the network. Additionally, WPA3 uses GCMP-256 encryption instead of the previously used 128-bit encryption to provide security.
SAE (Simultaneous Authentication of Peers) protocol . This protocol is used to create a secure "handshake" in which a network device connects to a wireless access point and both devices exchange data to verify authentication and connection. Even if the user's password is not strong enough, WPA3 provides a more secure DPP experience for Wi-Fi networks.
Enhanced protection against password guessing attacks . The WPA3 protocol protects against offline password guessing. The user is allowed only one attempt to enter the password. In addition, you must interact directly with the Wi-Fi device: each time you attempt to enter the password, you must be physically present. WPA2 lacks built-in encryption and protection of data on public open networks, making password guessing attacks a serious threat.
Devices running the WPA3 protocol will become widely available in 2022. They are backward compatible with devices using the WPA2 protocol.