In this article I will talk in detail about what is DRM technology, I will introduce the reader to the features of DRM licenses, and explain how possible it is to reset them and bypass DRM protection.
Digital Rights Management license
Our lives are filled with different types of content. We watch movies on the Internet, listen to music, look at photos and read books, often without thinking that they were obtained illegally, thanks to the intellectual pirates of our day. The fight against illegal theft of content has become a headache for many authors; reputable companies spend many millions of dollars in order to provide high-quality and effective copyright protection.
Among various tools for protecting an intellectual product, DRM is very popular - it is a technology that allows the copyright holder to control access to the sold product, prevent its illegal copying, transfer, and so on. Unfortunately (or fortunately), the DRM license is not always effective, having both its advantages and disadvantages.
A similar technology is TrustedInstaller, which protects against the deletion of vital files for Windows (description at the link).
What is DRM
DRM is an abbreviation for “Digital Rights Management”, which means digital rights management. This control is implemented in the form of placing in a DRM-protected product various technical means that prevent the illegal disposal of an intellectual property product. Such a “digital lock” in the form of a licensed encrypted key can be very effective; the owner will not be able to copy the purchased digital product, transfer it, sell it, and so on.
The DRM key itself is presented in the form of a complex mathematical code, which is quite difficult to crack (crypto-algorithms are used). It can only be unlocked if you purchase the offered digital product.
In what cases is DRM used?
You can encounter the work of Digital Rights Management protection in the following cases:
- when playing a certain file, the system prompts you to enter a password, identifier, or a unique letter;
- launching the required file is possible only in a specific program;
- a certain program starts working only on a separate device , for example, on a PC, music center, etc.;
- The DRM license significantly limits the number of copies of a protected file.
DRM functionality
As mentioned above, DRM technology prevents the illegal distribution of copyrighted content, its copying, transmission, and translation into other formats. I realized that this DRM allows you to limit work with the product to the required lines, carry out limited copying, and remotely delete the required file on the user’s device. The possibilities of its functionality are very high.
At the same time, the sword, as usual, has two ends. The disadvantages of DRM include significant restrictions on the use of information, the probable impossibility of any copying at all, instability and unreliability of programs with such protection. Moreover, the principles of DRM sometimes conflict with the laws of some countries (eg Australia).
We look at information about DRM
To view information about what requirements different programs have, which applications will be affected by removing licenses, and whether the gadget supports technologies that are necessary for the normal operation of services, you should install DRM Info on your mobile device. The application publishes data about DRM components, indicating whether they are supported on gadgets.
Increase
Using this information, you can determine whether you should purchase licensed apps or premium accounts. For example, in order to be able to play videos in Full HD and 4K format on Netflix, you need level 1 of Google Widevine.
Many devices come with the third level, it turns out that there is no point in spending money on a premium account, because... There will be no improvement in quality here - the device does not support the necessary technologies.
Related articles:
How to update Google Play services
Android apps won't update
What is a DRM license?
A DRM license is a digital key used to decrypt previously encrypted content, while also granting the right to use that content. You can receive such a key only if you pay for it.
There are also partial DRM licenses in the form of various “trial periods”, a limited trial number of program launches and other types of temporary access to the product’s functionality, after which, after the end of which, access to the program is blocked, and we are offered to buy a full version of the program.
DRM key: what is it for?
Illegal copying is a problem that thousands of manufacturers, developers and authors are struggling with. DRM technology gives the user the right to use the product. “Digital Rights Management” is how the abbreviation DRM is translated. This is a kind of digital key with which you can protect data from piracy.
An example of such a key is given. For example, you download a trial version of an application. This trial expires after 20 days. After which, the data of this application can be encrypted using a DMR license and in order to continue using the application, you will need to purchase the full version. Thanks to this license, content users cannot copy the data protected by this technology, transfer it, or, as indicated in the example, use it for longer than the specified period.
Such a “lock” itself has a complex code and is far from easy to crack. Only experienced hackers can do this, and even those will have to try. After the development of a product, such a digital key is attached to the license.
Resetting DRM licenses
Resetting DRM licenses depends on the specifics of each license. Various hacker software allows you to reset the launch counters of DRM-protected files, unlink such files from certain sites, neutralize key verification by the software used, etc.
On Android, you can reset all DRM licenses loaded on your device.
- To do this, you need to go to “Settings”;
- Select “Restore and reset”;
- And then click on “DRMreset”.
You should use this option with extreme caution, because if you purchased a product with this license, then after resetting the DRM settings you will lose access to it. You should use this function in special cases, for example, if you sell your gadget.
Is it worth...?
I understand perfectly well that the countries of the post-Soviet space want to quickly become part of the civilized world. Laws are being adopted to combat “piracy”, etc. But the mentality coupled with insufficient income reduces all attempts to zero. People will download hacked software, listen to free music and watch movies online; they will not stop downloading Office, Photoshop and Windows from torrents. Alas, this is the reality.
But, if you have the opportunity to purchase the software, thanking the developers for their work, please do not be lazy to do so.
I'm sure you've figured out the DRM license - what kind of “beast” it is. All that remains is to make a choice - reset, remove protection, or live honestly and hope for the best.
How to remove DRM protection
There are various methods to remove this type of DRM protection. Let's look at some of them:
- special programs, for example, “DRM Media Converter” or “DRM Removal” allow you to remove DRM protection of WMV, M4B, M4V, ASF and other files;
- if WMV and WMA files are protected by DRM, burn WMA to CD and WMV to DVD, and then extract them to your computer, the protection will be removed;
- use a converter to convert protected WMV, WMA and other files into other video and audio formats (use Digital Music Converter, Sound Taxi, Note Burner and other similar programs), after conversion you will receive a “clean” file.
You can see an example of how to remove DRM protection from a PDF file in the video:
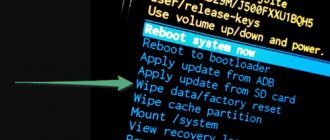
What does resetting your phone mean?
To erase all data from your phone, you can reset the system to factory settings. This procedure is also called formatting or hard reset. Important! Some of these steps can only be performed on devices running Android 9 and later.
Interesting materials:
What kind of mapping of a plane onto itself is called central symmetry? What transformation is called parallel transfer and how is it related to a vector? What kind of development is called development with complete transformation? Give examples? What is the current name of the city of Stalingrad? What kind of champagne can be called champagne? What event in world history was the reason for calling Moscow the Third Rome? What state of matter is called gas? What kind of vessel is called a small boat? What use of tense forms is called relative? What address in Excel is called relative examples?
Criticism [edit]
Some vendors implement broad DRM systems, restricting consumer rights beyond the scope documented by the OMA DRM standards. For example, some Nokia Symbian-based devices will completely refuse to send all
files of certain types over Bluetooth. For these phones, this blocks sending of MIDI files, Java Applets, and Symbian programs regardless of whether or not they are protected by DRM. Such phones will refuse any attempts to send such files with the message “Unable to send protected objects” or a similar error. This prevents sending such content, even when the content license explicitly allows or even depends on redistribution.
Weather applications, optimizers, default browser - it’s best to get rid of all of these.
Omacp - danger
Interesting point. OMA CP is a device control protocol of the OMA Device Management specification, developed in accordance with the mobile standard. This protocol uses the WAP wireless data transfer type. But here’s the funny thing: to transfer data you don’t need a SIM card installed or an Internet connection. This protocol is used by operators, for example, to set settings on the phone, of course you don’t need a SIM card, just like the Internet, but you still need a GSM module))
The second joke - considering what is written at the top, some craftsmen send an attack in the form of malicious OMA CP messages, which, for example, can change some parameters. And what’s interesting is that Android doesn’t have much protection against such attacks. The protection is done by phone manufacturers themselves, using OMA authentication. But that's a completely different story
I hope this information was useful. Good luck and good luck, see you again friends and take care of yourself!
To home! 04/12/2021
Ctrl+C Ctrl+V - what does this mean? (control + c control + c) Grizzly folder - what is it? Mb3install - what is this folder? PORT. IN on the music center - what is it? Windows10UpgraderApp - what is it? scoped_dir - what is this folder? Windows10Upgrade - can it be removed? im_temp - what is this folder?
Broadcast Services Security issues with DRM Profile [edit]
Broadcast services requirements being completely different from video-on-demand, the OMA BCAST Smartcard profile has been recommended by all the industries to be the unified standard used for Mobile TV broadcast.
Providers/Implementations [edit]
Commercial OMA DRM providers include:
- Authentec
- castLabs mobile TV Service Delivery Platform
- Discretix
- Irdeto
- Mutable OMA DRM
- NDS
- Philips
- Saffron Digital
- Viaccess
An open source solution for OMA DRM 2.0 is also available. [1]
Licensing format [edit]
The OMA DRM specification uses a profile of the Open Digital Rights Language for expressing its licenses. [2]
Determining that a file is OMA protected [edit]
Nokia Series 40 [edit]
On Nokia Series 40 phones, an installed file with DRM will have its “Send” option grayed out in its options menu. If the user attempts to send such a file via MMS, a message stating “The file is copyright protected” will appear. A Bluetooth file transfer will fail if the user tries to extract the file using Bluetooth, yet the file will still appear as present, and will still be deletable via Bluetooth.
However, if the file (such as a music track) is received with separate delivery—the key is sent separately from the actual download of the file, and the file contains a license URL—it is possible to forward the file to other devices. Once the file is activated on the new device, it will prompt the user to access the URL embedded in the file, and give the user the option to acquire the key.