It's true that we can use cellular data traffic here and there. But people still prefer Wi-Fi, in part because it is more stable and accessible.
The problem is that you can't take your Wi-Fi network anywhere. Instead, perhaps you can use the internet connection around you. And the Wi-Fi hacker app (without root) is able to guess the passwords of Wi-Fi networks around you and connect to the available ones. The biggest advantage is that you do not need to root your Android phone or tablet when using the Wi-Fi hacking app. In this post you can get top 5 best Wi-Fi Hacker Apps (No Root) .
- Top 1: AndroDumpper
- Top 2: Wifi Wps Wpa Tester
- Top 3: WPS Connect
- Top 4: WiFi passkey
- Top 5: Wifi Master Key Apk
Applications with global Wi-Fi password databases
One of the ways to hack a closed network is to search and substitute the required password using applications with global password databases for connecting to Wi-Fi networks. All you need to do is download the application, enter your region (geolocation) and the name of the wifi access point for which you want to receive the password. Next, the application will search its database and provide the current password. The most popular applications with wifi passwords:
The password search process itself can take from a few seconds to several minutes, but the time spent waiting is rewarded with access to the network.
2. Intercepting and hacking your neighbor’s Wi-Fi password
You can also gain access to someone else’s network by intercepting and hacking it. To do this, the following steps are performed: the “AirSlax” program is installed on the gadget, after which it is installed on a flash drive with the downloaded archive and the “bootinst.bat” file is launched - this way you will always have a “magic wand” at hand for quick selection. When the file is launched, press the combination “Alt + F1”, a menu is displayed in which “AiroScript” is selected. From the list of networks that appears, select the one needed for hacking (if the one you need is not there, press “1+ Enter”. Next in the list of commands, select the automatic mode, after which automatic interception of traffic and decryption of WEP passwords, as well as interception of the handshake of WPA networks, begins.
Andro>Samsung Root
- 1. Samsung Root
- 2. Root Samsung Galaxy S3
- 3. Root Samsung Galaxy S4
- 4. Root Samsung Galaxy S5
- 5. Root Samsung Galaxy S6
- 6. Root Samsung G900v
- 7. Root Note 4 to 6.0
- 8. Root Samsung Note 2
- 9. Root SM N9005
- 10. Root Note 5
- 11. Root SM G900F
- 12. Samsung Tablet Root
- 13. Root GT i9500
- 14. Root GT N7100
- 15. Root Samsung G935F
- 16. Root Samsung G900H
- 17. Root Samsung GT i9505
- 18. Root Samsung N7000
- 19. Root Note 3 on a lollipop
- 20. Root Note 3
- 21. Root Samsung S7
- 22. Samsung J7 Root
- 23. Root Samsung S2
- 24. Root Samsung S6 Active
- 25. Root Samsung GT S7562
- 26. Root Samsung Grand Premier
- 27. Root Samsung G925f
- 28. Root Samsung G920f
- 29. Root Samsung Note 4
Motorola Root
- 1. Moto G Root
- 2. Moto E Root
- 3. Moto X Root
- 4. Root Motorola Device
LG Root
- 1. Rooted LG G3
- 2. Root LG G3 Bit
- 3. Rooted LG G3 D855
- 4. Rooted LG G4
- 5. Root LG LS665
- 6. LG One Click Root
- 7. Root LG without computer
- 8. Root Lg Leon
- 9. Root LG H502
- 10. LG G5 Root
- 11. LG L90 Root
- 12. Root LG D722
- 13. Root LG H222
- 15. Root LG D325
- 16. LG Stylo Root
- 17. LG G4 Root Bit
- 18. Root LG H422
- 19. Root LG Volt ls740
- 20. Rooted LG G3 D850
- 21. Root LG D100
- 22. Rooted LG G2
- 23. LG K10 Root
- 24. Root LG D337
- 25. LG G4c Root
- 26. Rooted LG G4 Stylus
HTC Root
- 1. HTC Root
- 2. Root HTC One M7
- 3. Root HTC One M8
- 4. Root HTC One M9
- 5. HTC One S Root
- 6. HTC 10 Root
- 7. Root HTC Desire 510
- 8. HTC Desire Root
Nexus Root
- 1. Nexus 5 Root
- 2. Nexus 4 Root
- 3. Root Nexus 7
- 4. Nexus Root Toolkit
- 5. Nexus 6P Root
- 6. Nexus 5X Root
- 7. Nexus 9 Root
- 7. Nexus 6 Root
Sony Root
- 1. Root Sony Xperia Z1
- 2. Root Sony Xperia Z
- 3. Root Sony Device
- 4. Root Sony M4 Aqua
- 5. Root Xperia Z5
- 6. Root Xperia E1
- 7. Root Xperia M2
- 8. Root Xperia E3
- 9. Root Xperia Z2
- 10. Root Xperia Z3
Huawei Root
- 1. Huawei Root
- 2. Huawei P8 root
- 3. Huawei ALE L21 root
- 4. Huawei Y360 root
- 5. Huawei P9 Root
- 6. Root Huawei Mate 8
- 7. Huawei G7 Root
- 7. Huawei G8 Root
- 8. Huawei Y635 Root
- 9. Huawei Y550 Root
- 10. Huawei Y520 Root
- 11. Root Huawei P8 Lite
- 12. Huawei Y6 Root
- 13. Huawei Y330 Root
- 14. Huawei G630 Root
ZTE Root
- 1.ZTE Root
- 2. Root ZTE Z820
- 3. Root ZTE Zmax
- 4. Root ZTE Blade L2
- 5. Root ZTE N817
- 6. ZTE Maven Root
- 7. Root ZTE Blade l3
- 8. Root ZTE V795
- 9. Root ZTE Zmax 2
- 10. Root ZTE Z812
Zenfone Root
- 1. Kindle Fire Root
- 2. How to Root Andro >Root Alternatives
- 1. KingRoot application
- 2.Root Explorer
- 3. Root Master
- 4. One Click Root Tools
- 5. King Root
- 6. One Root
- 7. Vroot folder
- 8. Root APK-
- 9. Root Genius
- 10. CF Auto Root
- 11. Super Root APK
- 12. Alternatives to FramaRoot
Root Toplists
- 1. Hide apps without Root
- Root 2. Free In-App Purchase NO
- 3. Screen recorder NO Root
- Root 4. Game Recorder NO
- 5. Free Screen Recorder NO Root
- 6. Easy Screen Recorder NO Root
- 7. 50 Applications for rooted user
- Root 8. Game Killer NO
- 9. Root Browser
- 10. Root Uninstaller
- 11. Wifi Tether for rooted devices
- 12. Root file manager
- 13. No Root Firewall
- 14. Hack Wi-Fi without Root
- 15. AZ Screen Recorder Alternatives
- 16. Button Savior Non Root
- 17. Hide Root Access
- 18. Samsung Apps Root
- 19. Samsung Root Software
In this fast-paced world, we all need to stay connected to the Internet, no matter where we go. There are times when we may find it difficult to access the web and will require borrowing a Wi-Fi connection. Although you may have to hack the Wi-Fi network in order to access it. Don't worry! Hacking a Wi-Fi network is not rocket science. In this article, we will let you know how to hack Wi-Fi without root using some of the best apps out there. Start getting used to this Wi-Fi hacker without root tools.
3. Manual and software selection of wi-fi password
You can test your luck and try to guess the password manually. First, birthdays or significant dates (if you know them), simple combinations of a series of numbers or standard company passwords (if the name of the network has not been changed) are checked; the cipher can be one of: qwertyui, qw1234er, Password, repeating one number eight times. This method has no guarantees; it all depends on your imagination and the imagination of your neighbor. By the way, we have an excellent article with the most popular passwords for Wi-Fi networks in RuNet, read it!
How to switch to the 5 GHz band?
First you need to connect a Wi-Fi adapter that supports 5 GHz and equip it with a suitable antenna (they are also made for different bands). Then just run Wifite with the -5 key, and you will see five gigahertz access points. Usually there are much fewer of them than 2.4 GHz. This is due both to their relatively small distribution and shorter range. The higher the frequency, the faster (other things being equal) the signal fades.
Enabling 5GHz mode in Wifite
4. Forgery (phishing) in order to obtain a wifi password
This technique consists of luring a password out of a neighbor using cunning. To do this, you need to download the WiFiFisher application - it will help connect your neighbor to another network, which will give you the desired access code. Everything goes through several stages: the program prepares your computer for the forgery, then you select the wi-fi network for which you want to receive the password. Next, the program creates exactly the same access point with the same name as the network selected for attack, and “jammes” the selected Wi-Fi network for attack. The owner of the selected network loses the Internet, he tries to connect again - this time to the phishing access point you created (confuses it with his own), enters the login and password, which fall into your hands. That's it, the operation is completed.
To avoid falling for such tricks, be careful when entering passwords.
How to brute WiFi passwords?
It’s better to search passwords locally on a desktop computer with a powerful video card, but if you don’t have one, use online services. They offer limited sets for free, but even these are sometimes sufficient.
Hacking two WiFi passwords online
Another interesting option is to use a distributed computing network. This can be done, for example, with Elcomsoft Distributed Password Recovery. This versatile program understands dozens of password and hash formats, including .cap, .pcap and .hccapx. Up to ten thousand computers can simultaneously work on one task, combining the resources of their processors and video cards.
Distributed brute force of WPA hashes
Plus she has a very advanced approach to dictionary attack. You can use masks, prefixes and mutations, essentially expanding the volume of the dictionary several times.
Why perform a dictionary attack instead of a brute force attack?
The WPA(2)-PSK key is generated with a length of 256 bits. The number of possible combinations (2^256) is such that even on a powerful server with graphics accelerators it will take years to sort through them. Therefore, it is more realistic to perform a dictionary attack.
Usually Wifite2 does this itself. After grabbing the handshake, he checks its quality. If all the necessary data is saved in it, then an attack on the wordlist-top4800-probable.txt dictionary is automatically launched. As you might guess, it contains only 4800 of the most common passwords.
It is convenient because it works quickly even on an old laptop, but most likely the required combination will not be in this dictionary. That's why it's worth making your own.
How to compose your own dictionary?
First, I collected a collection of dictionaries from various sources. These were pre-installed dictionaries in programs for brute-forcing passwords, the /usr/share/worldlists/ directory in Kali Linux itself, databases of real passwords from different accounts leaked to the Internet, and collections on specialized forums. I brought them to a single format (encoding) using the recode utility. Then I renamed the dictionaries using the pattern dict##, where ## is a two-digit counter. The result was 80 dictionaries.
Merging 80 dictionaries, skipping identical entries
At the next stage, I combined them into one, removing obvious repetitions, and then ran the PW-Inspector utility to clean the combined dictionary from garbage. Since a WiFi password can be between 8 and 63 characters, I removed all entries shorter than 8 and longer than 63 characters.
cat * > alldicts | sort | uniq pw-inspector -i alldicts -m 8 -M 63 > WPAMegaDict
Then I thought that the file was too large, which could be reduced further without obviously compromising the efficiency of the search. Have you seen Wi-Fi passwords longer than 16 characters in real life? I didn't see it either.
pw-inspector -i WPAMegaDict -m 8 -M 16 > WPADict_8-16
On Kim Dotcom's file hosting service you can (647 MB in a ZIP archive, 2.8 GB in unpacked form).
Android applications for connecting to Wi-Fi without knowing the password
We have selected several of the best and most reliable Android applications for connecting to your neighbor’s Wi-Fi, here they are:
- WPS Connect is an application that automatically generates passwords for wifi networks; it will take the password in a couple of minutes.
- WiFi You - a repository of millions of passwords from wi-fi networks around the world;
- WiFinspect is an application for experienced users that allows you to conduct a detailed analysis of someone else's network;
- WIFI WPS WPA TESTER - will remove the password from an insufficiently protected Wi-Fi access point using identified vulnerabilities.
PC programs for connecting to your neighbor’s Wi-Fi without a password
Quite a few programs have been written for connecting to someone else’s Wi-Fi for a desktop PC or laptop, much more than for Android. This is understandable, Android is a relatively new OS when compared to Windows or Linux. We have collected the most common and necessary programs that will definitely help you, here they are:
- Wificrack is an electronic dictionary with millions of possible passwords for Wi-Fi networks.
- Macchanger - programs for replacing the Mac address of your device, needed to connect via WPS.
- Airodump-ng is an application that can determine the allowed address for connecting to someone else's Wi-Fi network without a password.
- Wifiphisher is a program for catching (forging) the password of someone else's password.
How to connect to Wi-Fi on a Windows laptop
So, how to connect to Windows Wi-Fi? The easiest way to connect is when your laptop sees the desired wi-fi network. In this case, all you have to do is click on the corresponding wifi network icon in the lower right corner of the screen, select an access point and enter a password. On Windows 10, the process of connecting to the network is not much different from the standard one.
Connecting to Wi-Fi via WPS
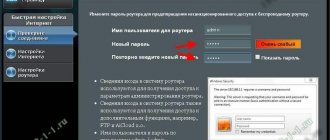
This option is a good way to connect without entering passwords. To connect a computer with Windows 7, 8 or 10 in this way, you will need to complete the following steps:
- Find the one you need in the list of available networks and click “connect”;
- in the window that appears to enter the password, at the bottom of the sign, select the inscription “connect using the button on the router”;
- then press the WPS button on the router itself;
- In this way, your device will be connected to the access point without entering a code.
The absence of such a window indicates that this function is not supported by your Wi-Fi adapter on the laptop.
Standard connection of a laptop to a router:
- We connect the cable to the router (WAN port), the second end of the wire is connected to the computer (when connecting for the first time, it is better to use this option than the wireless one). We plug the router into the outlet, if there is a power button, turn it on and give it a couple of minutes to boot.
- Next there will be several options:
- First - The router is connected by the provider and received the settings automatically (to check, go to the browser, load a couple of tabs). It works - connected.
- Second, the router does not connect automatically; you need to set up an Internet connection. You can find detailed instructions on the provider’s website, since subsequent settings depend on its settings and router model.
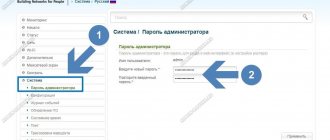
- We look at the settings, enter “192.168.11” or “192.168.01” in the address bar of the browser and press ENTER. If the address does not match, look for the correct one in the documents for the router (or on the sticker on the back cover of the router), after which the system may request you to enter a login and password (maybe admin for two fields or 1234). You can view detailed information on the provider’s website or in the accompanying instructions. Next, we configure the router according to the instructions on the website of your Internet provider.
- Finally, you need to set up your home Wi-Fi network. Going into the settings, find the section that is responsible for the wireless connection, create and write down a strong password. It will also be used to connect the rest of your devices. Finally, select WPA2-PSK as security.
This completes the standard setup of the computer to the router.
How to connect to Wi-Fi via phone from a router
How to connect to Wi-Fi from a mobile phone without entering a password? - quite simple. We connect wifi to OS Android via WPS. To do this, follow these steps:
- Open the Wi-Fi (WLAN) settings on your smartphone;
- find “advanced” or “advanced settings” and go into them;
- select “WPS by button” / “use WPS”;
- On the router, press the router button.
After these steps, the device is connected without asking for a password.
OC iOS (iphone) via WPS Unfortunately, the iPhone settings do not allow you to connect in this way. If you really want to try this connection process, you can read the help page on the Apple website, which describes in detail the recommendation for setting up a router for connecting iOS devices.
Is someone else's WiFi safe? Will my passwords be stolen?
When connecting to someone else's network, data security can of course be a big question mark, due to the existence of a lot of different kinds of programs on the side that distributes the Internet to you, which can intercept and decrypt your traffic, which will allow you to find out at least your browser history and passwords at a maximum. But this is already in the category where a hacker really needs to hack you. In other cases, your data is relatively safe.
For more protection, it is recommended to select “Public network” instead of “Home” in the device settings when connecting to someone else’s network.
This way the data stored on your computer will be protected.
When you turn on your smartphone, each resident of an apartment building can see many wifi connection points. Particularly inquisitive people have a desire to use someone else’s network, but how to find out the password for Wi-Fi.
Each router has its own IP address, through which you can view all the data of the neighboring device.
WiFi is an IEE802.11 standard network. The transmitter is installed in almost every apartment. You can find out the name and address of the router from the network mask, which people often forget to change during the initial installation of the device. You can connect to Wi-Fi if the owner of the network broadcasts it without a password at all.
What settings should you make before hacking WiFi?
By launching Kali in the default configs and plugging in a freshly unpacked WiFi adapter, you can only hack your router; there is no question of any pentest. To find out the possibility of a remote attack from the street (or at least from a neighboring room), you need to do the following:
- disable power saving for the WiFi adapter;
- increase the power of the dongle;
- prepare dictionaries for searching passwords;
- update all integrated software and install additional ones;
- check and save changes.
How to disable power saving for WiFi adapter in Kali?
In the terminal we write:
iw dev # Display a list of Wi-Fi adapters and find the external dongle by its MAC address iw dev wlan1 set power_save off # Here the external dongle is named wlan1
If you disable power saving and increase the power of the adapter, do not forget to provide it with cooling. It is also better to use USB 3.0 or power-enhanced USB 2.0 ports. They are usually distinguished by color.
How to increase the power of a Wi-Fi adapter?
There are two methods to fire them up. The first is through global settings in Kali. It is suitable for those adapters that read the region code from the OS.
Method 1
First, look at the current parameters:
- iw dev shows a list of wireless adapters and their maximum power allowed by the settings. Typically we see txpower 20.00 dBm (+20 decibels relative to milliwatt), which in theory means a transmitter power of 100 mW, but in practice it means that the attacked routers most likely will not hear your “whistle”.
- iw reg get displays global WiFi usage restrictions settings. In particular, the ISO 3166-1 country code, available frequency bands and channel widths. If country 00 is specified, then the country is not specified and strict restrictions apply
The most liberal standards for WiFi are in Guyana (GY) and Belize (BZ), where ten times the power of WiFi adapters is allowed. The corresponding entry in the database looks like this: country BZ: DFS-JP. (2402 - 2482 @ 40), (30). (5735 - 5835 @ 80), (30). The abbreviation DFS after the country code stands for Dynamic Frequency Selection. It can be performed according to the American (FCC), European (ETSI) or Japanese (JP) scheme. There is no need to change it.
Next, the frequency window in the 2.4 and 5 GHz bands and the channel width in megahertz are indicated. These parameters determine how many channels you will see.
To change the region, simply write in the terminal:
iw reg set BZ # Mentally transported to Belize with the laptop ip link set wlan1 down # Disable the external dongle designated as wlan1 iw dev wlan1 set txpower fixed 23 mBm # Double the transmitter power
The scale here is logarithmic, so doubling the power (up to 200 mW) corresponds to an increase of 3 dBm (up to 23 dBm). Simply put, TxPower(dBm) = 10 * LOG(P/1), where P is the power in milliwatts.
Change region and get 1000 mW
Don’t rush to turn the dongle all the way right away. For each device there is a reasonable limit, which is selected experimentally. One of my adapters works more stable at 27 dBm (500 mW) than at 30 dBm (1000 mW), and it is generally useless to drive the other above 23 dBm.
If you are lucky enough to buy a high-quality dongle with a large power reserve (for example, for street use), then try specifying the PA region. This is Panama, where transmitters up to 4 W (36 dBm) are allowed. True, you won’t get as much from a USB 2.0 port—you need USB 3.0 or additional power.
Method 2
Used for those WiFi adapters that have the regional code programmed into their own memory. For example, these are all the Alfa Networks adapters I have encountered. They ignore global settings (including iw reg set BZ), so you will have to change the restrictions themselves for the country that is already stored in the dongle’s memory.
iw reg get # Find out for which country the adapter was released git clone https://kernel.googlesource.com/pub/scm/linux/kernel/git/sforshee/wireless-regdb # Clone the database of regional WiFi restrictions cd wireless-regdb/ # Go to this directory gedit db.txt # Edit the database source
Changing the power limit of WiFi transmitters in regional settings
We find the desired country by code and instead of 20 (dBm) in brackets we write 30 everywhere (or even 33, that is, 2000 mW). We make similar changes for country 00 (or at least for all countries) and save db.txt.
Previously, to compile a database from a text file and sign it, you needed to install a Python wrapper for the OpenSSL library, but the new version of Kali already has it (python3-m2crypto). Therefore, we simply write the make command and get a new regulatory.bin, where all restrictions are removed (more precisely, they are set obviously large).
Creating your own database with permissions for more powerful WiFi
Next, we delete the old (original) database, copy our (modified) one instead, copy our public key (since the database has a digital signature) and restart.
rm /lib/crda/regulatory.bin cp regulatory.bin /lib/crda/regulatory.bin cp $USER.key.pub.pem /lib/crda/pubkeys/ reboot
Changing power limit in regional settings
All! Now, after rebooting into Live USB Persistence, we set the adapters to increased power in the standard way.
ip link set wlan1 down # Turned off the dongle iw dev wlan1 set txpower fixed 23 mBm # Doubled the power ip link set wlan1 up # Turned on the dongle
Let's check the result:
iw reg get
It should be something like this (here a 10 dBm increase in power).
Increase the power of the WiFi adapter tenfold
How to quietly connect to a router?
You can find out the type of wifi device by the name of the network displayed in the list of available ones. You can use the network unlimitedly if the device itself was able to connect without a password.
Your actions are invisible when the traffic load is low. You can detect something is wrong if your neighbor looks at the list of connected devices. And he will do this through the laptop browser, where the corresponding router address is entered.
You can go into the router settings through a browser by entering the address 192.168.1.1. By default, the nickname is set to admin and the same password.
But before that, the laptop needs to be connected to wifi. By quietly correcting the data, you can annoy your neighbor and interrupt the connection. After that, it will reset the settings to factory settings and change the access codes.
The wifi password and ip address are easy to find out using special hacking programs, but the latest versions of routers provide this feature and block automatic connections.
It is convenient to have a neighbor connection point for the following purposes:
- No need to pay a monthly subscription fee;
- WiFi allows you to use several devices at once, unless your neighbor sets a limit on the number of connected devices;
- Your identity will not be established for illegal connections.
Hacking someone else's wifi is an illegal act, which results in criminal liability.
Whether or not to hack someone else’s router is up to everyone personally, but why not try? The IP address of the device is indicated on the back cover of the wifi transmitter. You can look it up at a computer hardware store.
Ways to solve connection problems
To connect to most wifi networks you will have to crack the password. A simple way to solve Internet access is to purchase your own router and get your own IP address for the devices.
But an inquisitive mind is always drawn to complex tasks. The first step is to find information about the new network and whether there is a Wi-Fi password on the router.
You can find out after viewing the details of the current wifi. Open the “Control Panel” and find the Internet network item and go to the “Network Control Center”. We need to open the “Network Connection” item.
At this point you can see:
- Complete list of available wireless networks;
- Broadcast signal level;
- Access to Wi-Fi. If it is open, then you are very lucky, use free wifi.
You can hack wifi using programs to find a suitable password. They run on your laptop and try possible variations until a connection is made.
It should be remembered that no amateur hacker can use the neighbor’s Wi-Fi completely unnoticed. The IP address is calculated instantly if you connect the device to the network.
A list of all current connections is displayed in the router itself. It is always available on a PC connected to it locally via a wire. But rarely does anyone control their network while the transmitter is operating stable. One extra neighbor on the “wire” will not make a difference; the speed drops significantly with a huge list of wi-fi “freeloaders”.
Authentication scheme and analysis
So first, let's take a look at the picture below. Look, we generate a PIN, but the search only takes place in the first part of M4. After sending the first part, if it is not correct, we resend it. If it is correct, then we get a positive answer and begin to sort through the second part of M6 until we get a positive answer.
For implementation we will use the Linux operating system. In general, you can forget about Windows, since there is not a single normal hacking program there. Now I will give a screenshot of an approximate hack.
Everything is as I said earlier. First there is a search of the first part, then a search of the second. At the very end, the system shows us the full password for the wireless network. The problem is that users, when setting up their access point, forget to disable WPS. In general, you can, of course, not disable this function, but deactivate password authentication, leaving the connection by pressing the VPS button.
What hacking programs are there?
Applications do not guarantee 100% wi-fi hacking results; you will have to connect using several programs. Finding out the password is possible with a probability of up to 90%.
Here is a list of programs available on the Internet:
- WifiSidejacking - the program interface is entirely in English, but a detailed manual helps you connect to Wi-Fi in a few minutes;
- Aircrack-ng is a set of tools for competently searching for not only wifi passwords, but also helps to determine the IP address of connected subscribers;
- AirSlax - works with wifi in 6 simple steps: scanning the network, selecting a target, capturing packets, disconnecting the client, guessing the password and saving the finished result;
- Wifipirate 13 is a powerful application that provides passwords of all surrounding wireless broadcast points;
- CommViewforwifi—used to analyze networks, search for new connection points and neighbor activity times.
Aircrack-ng includes a software package of applications for decrypting intercepted files, creating encrypted signals, recovering Wep keys in Windows. It includes a tool for converting files with the ivs extension.
There is also the ability to monitor the current connection and determine the wi-fi network traffic.
Through a remote IP address, the Airserv-ng application provides access to the laptop's wireless card. Allows you to solve problems with drivers and make changes to the operating system. The program hacks wi-fi networks: Wep, searches for WPA-PSK keys, WPA/WPA2. All operations are carried out automatically without the participation of the owner of the magic code.
No programmer can predict the password selection time; it all depends on the following factors:
- Password complexity, presence of letters and numbers;
- Wi-fi device type;
- Has the IP address changed?
- Distance from the transmitter, device load.
- The selected utility and scanning method.
Implementation of Bruteforce for WiFi
- First of all, we need Linux, but not simple and golden. In general, the best option is BackTrack. This package contains all the necessary programs, as well as special drivers. You can download it from the official website – backtrack-linux.org. In this case, you don’t have to install the system separately or as a second OS. Just make a boot disk with a virtual machine. The distribution can also be found on the same site;
- We launch the system and command line. Enter your login information: Login: root;
- Password: toor;
startx
- Now we need to update the Reaver program, for this we will need the Internet. If your Internet does not come from the gateway, but directly from the provider via cable, then it will still need to be configured. If the Internet comes from the router, then everything is in order - we continue dancing. We write the command for installation:
apt-get update apt-get install reaver svn checkout reaver-wps.googlecode.com/svn/trunk reaver-wps cd ./reaver-wps/src/ ./configure make make install
NOTE! You can, of course, try to use the already installed version, but it’s better to update it using the commands above.
- Now we need to check that the wireless module is working correctly, and that the drivers out of the box are connected to it:
iwconfig
- Most often, the connection is designated as wlan0. If you previously connected to a wireless network to download reaver, then it is better to disconnect from your Wi-Fi. Now you need the module to be turned on in network search mode. It will now catch packets from all wireless networks:
airmon-ng start wlan0
- A new connection, mon0, should be created. If you have created something else, then instead of mon0, use your connection name. Now you need to find out the MAC address of the desired access point:
airodump-ngmon0
- You should now see a list of networks. We will contact the access point exactly by MAC address. Therefore, next we enter the command to launch the program:
reaver -i mon0 -b 00:21:29:74:67:50 -vv
- Instead of the MAC address that I have, you should select any of the first ones from the list of networks and simply replace it.
Now we just have to wait and watch. The system will start searching M4 first, and then M6. At the very end we will see complete information on the access point, as well as the WPA PSK key we need, with which we can connect. The search took about 3 and a half hours. But I have a weak computer, so maybe you can do it much faster.
How to hack a hotspot on Android?
Finding a password for a smartphone’s wi-fi transmitter is even more interesting. Often neighbors use the Internet through their cellular operator. Based on the results of the selected password, it is possible to determine the IP address of the subscribers.
There are software applications for scanning networks:
- Wifi Password break;
- To control wifi, use the Wifikill program;
- Wibr+ - serves as an assistant for hacking wi-fi without any special hacking skills;
- WiHackmobile is a simple program for finding passwords of surrounding networks;
- Wi-Lomster is a popular application for working on a smartphone;
- WifiRouterkeygen - quickly finds Wi-Fi passwords to connect to a neighbor. The interface is easy to use and does not require familiarization with the utility.
The listed utilities can identify the most attractive network for hacking.
You won’t be able to connect quickly if your neighbor has taken care of wi-fi protection:
- Saved a long and complex password;
- Changed default logins;
- Purchased the latest version of the provider's router;
- Turns off the transmitter when not in use;
- Controls connections and has introduced restrictions on the number of devices;
There is no chance of hacking networks with a reliable level of encryption using any utility.
If the router turns off during scanning, the procedure will have to start over.
Connecting your device is half the battle, but you need to carefully hide your IP from your neighbor. When he realizes that his wi-fi network has become public, he will wonder who used the router. The problem will develop into a scandal if he comes to you.
The Wifikill utility helps you find intruders using your router. With one click, it will block a user by IP address. But he can change it, so it’s better to set restrictions on the number of connected devices. It’s better to create a list of allowed devices.
There are various ways to gain remote access to someone else's phone, but on our website we only discuss legal methods. And the only such way is to install a monitoring application on the phone you want to access.
After analyzing a huge number of applications, sites, forums and offers, we came to the conclusion that there are no free and high-quality monitoring programs. Yes, they cannot exist. “Free cheese is only in a mousetrap,” as they say. Therefore, all the programs that we mention are paid, but some of them provide free trial periods, during which you can test the functionality and understand whether the application is suitable for you or not, and whether you are willing to pay for it. We have compiled our own rating, which you can find out in more detail here.
Top 2: Wifi Wps Wpa Tester
Main features of this Wi-Fi hacker:
1. This application can hack Wi-Fi network password using various algorithms such as Dlink, Arris, Zhao, etc.
2. It will scan all Wi-Fi networks around you automatically as soon as you open the app.
3. You can use this Wi-Fi hacker app (no root) to monitor your Wi-Fi networks and identify their vulnerabilities.
4. It tells you about secure Wi-Fi networks and you don't have to worry about data leakage when using a new connection.
pros
1. You can download this app for free from your Google Play Store.
2. It is easy to use and all you need to do is one click of a button.
3. If one method fails to connect to the network, it will automatically try another algorithm.
Minuses
To use this app on Android 5.0 or earlier, you need to root your device first.
The undoubted leader in the spyware market is the surveillance application IKeyMonitor.
IkeyMonitor will allow you to remotely log into someone else’s phone, listen to and record calls, read SMS, and observe all the person’s activity on the Internet.
In addition to these basic application tasks, you will be surprised by the many other features of IKeyMonitor.
Installing spyware is very easy and quick. After the purchase, you will be taken to your personal account, where all the information you are interested in from the phone you are going to monitor will be received in the future.
This is what your personal account will look like:
iKeymonitor features:
- Listening and recording calls (from a phone, computer or laptop).
- Listening to the environment (remote access to the device’s microphone, which can be turned on at any convenient time).
- Remote control.
- Phone multimedia control.
- Notifications (about SIM replacement, events and calls).
- You can even see deleted SMS.
- Complete list of contacts.
- Call log (all incoming, outgoing, missed, deleted).
- GPS location and geo-fencing.
- Free application for mobile viewing (personal account).
- Keylogger. All manipulations with the device screen and keyboard are transferred to your personal account
- All messengers (VKontakte, WhatsApp, Skype, Facebook, Instagram, Viber, etc.).
- Websites visited.
- Remote screen lock.
- All photos and videos (received, sent, deleted and taken on the phone).
- Automatic screenshots.
- Ability to block contacts, applications and games.
- Set up “hot words” in calls and messages.
- Browser history.
- And much more.
Legal mobile spy IKeyMonitor a 100% money back policy.
The developers of the iKeymonitor spy program are constantly working on regular updates and adding new features, which is certainly important for potential clients.
So, at the moment it is possible to install iKeyMonitor for almost all iPhone/iPad/Android. At the same time, the iPhone can be either jailbroken or without it. And also Android with root/without root.
If for any reason you doubt whether iKeymonitor is right for you, you can always try the free version. All you need to do is create an account and install the application on the device you want to access remotely. When you sign up for the free version, iKyemonitor does not ask for your banking information, so after the trial period the program simply stops working. You don't have to worry about being charged a monthly fee.