Many people have found themselves in a situation where they need Wi-Fi and their smartphone or laptop catches many networks with a good signal, but each network has a password. Of course, we can say that connecting to someone else’s network against the will of the owner is ugly. But what if connecting to the Internet is a matter of life and death? For such cases, there are several working options for bypassing the protection:
- brute force;
- changing mac address;
- hacking programs;
- android applications;
- traffic interception.
How to find out your neighbor's WiFi password
Traffic interception
This is perhaps the most reliable, but at the same time quite difficult method. To use it, you need not only to have an understanding of a wireless network, but also to understand the principle of operation of the router and password encryption.
Initially, the Internet signal is transmitted via cable. The cable transmitting the signal is connected to the router. And the router already distributes the signal “through the air”. The password is set in the router itself and when we enter it from our device, a signal with the password is sent to the router. A response is received from the router with the password set, and if the password is entered correctly, a connection occurs. If not, no connection occurs.
Traffic interception scheme
One way or another, the router gave us a response with the password set on it. Once connected, it exchanges information with all connected devices. They are called data packets. If you wish and have enough computer literacy, these data packets can be intercepted and, by decrypting them, you can obtain the password that was set on the router.
But as mentioned earlier, this method is quite complicated, because to implement it you will need a high level of knowledge in the field of computer technology. But you can simply use the special CommView program, the instructions for which were described above.
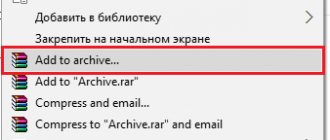
Changing mac address
The essence of this method was described above. You need to get to the mac address so that the Internet on the device works through someone else's router. Found the ID? Now change it on your device. On a computer this is done like this:
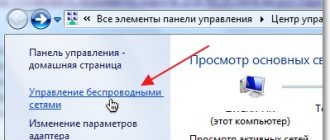
- Go to the “Control Panel”.
- Go to the “Network and Internet” section, select “Network and Sharing Center”.
- Find the category: “Changing adapter settings.”
- Right-click the context menu on the desired access point and select “Properties”.
- “Network” tab, then “Configure”, after “Advanced”.
- Oh and enter the treasured 12-digit number.
- Click “OK” to restart the network connection.
On smartphones, changing the mac address is much more difficult. On Android you need to get root rights and fight with third-party applications. Do at your own risk.
Mac address scanner
Mac address scanner reveals data of surrounding mac addresses. It does not require special knowledge and does not have a complex interface. In this case, the creator of the utility is not important. There is a version from ColarSoft. You need to install it, run it and click the green “Start” button to analyze the surrounding networks. The received data is saved in the computer's memory or sent to online storage.
The second column displays current mac addresses. If the owner of the access point does not use such protection, the ID will be displayed as several X's. Otherwise, you will receive a 12-digit combination.
Risk of using someone else's Wi-Fi
Many people are afraid to use a third-party network because of the risk of interception of personal data by another user. For example, you can often hear that in this way the owner of a network can find out the passwords of the user connected to it.
But here the question arises: aren’t you afraid to use open Wi-Fi, for example, in a cafe? Although there the risk is much higher, because the number of connected users is off the charts.
Why is it unsafe to use someone else's Wi-Fi?
In neither case, no one will be able to access your data. Moreover, you don’t even need additional protective equipment. Operating system developers have already taken care of all this. In Windows, the standard set of programs contains settings designed to protect user data. These settings will certainly be enough to prevent another person connected to the same network as you from using your data. Even if it is the owner of the router.
The main thing is that when you connect to a new network, honestly give answers to all the questions that the system will pose to you. Then you will trust in her reliable hands and will not be afraid of anything.
Password selection
There are several ways to calculate the code from your neighbor's Internet. Of course, such an act will be considered hacking. The simplest method, which does not require any knowledge, is regular selection. People often do not change standard passwords or use very simple combinations that are known to everyone. A few examples:
- qwerty;
- admin;
- 123456;
- 111111.
Those who set such passwords either do not worry about their own security, or simply do not understand anything about “computers.” Therefore, before downloading any programs, you should try to guess the simplest phrases and numbers.
Legal consequences
More recently, internet theft has become a criminal offense and can be punishable by up to five years. But in reality, it is unlikely that you will face real punishment just for connecting to someone else’s router. This will only be considered a truly serious crime if you used the connection to obtain the user’s personal data.
Consequences of using someone else's Internet
In addition, you must agree that it is unlikely that in our country a case of traffic theft will go to trial. You can always come to an agreement with your neighbor and apologize, not to mention the fact that it will be quite difficult to figure you out. And if you use closed networks found on the street, then this is generally almost unrealistic.
But, still, it is not recommended to use someone else’s Wi-Fi unless absolutely necessary and for a long time. After all, these are material losses for the owner of the network, which becomes a serious reason for litigation.
Hacking programs
The essence of hacking platforms is described above, but here is a list of current and powerful programs used around the world.
- AIRCRACK . It is capable of absolutely everything, but it is a command line where you need to enter commands. They didn’t deliver a friendly interface;
- AIRSNORT . Intercepts data packets, selecting keys using cunning algorithms. It was updated several years ago, but has not lost its relevance;
- KISMET . More protection from third-party penetration, but, if desired, allows protocol packets from third-party routers, and even finds hidden networks;
- FERN WI-FI WIRELESS CRACKER . Focused on system security. Searches passwords using a dictionary, and in the case of WEP router protection, connects algorithms to output the real password. Constantly updated, acquiring additional functions;
- AIRJACK . Functionally similar to AIRCRACK, but it can also create a false access point, which helps protect the main one from unwanted hacking, or make sure that the victim, without suspecting the substitution, enters the password himself into a non-existent router;
- WIFIPHISHER . A unique piece of software, actually a virus, that connects to someone else’s system and displays a message in the browser, requiring you to enter your WiFi password, supposedly to install important updates. The user obeys and no longer notices any changes. The attacker gets what he wants.
Commview for intercepting data packets
I would like to tell you a little more about this toolkit. The application is constantly updated, acquiring valuable mechanics and categories. Primarily used by network programmers and wireless network administrators.
The program breaks data packets into protocols, shows signal strength, its speed and other useful parameters.
To borrow the nearest Internet, you need to download the application and scan the desired WiFi from the list of networks. The program will display the entire package of transmitted data. Commview allows you to use the “node reassociation” function. Users will be disconnected from the connection automatically and instantly connected back, and the program will open the EAPOL protocols. They contain the necessary information - the desired passwords for hacking a Wi-Fi network.
AirCrack-NG will help you decode the received protocols.
Using Aircrack ng
This is a complex toolkit that requires preliminary preparation and many additional steps. You shouldn’t press “start” and wait for a positive result. Having previously received all possible data through Commview, you need to:
- Download and launch Aircrack ng, go to the first tab.
- In the “Filenames” line enter the path to the file with intercepted packets.
- In the "Encryption" category, select "WPA".
- There is a dictionary, or a database of popular passwords, it needs to be inserted into the Worldlist line.
- ABOUT.
- In “Specify ESSID” write the name of the desired network.
- In the window that appears, enter the network MAC address, which can be obtained using Mac address Scanner.
- "Launch". Analysis of available data will take from 5 hours to several days.
Options for protecting your own network
As it turns out, there are many options for spying on Wi-Fi data. Anyone who has a router at home or in the office should make it difficult for third parties to access. Otherwise, everyone risks being cruelly deceived. It is recommended to use the following tips:
- Come up with a complex combination for a password - at least 10-12 characters, taking into account the keyboard layout, register, signs and numbers.
- Disable WPS, this function remembers authorized users and reconnects them automatically.
- Periodically changing the PIN of the device used, as well as removing the factory inscription from the case.
- Limit access to PIN information and do not enter it on dubious sites.
These steps will help you effectively protect your network. Now only a hacker with a capital H can hack it. Rest assured, if the hack is successful, he is somewhere nearby. Only the proximity of the attacker can lead to a successful outcome.
How to hack a hotspot on Android?
Finding a password for a smartphone’s wi-fi transmitter is even more interesting. Often neighbors use the Internet through their cellular operator. Based on the results of the selected password, it is possible to determine the IP address of the subscribers.
There are software applications for scanning networks:
- Wifi Password break;
- To control wifi, use the Wifikill program;
- Wibr+ - serves as an assistant for hacking wi-fi without any special hacking skills;
- WiHackmobile is a simple program for finding passwords of surrounding networks;
- Wi-Lomster is a popular application for working on a smartphone;
- WifiRouterkeygen - quickly finds Wi-Fi passwords to connect to a neighbor. The interface is easy to use and does not require familiarization with the utility.
The listed utilities can identify the most attractive network for hacking.
You won’t be able to connect quickly if your neighbor has taken care of wi-fi protection:
- Saved a long and complex password;
- Changed default logins;
- Purchased the latest version of the provider's router;
- Turns off the transmitter when not in use;
- Controls connections and has introduced restrictions on the number of devices;
There is no chance of hacking networks with a reliable level of encryption using any utility.
If the router turns off during scanning, the procedure will have to start over.
Connecting your device is half the battle, but you need to carefully hide your IP from your neighbor. When he realizes that his wi-fi network has become public, he will wonder who used the router. The problem will develop into a scandal if he comes to you.
The Wifikill utility helps you find intruders using your router. With one click, it will block a user by IP address. But he can change it, so it’s better to set restrictions on the number of connected devices. It’s better to create a list of allowed devices.
How to quietly connect to a router?
You can find out the type of wifi device by the name of the network displayed in the list of available ones. You can use the network unlimitedly if the device itself was able to connect without a password.
Your actions are invisible when the traffic load is low. You can detect something is wrong if your neighbor looks at the list of connected devices. And he will do this through the laptop browser, where the corresponding router address is entered.
You can go into the router settings through a browser by entering the address 192.168.1.1. By default, the nickname is set to admin and the same password.
But before that, the laptop needs to be connected to wifi. By quietly correcting the data, you can annoy your neighbor and interrupt the connection. After that, it will reset the settings to factory settings and change the access codes.
The wifi password and ip address are easy to find out using special hacking programs, but the latest versions of routers provide this feature and block automatic connections.
It is convenient to have a neighbor connection point for the following purposes:
- No need to pay a monthly subscription fee;
- WiFi allows you to use several devices at once, unless your neighbor sets a limit on the number of connected devices;
- Your identity will not be established for illegal connections.
Hacking someone else's wifi is an illegal act, which results in criminal liability.
Whether or not to hack someone else’s router is up to everyone personally, but why not try? The IP address of the device is indicated on the back cover of the wifi transmitter. You can look it up at a computer hardware store.