The Active Directory Module for Windows PowerShell is one of the main tools for administering a domain, managing objects in Active Directory and obtaining various information about AD computers, users, groups, etc. Any Windows administrator should know how to use both the AD graphical snap-in (usually These are ADUC - Active Directory Users & Computers) and cmdlets of the RSAT-AD-PowerShell module for performing everyday Active Directory administration tasks. In this article, we'll look at how to install the Active Directory PowerShell module on Windows, its main features and popular cmdlets that are useful for managing and interacting with AD.
Installing the Powershell Active Directory module on Windows Server
Active Directory for Windows PowerShell is already built into Windows Server operating systems (starting with Windows Server 2008 R2), but is not enabled by default.
On Windows Server 2016, 2022, and 2022, you can install the AD module for PowerShell from Server Manager ( Add Roles and Features → Features → Remote Server Administration Tools → Role Administration Tools → AD DS and AD LDS Tools → Active Directory Module for Windows PowerShell ).
In the English version of the server, this is respectively in the Server Manager: Add Roles and Features → Features → Remote Server Administration Tools → Role Administration Tools → AD DS and AD LDS Tools → Active Directory module for Windows PowerShell .
If you have already installed the Active Directory Domain Services role, this means that the Active Directory Powershell module is already activated and no additional steps need to be taken.
See also: A complete guide to Active Directory, from installation and configuration to security auditing. Part 4: Installing Active Directory Domain Services on Windows Server 2022
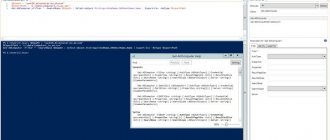
You can also install the module from the PowerShell console using the command:
Install-WindowsFeature -Name "RSAT-AD-PowerShell" -IncludeAllSubFeature
See also: Managing Windows Server roles and features using PowerShell
You can install RSAT-AD-PowerShell on more than just domain controllers. Any ordinary domain server or even workstation will do. The Active Directory PowerShell module is installed automatically when you deploy the Active Directory Domain Services (AD DS) role (when you promote a server to an AD domain controller).
The module communicates with AD through the Active Directory Web Service, which must be installed on your domain controller (communication is via TCP port 9389).
Possible problems
During the process of activating AD and RSAT, a number of difficulties may arise, for example, the option to run programs on behalf of another user is not activated in advance. In addition, we must remember that the remote control tool cannot be installed on a PC running on the Home or Standard version of Win 10. The RSAT tool can only be added to the Enterprise or Professional OS.
This tool is located on the Microsoft website. Developers offer programs for a specific version of Win 10. If the edition type is not specified, you need to use RTM (full release of Windows OS) to download RSAT.
In order to download additional components for working on a remote server, you do not need to look for special software. You can perform this action using the Add Features Wizard. It is recommended to add a backup domain controller in advance to prevent possible operational failures.
How to Install the Active Directory PowerShell Module from the Command Prompt
You can install the RSAT-AD-PowerShell module not only on Windows Server, but also on your workstations.
If you try to run the above PowerShell command:
Install-WindowsFeature -Name "RSAT-AD-PowerShell" -IncludeAllSubFeature
then you will receive an error message:
Install-WindowsFeature: The target of the specified cmdlet cannot be a Windows client operating system.
Moreover, no matter what edition of Windows you have: Home, Pro, Enterprise.
However, in Windows 10 build 1809 or later, the RSAT package is integrated into the Windows image (as Features on Demand), so you can use this PowerShell command to install the Active Directory module:
Add-WindowsCapability -online -Name "Rsat.ActiveDirectory.DS-LDS.Tools"
The previous command must be run in a command prompt with administrator rights.
Related Article: How to Run PowerShell as Administrator
How to Install Active Directory PowerShell Module on Windows 11 in GUI
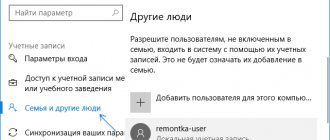
install the Active Directory PowerShell module in the GUI in Windows 11, open Settings by pressing Win +i and selecting the Apps tab , then going to Optional Features .
Now select “ View features ” in the “ Add an optional feature ” .
To install Active Directory remote administration tools, find “ RSAT: Active Directory Domain Services and Lightweight Directory Services Tools ” ( Remote Server Administration Tools: Active Director Domain Services and Lightweight Directory Services Tools ), check the box and click on the “ Next ” button ( Further ),
then click " Install " .
Note : If you cannot find it when searching for a particular component, then the component may already be installed.
To verify this, in the search bar under “ Installed features ” , enter the name of the component you are looking for.
Also remember that these components are called differently in English and localized versions of Windows!
How active directories work
The main operating principles are:
- Authorization, which makes it possible to use a PC on the network simply by entering a personal password. In this case, all information from the account is transferred.
- Security. Active Directory contains user recognition functions. For any network object, you can remotely, from one device, set the necessary rights, which will depend on the categories and specific users.
- Network administration from one point. When working with the Active Directory, the system administrator does not need to reconfigure all PCs if it is necessary to change access rights, for example, to a printer. Changes are carried out remotely and globally.
- Full DNS integration. With its help, there is no confusion in AD; all devices are designated exactly the same as on the World Wide Web.
- Large scale. A set of servers can be controlled by one Active Directory.
- The search is performed using various parameters, for example, computer name, login.
Objects and Attributes
An object is a set of attributes, united under its own name, representing a network resource.
Attribute - characteristics of an object in the catalog. For example, these include the user’s full name and login. But the attributes of a PC account can be the name of this computer and its description.
Processes Atieclxx, Atiedxx, Ati2evxx - why they are used and which utility they belong to
Example:
“Employee” is an object that has the attributes “Name”, “Position” and “TabN”.
LDAP container and name
A container is a type of object that can consist of other objects. A domain, for example, may include account objects.
Their main purpose is to organize objects by types of features. Most often, containers are used to group objects with the same attributes.
Almost all containers map a collection of objects, and resources are mapped to a unique Active Directory object. One of the main types of AD containers is the organization module, or OU (organizational unit). Objects that are placed in this container belong only to the domain in which they are created.
Lightweight Directory Access Protocol (LDAP) is the underlying algorithm for TCP/IP connections. It is designed to reduce the amount of nuance when accessing directory services. LDAP also defines the actions used to query and edit directory data.
Tree and site
A domain tree is a structure, a collection of domains that have a common schema and configuration, that form a common namespace and are linked by trust relationships.
A domain forest is a collection of trees connected to each other.
A site is a collection of devices in IP subnets, representing a physical model of the network, the planning of which is carried out regardless of the logical representation of its construction. Active Directory has the ability to create an n-number of sites or combine an n-number of domains under one site.
How to Install the Active Directory PowerShell Module on Windows 10 in a GUI
To install the Active Directory PowerShell module in the GUI, press Win+x , then select “Apps and Features” from the menu that opens .
Next, select “ Optional Features ” .
Now select “ Add a feature ” .
To install Active Directory remote administration tools, select “ RSAT: Active Directory Domain Services and Lightweight Directory Services Tools ” ( Remote Server Administration Tools: Active Director Domain Services Tools and Lightweight Directory Services Tools ) and click on the “ Install ” .
Active Directory PowerShell Cmdlets
The Active Directory module for Windows PowerShell has many cmdlets for interacting with AD. Each new version of RSAT contains more cmdlets than the previous one. There are 147 Active Directory PowerShell cmdlets available in Windows Server 2022.
Before you can use the Active Directory module cmdlets, you need to import it into your PowerShell session:
Import-Module ActiveDirectory
Starting with Windows Server 2012 R2, Windows 8.1 and later versions, the module is imported automatically.
If the Active Directory module is not installed on your computer, you can import it from your domain controller (you need domain administrator rights to do this) or from another desktop computer:
$psSess = New-PSSession -ComputerName COMPUTER_NAME Import-Module -PSsession $psSess -Name ActiveDirectory
In these commands, COMPUTER_NAME is the computer that is the Domain Controller, or the computer on which the Active Directory Powershell module is installed.
You can display a complete list of available Active Directory cmdlets using the command:
Get-Command -module ActiveDirectory
To count the total number of cmdlets in the AD module, run the command:
Get-Command -module ActiveDirectory | measure-object | select count
Most RSAT-AD-PowerShell cmdlets begin with the Get- , Set- , or New- .
- Get- cmdlets are used to obtain various information from Active Directory (Get-ADUser - user properties, Get-ADComputer - computer settings, Get-ADGroupMember - group membership, and so on). You don't need to be a domain administrator to run them. Any domain user can run PowerShell commands to obtain AD object attribute values (except sensitive ones, as in the LAPS example);
- Cmdlets of the Set are used to set (change) object parameters in Active Directory. For example, you can change user properties ( Set-ADUser ), computer settings ( Set-ADComputer ), add a user to a group, and so on. To do this, your account must have permissions to change object properties;
- Commands starting with New - allow you to create AD objects (create a user - New-ADUser , create a group - New-ADGroup);
- Remove cmdlets are used to remove AD objects.
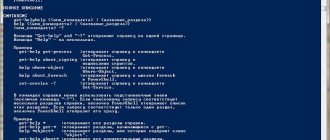
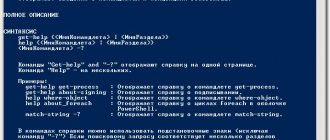
This is how you can get help for any cmdlet:
Get-Help COMMANDLET Get-Help COMMANDLET -Full
See also: How to get help with PowerShell commands
You can display examples of using Active Directory cmdlets as follows:
(Get-Help COMMANDLET).examples
Or:
Get-Help COMMANDLET -Examples
Tooltips are useful when entering cmdlet parameters in PowerShell ISE.
Device
Let's talk about the structure of the program.
Objects
Active Directory has a hierarchical structure consisting of objects. Objects fall into three main categories: resources (such as printers), services (such as email), and user and computer accounts. The service provides information about objects, allows you to organize objects, control access to them, and also sets security rules.
Objects can be stores for other objects (security and distribution groups). An object is uniquely identified by its name and has a set of attributes—the characteristics and data it can contain; the latter, in turn, depend on the type of object. Attributes form the basis of the structure of an object and are defined in the schema. The schema defines what types of objects can exist.
The schema itself consists of two types of objects: schema class objects and schema attribute objects. One schema class object defines one Active Directory object type (for example, a User object), and one schema attribute object defines the attribute that the object can have.
Each attribute object can be used in several different schema class objects. These objects are called schema objects (or metadata) and allow you to change and extend the schema whenever necessary and possible. However, each schema object is part of the object definitions, so disabling or changing these objects can have serious consequences because they will change the directory structure. A change to a schema object is automatically propagated to the directory service. Once created, a schema object cannot be deleted, it can only be disabled. Typically, all schema changes are carefully planned.
A container is similar to an object in that it also has attributes and belongs to a namespace, but unlike an object, a container does not stand for anything specific: it can contain a group of objects or other containers.
Structure
The top level of the structure is the forest - the collection of all objects, attributes and rules (attribute syntax) in Active Directory. A forest contains one or more trees linked by transitive trust relationships. The tree contains one or more domains, also linked into a hierarchy by transitive trust relationships. Domains are identified by their DNS name structures - namespaces.
Objects in a domain can be grouped into containers - divisions. OUs allow you to create hierarchy within a domain, simplify domain administration, and allow you to model, for example, the organizational or geographic structure of an organization in a directory service. Divisions may contain other divisions. Microsoft recommends using as few domains as possible in your directory service and using organizational units for structuring and policies. Often group policies are applied specifically to departments. Group policies are themselves objects. The division is the lowest level at which administrative authority can be delegated.
Another way of dividing is sites, which are a way of physically (rather than logical) grouping based on network segments. Sites are divided into those that have connections via low-speed channels (for example, via global network channels, using virtual private networks) and via high-speed channels (for example, via a local network). A website can contain one or more domains, and a domain can contain one or more websites. When designing a directory service, it is important to consider the network traffic generated when data is synchronized between sites.
A key decision when designing a directory service is the decision to divide the information infrastructure into hierarchical domains and top-level departments. Typical models used for such separation are models of separation by functional divisions of the company, by geographical location and by roles in the company's information infrastructure. Combinations of these models are often used.
Physical structure and replication
Information is physically stored on one or more equivalent domain controllers, replacing the primary and backup domain controllers used in Windows NT, although a so-called "single master operations" server, which can emulate a primary domain controller, is retained for some operations. Each domain controller maintains a read-write copy of the data. Changes made on one controller are synchronized to all domain controllers during replication. Servers that do not have Active Directory installed, but are still part of an Active Directory domain, are called member servers.
Directory replication occurs on demand. The KCC (Knowledge Consistency Checker) service creates a replication topology that uses sites defined in the system to control traffic. Intrasite replication occurs frequently and automatically using a consistency checker (notifying replication partners of changes). Cross-site replication can be configured on a per-site link basis (depending on link quality) - a different "score" (or "cost") can be assigned to each link (e.g. DS3, T1, ISDN) and replication traffic will be limited to be transmitted scheduled and routed according to the assigned link estimate. Replication data can transit across multiple sites via site link bridges if the score is low, although AD automatically assigns a lower score to site-to-site links than to transit links. Site-to-site replication is performed by bridgehead servers at each site, which then replicate changes to each domain controller in its site. Intra-domain replication uses the RPC protocol, while inter-domain replication can also use the SMTP protocol.
If the Active Directory structure contains several domains, a global catalog is used to solve the task of searching for objects: a domain controller that contains all the objects in the forest, but with a limited set of attributes (incomplete replica). The catalog is stored on specified global catalog servers and serves cross-domain requests.
Single-host capability allows requests to be processed when multi-host replication is not possible. There are five types of such operations: master domain controller emulation (PDC emulator), relative identifier master (relative identifier master or RID master), infrastructure master (infrastructure master), schema master (schema master), and domain naming master. (domain naming wizard). The first three roles are unique within the domain, the last two are unique within the entire forest.
The Active Directory database can be divided into three logical stores or "partitions". The schema is the template for the service and defines all types of objects, their classes and attributes, attribute syntax (all trees are in the same forest because they have the same schema). The configuration is the structure of the Active Directory forest and trees. A domain stores all information about objects created in that domain. The first two stores are replicated to all domain controllers in the forest, the third partition is fully replicated between replica controllers within each domain and partially replicated to global catalog servers.
Database (directory storage) in Windows 2000 uses the Microsoft Jet Blue extensible storage subsystem, which allows each domain controller to have a database of up to 16 terabytes and 1 billion objects (theoretical limit, practical tests were performed with only approximately 100 million objects ). The database file is called NTDS.DIT and has two main tables - a data table and a links table. Windows Server 2003 added another table to ensure that security descriptor instances are unique.
Get-ADComputer: Get computer properties
To display computer property information for a specific organizational unit (computer name and last logon date), use the Get-ADComputer :
Get-ADComputer -SearchBase 'OU=CA,OU=USA,DC=ds,DC=hackware,DC=ru' -Filter * -Properties * | FT Name, LastLogonDate -Autosize
See also "Get-ADComputer: Find information about computers and filter computers by their properties in Active Directory."
Functions and purposes
Microsoft Active Directory – (the so-called directory) a package of tools that allows you to manipulate users and network data. The main purpose of its creation is to facilitate the work of system administrators in large networks.
Directories contain various information related to users, groups, network devices, file resources - in a word, objects. For example, the user attributes that are stored in the directory should be the following: address, login, password, mobile phone number, etc. The directory is used as an authentication point , with which you can find out the necessary information about the user.
Add-AdGroupMember: add AD user to groups
To add users to an existing security group in your AD domain, run this command:
Add-AdGroupMember -Identity LondonSales -Members e.braun, l.wolf
Display a list of users in an AD group and export it to a CSV file:
Get-ADGroupMember LondonSales -recursive | ft samaccountname | Out-File c:\ps\export_ad_users.csv
In the previous command, " ft " is the Format-Table .
See also: Managing Active Directory Groups Using PowerShell
Basic concepts encountered during work
There are a number of specialized concepts that are used when working with AD:
- Server is a computer that contains all the data.
- The controller is a server with the AD role that processes requests from people using the domain.
- An AD domain is a collection of devices united under one unique name, simultaneously using a common directory database.
- The data store is the part of the directory responsible for storing and retrieving data from any domain controller.
New-ADOrganizationalUnit: Create an organizational unit in AD
To quickly create a typical OU structure in AD, you can use a PowerShell script. Let's say you want to create several OUs with state names and create typical object containers within them. Creating this AD structure manually using the ADUC graphical snap-in takes quite a lot of time. The AD module for PowerShell allows you to do this in seconds (except for the time it takes to write a script):
$fqdn = Get-ADDomain $fulldomain = $fqdn.DNSRoot $domain = $fulldomain.split(“.”) $Dom = $domain[0] $Ext = $domain[1] $Sites = (“Nevada”,” Texas","California","Florida") $Services = ("Users","Admins","Computers","Servers","Contacts","Service Accounts") $FirstOU ="USA" New-ADOrganizationalUnit - Name $FirstOU -Description $FirstOU -Path "DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false ForEach-Object ($S in $Sites) { New-ADOrganizationalUnit -Name $S -Description "$S" -Path "OU=$FirstOU,DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false ForEach-Object ($Serv in $Services) { New-ADOrganizationalUnit -Name $Serv -Description "$S $Serv" -Path "OU =$S,OU=$FirstOU,DC=$Dom,DC=$EXT" -ProtectedFromAccidentalDeletion $false } }
After running the script, the following organizational unit structure appears in Active Directory.
What is AD delegation
Delegation itself is the transfer of some of the permissions and control from a parent object to another responsible party.
It is known that every organization has several system administrators at its headquarters. Different tasks should be assigned to different shoulders. In order to apply changes, you must have rights and permissions, which are divided into standard and special. Specific permissions apply to a specific object, while standard permissions are a set of existing permissions that make specific features available or unavailable.
Ways to remove the Recycle Bin from your desktop
Establishing trust
There are two types of trust relationships in AD: "unidirectional" and "bidirectional". In the first case, one domain trusts the other, but not vice versa; accordingly, the first has access to the resources of the second, but the second does not have access. In the second type, trust is “mutual”. There are also “outgoing” and “incoming” relationships. In outgoing, the first domain trusts the second, thus allowing users of the second to use the resources of the first.
During installation, the following procedures should be followed:
Source
Get-ADDomainController: Retrieving information about domain controllers
To get information about all domain controllers in a domain, use the Get-AdDomainController cmdlet:
Get-ADDomainController -filter * | select hostname,IPv4Address,IsGlobalCatalog,IsReadOnly,OperatingSystem | format-table -auto
So, we looked at the main features of the Active Directory PowerShell module for administering an AD domain. I hope this encourages you to continue exploring other features of the module and automate more of your AD management tasks.
Connecting the ADUC console to a domain from a workgroup
If you want to connect the ADUC console to a domain controller from a computer that is not included in the domain (part of a workgroup), use this method:
- Start the command line and run the command to run the snap-in as a different user: runas /netonly /user:winitpro\aaivanov mmc
- In an empty MMC console, select File->Add/Remove Snap-In
- Move the Active Directory Users and Computers snap-in to the right pane and click Add;
- To connect to a domain, click on the console root and select Change domain. Enter your domain name.
As a result, the ADUC console will connect to the domain controller, receive and display the container structure (OU) of this Active Directory domain.