For more than 10 years of its existence, Android has gained a reputation as far from being the most secure operating system. After all, if it is in principle impossible to imagine infecting an iPhone, then clearly no one will be surprised if a device based on Google’s mobile OS gets a virus. In many ways, this attitude towards the platform has developed due to Google’s policy, which allows Android users to install software from any sources whose security may raise questions. But since I have never been attacked by malware, I decided to figure out what I was doing wrong and why I was so “unlucky” all the time?
Android is invulnerable to viruses, no matter what anyone says
Reduce screen lock time
A simple measure that will ensure the safety of your gadget is a simple screen lock. Configure this function so that the time before turning off the smartphone is minimal. However, if your phone is too easy to activate, locking it alone won't protect it.
The unlock code should be as secure as possible: do not use a pattern, but come up with a PIN code. It is desirable that it contains not 4, but 6 digits. If your smartphone has a fingerprint scanner or facial recognition, don't ignore these features.
How to protect Android: 10 tips for maximum security
Well, it’s easy to make a dozen iOS settings to improve the security of your mobile pet. But what to do with Android? The trouble is that Android seems to be the same, but at the same time very, very different. The fairly high openness of the platform allowed it to quickly become a leader in the mobile device market, but it gave rise to the notorious fragmentation, which they like to mention at every opportunity.
Let's say, Android on a Nexus device, on a Samsung/Sony/HTC smartphone and on some unknown "Chinese" device - these are two big differences. Nevertheless, some general tips can be given to improve the security of this OS, and some of them completely coincide with the recommendations for iOS. Of course, you will have to put up with certain inconveniences in your daily work, but here you will have to follow the universal rule - either comfort or safety. In the end, you can use only part of the recommendations and find the optimal balance of convenience and protection for yourself.
1. Get applications only from Google Play Store and Yandex.Store
Yes, yes, the most “dangerous” part of Android is not the OS itself, but the programs for it.
Unlike iOS, installing an application (either on your own or at the behest of an attacker) on Android is easy. Never download programs from unofficial sites or third-party sites, as they may be infected. It is best to completely disable the ability to install software from third-party sources and enable built-in application scanning. Also, you should not do root access, as this significantly increases the level of risk. How it will help:
it will dramatically reduce the threat of catching some kind of malware.
Where to set it up:
go to “Settings” -> “Security”, uncheck “Unknown sources” and check “Scan applications”.
2. Monitor what apps are allowed
First, you should install applications from well-known developers or those recommended by Google.
Secondly, before installing, you must check
what the application is going to access.
For example, a program for changing wallpaper or a toy that requires access to accounts, SMS, microphone, location and unlimited Internet access looks extremely suspicious. How it will help:
reduce the threat of contracting malware.
Where to configure:
when installing an application, a list of required permissions is always displayed + on the program page at the very bottom there is a “View permissions” item. Also, don’t forget to view the lists and permissions of applications connected to Google. In the list of programs you need to find “Google Settings” -> “Connected applications” and disable unnecessary ones.
3. Use strong passwords
Universal, but never superfluous advice.
To unlock the screen, it is better to set a really complex password and not use a pattern or PIN code. The password, as usual, must consist of at least ten characters. Ideally, it should include letters in different cases, numbers and other characters. But it’s better not to make the password too complicated, otherwise you’ll quickly get tired of entering it. It is useful to change your password periodically. It is also worth setting the minimum possible screen auto-lock interval and disabling the display of any passwords when entering. In addition, many applications allow you to set password protection. How it will help
: significantly reduce the chance of gaining access to the smartphone and its contents.
Where to set it up
: go to “Settings” -> “Security” -> “Screen Lock” and select “Password” as the screen lock method. Then go to “Settings” -> “Security”, uncheck “Show passwords”.
4. Encrypt your data
Everything is simple here!
If the information on the phone is encrypted, then even if it is lost, the data will not fall into the wrong hands. For protection, it is better to set a password rather than a PIN code. You will have to enter it every time you turn on the device. In current versions of Android, the strength of encryption depends only on the strength of the password - until Android 5.0 appears, this will have to be kept in mind. How it will help
: protect your data in case of loss of the device.
Where to set it up
: go to “Settings” -> “Security” -> “Encrypt phone”, you should also check the “Encrypt SD card” checkbox.
5. Monitor Wi-Fi connections
Android by default tries to connect to wireless networks that you have connected to.
It may well turn out that instead of a familiar open access point, it will turn out to be a hotspot with the same name, created by an attacker. Therefore, firstly, you should avoid public hotspots and, secondly, you should regularly clear the list of remembered Wi-Fi networks. At the same time, it is recommended to disable forced tracking of wireless networks. How it will help
: reduce the risk of unnoticed connection to a potentially dangerous Wi-Fi network.
Where to set up
: go to “Settings” -> “Wi-Fi”, long pressing on the name of the remembered network will bring up a menu where you can delete the network; In the same place, in the “Advanced settings” section, you need to uncheck the “Always search for networks” checkbox.
6. Always use a VPN
This advice is especially relevant when using open access points anywhere in a public place or on any untrusted networks.
Using a VPN will protect the transmitted data, and as a nice bonus, it will help you bypass possible bans on access to certain resources. Today, access to a reliable VPN is not that expensive, and some modern home routers have their own VPN servers, so in this case the connection will be completely free. Just keep in mind that it is better to use L2TP or OpenVPN - these protocols provide better security than the popular PPTP. To prevent any data from leaking out before the VPN connection is established, it would be a good idea to either disable auto-synchronization of applications or (which is better) configure forced use of the VPN. How it will help
: protect transmitted and received data.
Where to set it up
: go to “Settings”, in the “Wireless Connections and Networks” section, select “More…” -> VPN; after setting up one or more VPN connections, the only item “Permanent VPN” will appear in the menu, where you can select the connection to be used forcibly; Auto-sync can be disabled in the “Settings” -> “Accounts” section.
7. Turn off notifications
Even when the screen is locked, various notifications can be displayed both in the status bar and directly on the smartphone display.
These may include one-time codes for transactions, account status notifications and other confidential data. Unfortunately, Android does not have a single notification center where they could be turned off in one fell swoop. In addition, many manufacturers install a variety of shells, which may also not be very safe from this point of view. Therefore, you will have to manually turn off notifications in applications. How it will help
: strangers will not be able to see notifications that may contain important information.
Where to set it up
: go to “Settings” -> “Applications”, select the desired program and uncheck “Show notifications”. Sometimes it's easier to turn off notifications in the settings of the program itself.
8. Set up Google services
The Good Corporation wants to know as much as possible about its users, and its appetites are growing every year.
It makes sense to slightly reason with the search giant in its desires, since leaking access to your Google account entails very sad consequences - attackers will be able to not only read your messages, but also find out where and when you were, view your photos and contacts, and a lot more. How it will help
: reduce losses in case of Google account theft.
Where to set it up
: in the “Google Settings” application, in the “My Location” section, disable the “Sending geodata” and “Location History” options for all accounts, in the “Search and Hints” section, disable Google Now, in the “Android Remote Control” section, if desired enable the “Remote device search” and “Remote lock and reset” options; In the Google Photos application, go to Settings -> Startup and disable the automatic sending of all photos taken to Google servers.
9. Get rid of unnecessary apps
In essence, this is a continuation of points 1 and 2. The more programs there are, the higher the chance that some of them will engage in dishonest activities.
In addition, in the Android world there is a vicious practice when a smartphone manufacturer preinstalls a huge number of third-party applications and services. Even if you don't use them, this does not mean that their developers are not using you for any of their purposes. Some of them can be removed, although not all. Which services can be safely disabled can be easily found on the Internet. How it will help
: minimizing losses in the event of a data leak.
Where to set it up
: go to “Settings” -> “Applications” -> “All”, tap on the unnecessary application in the list and click the “Erase data” and “Turn off” buttons.
Hot ten best security settings for #Android from @Kaspersky_ru
Tweet
10. Enable two-step verification for Google and other apps
Two-factor authentication is perhaps the only method today of sufficiently reliable protection of any accounts.
It works quite simply - in addition to entering a password, you are required to provide a temporary one-time code, which can be received via SMS or using special applications or even devices. Without this code, an attacker, even if he knows your password, will not be able to log into your account and cause trouble. How it will help
: dramatically reduce the possibility of using accounts by strangers.
Where to configure
: go to the page https://accounts.google.com/SmsAuthConfig in your browser and follow further instructions.
The above tips will help significantly improve Android security, but they still won’t save you from many misfortunes. Therefore, do not be lazy to install a software package from well-known developers of antivirus solutions on your smartphone. In addition to the antivirus itself, they usually offer many other degrees of protection - secure web surfing, a password manager, SMS and call filtering, anti-theft functions, and so on.
And most importantly, never let your guard down!
Back up your data
Backing up your data should become a good habit. On the one hand, a backup will help if you lose your smartphone. On the other hand, such a backup will be useful if you remotely deleted data from your smartphone and then found it again. In addition, copied files can be easily transferred to a new device.
Kaspersky Internet Security for Android
Along with Avast, Kaspersky is popular. Unfortunately, the free version of the application misses many threats during the scan, which is why it cannot be called an optimal defender. However, after subscribing, all the shortcomings fade into the background.
If we put aside the fact that Kaspersky takes up a lot of space in the internal memory, only advantages remain. These include constant updates to the virus database, online scanning, a level of protection, and a familiar interface without unnecessary tabs.
Update your system regularly
System updates play an important role in the security of any gadget. If such an update is available, don't hesitate to install it or not, just do it. Updates not only add new features, but also fix bugs from previous versions. Sometimes updates also include improvements to security systems that protect your smartphone.
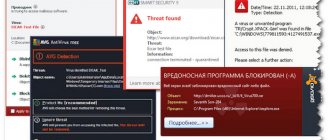
How Trojans get onto smartphones
Most users download Trojans to their smartphones themselves
But what about the malicious components that are automatically distributed through websites and instant messengers? Well, everything is simple with them. Despite the fact that the role of their distributors is often played by messaging applications or web resources, in order for them to reach the device, the user must still confirm their download. For example, as was the case with the malicious video that Jeff Bezos, the founder of Amazon, received. The video actually reached him via WhatsApp, but if the entrepreneur had not confirmed the playback, he would not have been able to harm him.
Download apps only from trusted sources
Do not download applications from dubious sites: use only official sites such as the App-Store or Google Play. However, you shouldn’t download everything here either. Pay attention to how many downloads and ratings an app has and read the list of required permissions. If an app requires too much, stay away from it.
What are Trojans and what are their dangers?
Programmers and advanced users know that a virus called a Trojan is disguised as a regular program. Often the application works so that the owner of the smartphone or tablet does not suspect anything. However, the main task of such software is to obtain all the information from the gadget. Hence the name - Trojan (Trojan horse).
There are two types of such viruses. Some gain access due to the ignorance and inattention of the user who grants software permissions to SMS messages, gallery, camera, etc. The second type looks for vulnerabilities in the Android operating system, then exploits the flaw for its own purposes. For example, to gain access to confidential data.
The main problem is that the owner of a smartphone often does not even suspect the presence of viruses in the device’s memory. So, for example, when an attacker connects to an application from a bank, the user finds out about it after losing money. In addition, Android phones and tablets rarely have antivirus installed. Moreover, if a person does not know about the existence of Trojan programs.
Important: Antiviruses can also be malicious. Download only common software from reputable sources.
It is difficult to protect yourself from viruses that “ask” the user for access to device functions. The software uses the normal capabilities of the device. For example, “pure” photo processing software requires permission to open a gallery. It is important to read the information in the pop-up windows. In the Android OS, some utilities request access to toll calls. This is a common scam: the attacker makes calls at the victim's expense.
What can infection of a smartphone lead to? It depends on the specific virus. The problem can be of different scales: from controlling the camera and microphone to writing off all the money from the bank account.
Give up root rights or jailbreak
Some applications can only be used after jailbreak or root because they require administrator rights. However, this process not only gives you more rights, but also removes important security measures. Think carefully about what is more important to you—security or additional features.
ESET Mobile Security & Antivirus
An advanced defender, leading the ratings in many respects. ESET Mobile Security & Antivirus is not only highly rated by users, but also boasts a lot of objective advantages. These include simultaneous protection of up to 5 devices from one account, custom message settings and the function of creating automatic selfies in a situation when the phone falls into the hands of another person.
The antivirus copes with its direct responsibilities perfectly. However, to conduct a deep scan you will need to subscribe. You can use ESET Mobile Security & Antivirus for free only for 30 days, after which you will have to either look for a replacement or still pay for Pro access.