If you know that you have parental controls installed on your smartphone, contact the person who installed them to unblock the installation of applications. However, in some cases, the same message may also appear in the scenarios described in the section above: if there are no parental controls, and you receive the message in question that the action is prohibited, try going through all the steps with disabling device administrators.
The installation of Android applications, both from the Play Store and in the form of a simple APK file downloaded from somewhere, can be blocked, and depending on the specific scenario, different reasons and messages are possible: that the installation of the application is blocked by the administrator, that the installation of applications from unknown sources, information from which implies that the action is prohibited or that the application was blocked by Play Protection.
In this instruction, we will look at all possible cases of blocking the installation of applications on an Android phone or tablet, how to correct the situation and install the desired APK file or something from the Play Store.
- For security reasons, installation of applications from unknown sources is blocked on the device.
- Application installation blocked by administrator
- Action prohibited. The function is disabled. Contact your administrator.
- Blocked by Play Protection
Download Smart AppLock from Play Store
How to set a time limit on an application?
How to limit time in apps
- Say "Hey Google" or press and hold the Home button on your Android phone.
- Say or enter a command for the application timer. For example: Set the timer for [app] to 15 minutes. Set a timer for 30 minutes for [app].
Interesting materials:
Where do many Russians live in Germany? Where does the herbalist live in the white garden? Where do Angora rabbits live? Where do they live the longest? Where do English speakers live? Where do bees live in nature? Where do Russians live in Cyprus? Where do Russians live in America? Where do Russians live in Bulgaria? Where do Russians live in Turkey?
Standard ways to disable blocking
Firstly, it should be noted that the specific method of unlocking directly depends on how exactly you set the password. That is, if restrictions were set by the phone’s built-in tools, then they are removed through the device settings. Things are a little different when program security is activated through third-party software. But more on that a little later, but for now let’s focus on standard methods.
The interface of Android devices differs depending on the specific model. Therefore, the names of some menu items in the instructions below may differ. As an example, let’s take the principle of deactivating protection on Xiaomi smartphones, which, according to statistics, are the most popular:
- Open your phone settings.
- Go to the "Applications" section, and then - "Application protection".
- Enter the previously set password or pattern.
- Move the slider in the opposite direction.
In a similar way, you can disable the password on Meizu, Huawei and Honor smartphones. But on Samsung the function is implemented differently. South Korean devices block applications not individually, but as a whole. All programs added to the protected folder are protected. Therefore, to disable such a security feature, you must go to the “Secure Folder” settings section.
Removing system files
This method is suitable for devices with root rights (which means increased access, allowing you to edit files from root folders). You can delete files that are responsible for blocking your smartphone.
- To do this, you will need a file manager that supports root rights (Aroma as an example). To use it, download it to your PC, and then transfer it to your phone without removing it from the archive (remember the transfer folder).
- Now you need to get into Recovery. Turn off your phone and hold down the button combination. It may be different for each phone model, but here are a few basic ones: Volume Up + Power On, Volume Down + Power On, Volume Up + Power On + Home Screen, Volume Down + Power On + Home Screen.
- Next you will be taken to CWMRecowery, here select “InstallZip”. Navigating through the menu can be either touch or done using the same keys.
- Now select “Choosezipfrom /sdcard” and include the directory where the manager was previously dropped. You can also select “Choose zip from last install folder” where you will see the files downloaded to your phone recently. Find and run the archive.
- In the program, follow the path /data/system/ and get rid of these files: gesture.key, password.key, locksettings.db, locksettings.db-wal, locksettings.db-shm.
- Restart your phone and, if prompted, enter any password.
AppLock IvyMobile - Will confuse all traces
IvyMobile's AppLock allows you to lock almost everything on your device. In addition to all third-party applications, it will also allow you to protect contacts, gallery, settings, email and so on. Moreover, to unlock, you can also “shuffle” the keyboard for input. Let's say you can swap some numbers, but they will be displayed in the old place. Why is this necessary? Well, for example, it is useful to enable this option in public places, and then even if an attacker sees that you have entered a password, he will not recognize it, since he will remember the wrong sequence
Download: AppLock IvyMobile
Tracing paper for iOS
Google's innovation will make Android more similar to iOS, Apple's competing mobile platform. Installing applications from third-party sources has been prohibited since the very first days of the App Store, Apple’s proprietary marketplace launched in the summer of 2008.
Bypassing these restrictions is only possible by jailbreaking - hacking iOS to gain access to the file system of Apple mobile devices. You can even jailbreak gadgets running iOS 13.3, the latest stable version of Apple’s mobile OS.
After hacking, it becomes possible to install applications on iPhone and iPad from third-party stores, including the most famous - Cydia. It was scheduled to close at the end of 2022, but is still in operation as of March 2022.
With the release of Android 8 Oreo, the function of installing applications from unknown sources (installing an application from an APK file) has changed. We have already looked at installing applications from unknown sources in Android 8, today we will look at this process in Android 9.
Receive a notification that you need to change your password
There are various services designed to notify you when you need to change your password. These are applications that can be downloaded to a laptop or smartphone:
- PCNS;
- Powershell.
They are programmed in such a way that when an outdated cipher appears, the user is notified of the need to change it.
Powershell for encryption
It is also permissible to use the special Interactive Logan policy, which can be found through the search or the Security options section. The policy is characterized by the following features:
- connecting the function through local settings of the Windows operating system;
- notifications appear 5 days before the expiration date;
- the ability to change the notification period to any number of days;
- the appearance of an inscription that is translated in English “Consider changing your password”.
If you use this function in a timely manner, all data will remain safe.
Notification about cipher change
Use of third party software
If the code was installed through third-party software, then removing the password will be equally easy on devices from different manufacturers. However, it all depends on which utility was chosen to block applications. Let's look at the principle of deactivation via AppLock:
- Launch the program.
- Enter your PIN.
- Go to the "Applications" tab.
- Move the slider located next to specific programs to the left.
- Save your changes.
You can also get rid of the lock by simply removing AppLock or any other similar software from your phone. However, depending on which programs the password was set for, the system may require you to enter a security code. This is done to ensure that an attacker cannot bypass the protection, thereby gaining access to the owner’s personal data.
Getting ready
To perform the steps described in this article, you will need a number of tools, and the main tool is Linux. Yes, many of the programs mentioned below can work on Windows, but for any operations related to Android and its applications, it is better not to rely on Billy's brainchild. In Linux, almost everything is easier to do, the command line is much more convenient here (we will need it so much), and some tools are simply not available for other OSes.
After installing Linux in a virtual machine or a second system, we immediately install development tools for Java and the virtual machine. On Ubuntu this can be done with one command:
$ sudo apt-get install openjdk-7-jdk
We also need four tools for unpacking and decompiling applications:
- Apktool - a Swiss army knife for unpacking and packing applications;
- Jadx - decompiler of Dalvik bytecode into Java code;
- Backsmali is a disassembler for Dalvik code (don’t be alarmed, it has little in common with a real assembler);
- Sign is a utility for signing packages.
For convenience, let's create an Android subdirectory in our home directory and download these tools into it:
$ cd ~ $ mkdir ~/Android && cd ~/Android $ wget https://bitbucket.org/iBotPeaches/apktool/downloads/apktool_2.2.0.jar $ wget https://github.com/skylot/jadx/releases/ download/v0.6.0/jadx-0.6.0.zip $ wget https://github.com/appium/sign/raw/master/dist/sign.jar $ wget https://bitbucket.org/JesusFreke/smali/ downloads/baksmali-2.1.3.jar $ mkdir jadx && cd jadx $ unzip ../jadx-0.6.0.zip
Add the following lines to the end of the ~/.bashrc file:
alias apktool='java -jar ~/Android/apktool_2.2.0.jar' alias jadx-gui='~/Android/jadx/bin/jadx-gui' alias baksmali='java -jar ~/Android/baksmali-2.1. 3.jar' alias sign='java -jar ~/Android/sign.jar' alias javac='javac -classpath /home/j1m/Android/android-sdk-linux/platforms/android-23/android.jar' alias dx='/home/j1m/Android/android-sdk-linux/build-tools/23.0.3/dx'
They are needed so that instead of long and inconvenient commands like java -jar ~/Android/sign.jar you can simply type sign .
Checking passwords for strength
If your device contains a folder of saved data, it is important to check its security and privacy. This is especially true in cases where a weak encryption is installed, which can be easily opened and private information taken away.
Google's browser includes a free feature to check for weak codes or hacked data.
To implement the options, perform step-by-step actions:
- Go back to the Password Manager program.
- Click on the “Check” button, then “Go to the verification page”.
- A menu appears where you read the information and click on the “Continue” button.
- To confirm your identity, scan your fingerprint or use a saved key.
- The system independently checks the data; if any of it has been stolen, it notifies you about it.
- To eliminate the risks, click on the “Password has been stolen. Change it now."
- A new menu will appear where you need to confirm the actions by clicking “Change”.
- Using the keys, new keys are indicated.
Often, data loss occurs due to the fact that a person uses the same keys for different sites and programs. You can use Google's generator, which will come up with a combination on its own.
Application of the generator
The generator operates according to the following scheme:
- arbitrary creation of a combination of a cipher consisting of capital and small letters, numbers;
- receive information that is difficult to hack or remember.
To avoid forgetting the generated data, use a dispatcher. If you want to see them, you can get inside at any time.
Password Vault for Android
And in conclusion, we will give one more useful advice. To prevent passwords from being forgotten in the future or stolen by an attacker, you should store them using programs such as “KeePas Droid” and “Safe”.
If you don't mind the full screen, you can use these features for free. For even greater security, you will find the "Advanced Protection" menu item in Settings. This way, unauthorized users cannot uninstall the app without opening it first and entering the password you set. To do this, in the menu you will find a remote lock password, which can be sent to your mobile phone in case of loss or theft. The application opens a false error message when opening certain applications. Thus, the unauthorized user believes that the application has crashed. The option can be activated using the application on the right edge for each application.
- For 69 cents per month, ads can be removed with an in-app purchase.
- In the “Settings” menu item you define a password.
This way you won't forget your access details.
How to bypass the lock if you forgot your password?
Do not miss:
- What is recovery on Android: how to go to the menu and what can you do there?
- How to reset settings on Android to factory settings. All the ways and why you need it
- Google play services error: what are they and instructions on what to do
If you recently changed your password and immediately forgot it, then to reset you need to enter Recovery mode.
To do this, you need to simultaneously hold down the power button and change the volume. These keys must be pressed when the phone is turned on.
From the menu that appears, you need to select factory reset. In most cases, you won't have to enter a key after your device boots up. This method has a negative side - you will lose all user files, you will have to reinstall the applications. You can restore information only if you have synchronized your device with cloud storage.
For smartphones of recent years, this method may not work - you will still have to enter the key after reverting the settings. Also ineffective are the options in which the lock is removed during a call or when the battery charge is low. They only worked on systems up to version 4, and later this vulnerability was closed by the developers. You can still answer the call without unlocking your smartphone, but to go to messages or menus you will need to enter a code.
If you have a smartphone of one of the latest Android models, then you can reset a forgotten key only by flashing the device. If you are an inexperienced user, it is best to do this at a service center. To change the firmware, you will need to connect your smartphone to your computer, download a special program and a file with factory settings.
Making changes
The hasPrime() method is very simple: it returns the value of the mHasPrime field, which is of type boolean. It is easy to assume that if the application is paid, hasPrime() will return true, otherwise it will return false. Our goal is to make sure that the method always returns true and the rest of the application thinks that the application is paid for and unlocks additional options in the settings window.
Unfortunately, this cannot be done by directly editing the source code: the application cannot be compiled back. However, no one forbids disassembling the code, making changes and reassembling it. And this is where we need apktool. Let's disassemble the APK:
$ apktool d -r asap.apk
An asap subdirectory will appear in the current directory. Open the file asap/smali/com/citc/asap/fragments/BaseBillingFragment.smali and find hasPrime(). The method declaration will look like this:
.method protected hasPrime()Z .locals 1 .prologue .line 167 iget-boolean v0, p0, Lcom/citc/asap/fragments/BaseBillingFragment;->mHasPrime:Z return v0 .end method
This is a disassembled listing, and, as you can see, it is an order of magnitude simpler than the disassembled code of native applications. In general, everything here is trivial:
- .method protected hasPrime()Z - declares a protected method that returns a value of type boolean (Z);
- .locals 1 - tells the virtual machine that the method uses one register in its operation (in this case it will contain the return value);
- .prologue and .line 167 - directives necessary for debugging do not affect the execution;
- iget-boolean v0, p0 ... - gets the value of a boolean field and writes it to the v0 register, the p0 register is a zero parameter, it is always equal to the class name (this);
- return v0 - returns the value of register v0;
- .end method - closes the body of the method.
Now we must change this method so that it returns true regardless of the value of the mHasPrime field. We could do this manually, but it's easier to write a new method in Java:
public class Test { public boolean hasPrime() { return true; } }
And run it through the compiler and disassembler:
$ javac Test.java $ dx —dex —output=Test.dex Test.class $ baksmali Test.dex
The output is the following assembly code:
.method protected hasPrime()Z .registers 1 const v0, 1 return v0 .end method
You should already have guessed that it declares the constant v0 with the value 1 and returns it (in Dalvik, the boolean type is int, which can have the value 1 - true or 0 - false). All that remains is to insert this code instead of the original one and assemble the package back:
$ apktool b asap
The package will appear in the asap/dist directory. Let's rename it so as not to get confused:
$ mv asap/dist/asap.apk asap-fake-hasPrime.apk
And sign with the test key:
$ sign asap-fake-hasPrime.apk
As a result, the file asap-fake-hasPrime.s.apk . All that remains is to put it on the memory card and install it, first deleting the original application.
| ASAP Launcher settings up to... | ...and after manipulation |
Opening up the test subject
Now we need to find an application that, firstly, is not difficult to pick out, and secondly, which provides some benefit and is well known. That is, we will not take the simplest software just so that it is not very difficult to understand its code, but instead we will direct our attention to the top Play Store. An almost ideal candidate for this role is ASAP Launcher, released two months ago, a convenient home screen with a lot of useful and extraordinary functions.
First, let's go through the APK without using special tools. To do this, download the package using the APKPure service: open the application page in the Play Store, copy the URL from the address bar and paste it into the search bar on APKPure. Next, click the Download APK button and wait for the download to complete.
ASAP Launcher page on APKPure.com
For convenience, let's rename the package to asap.apk:
# cd ~/Downloads # mv ASAP Launcher_v1.16_apkpure.com.apk asap.apk
Unzip using unzip:
# mkdir asap; cd asap # unzip asap.apk
Yes, the APK is a regular ZIP archive, but nevertheless it has a clear structure:
- META-INF is the directory containing the MANIFEST.MF, CERT.MF and CERT.RSA files. The first two are a list of all package files and their checksums, the latter contains the developer's public key and the digital signature of the CERT.MF file created using the private key. This data is needed so that when installing the package, the system can find out that the package has not been modified and was actually created by its author. This is important because, since there is no way to forge the digital signature of a package (this requires a private key), the modified package will have to be signed with a different key;
- res — application resources. Here you can find the icon (mipmap), line breaks (values), images (drawable), and descriptions of the application interface (layout). All of them can be modified to change the appearance of the application. However, XML files will have to be “compressed” first - to improve performance they are stored in a binary format;
- classes.dex - application code in the form of Dalvik virtual machine bytecode. Applications typically contain only one such file, but by using the multiDex directive, the developer can force the development environment to split it into many smaller ones to improve performance or overcome the limit of 65,536 methods in a single dex file;
- AndroidManifest.xml is an application manifest that describes its structure, including activities, services, intent handlers, and so on. Again in binary XML format.
The package may also contain other directories, such as assets (any files included by the developer, in this case fonts and a database) and lib (native libraries built using the Android NDK).
Disabling a password using a PC
Now about the most difficult, but also the most effective method - how to reset a password on Android via a computer. To operate, you will need a cord, a PC and a special ADB Run program. This is an option for any device, including those without root.
Detailed instructions
The task is implemented in the following sequence:
- Download the Android SDK archive from the official website and unpack it on your PC. You can’t download just ADB, so you download the entire Android Studio.
- Place the platform-tools folder in the root (drive C) and rename it to ADB for convenience.
- Connect your smartphone to your PC via a USB cable.
- Enter the command line (Start menu, execute or find cmd, then press Enter) and enter the adb shell command
cd /data/data/com.android.providers.settings/databases
sqlite3 settings.db
update system set value=0 where name='lock_pattern_autolock';
update system set value=0 where name='lockscreen.lockedoutpermanently';
.quit and then press Enter.
The password will disappear after rebooting the device. If the device is rooted and has a custom Recovery, you can do the following:
- Download the Aroma file manager (on PC) without unpacking the archive. In principle, you can use any other one, it’s just that this one works with graphic files and is suitable for bypassing a graphical password.
- Connect the gadget to the PC.
- Copy the downloaded archive to the Android memory card.
- Turn off the gadget.
- Log in to Recovery and select archive installation (Install zip).
- Select installation from SD card.
- Find and indicate the downloaded archive. The file manager will launch.
- Open the data/system folder, where you can find and delete the password.key file.
After rebooting the gadget, the password will be lost. In the same way, you can remove the password on an Android tablet. Well, flashing the firmware will completely update the operating system, and the password will not be enabled by default. But this work is not for dummies and requires more knowledge and time.
Checking the security of saved passwords
The user needs to know not only where passwords are stored on Android, but also how to check their security. This will allow you to perform the following functions:
- identifying information that is easy to discover;
- timely detection of data leaks.
To assess the degree of safety, perform the following steps:
- Open the Chrome browser.
- Click on the 3-dot icon and select “Settings”.
- Sequentially select the “Passwords” and “Check” options.
The program scans the operating system, identifying possible information leaks or simple ciphers that are easy to crack.
Sign in to Chrome
Application installation is blocked by the device administrator on an Android phone or tablet
Second scenario: when running the installer, the system notifies the user that the administrator does not allow the installation of certain software. On smartphones with Android OS, this works differently than on a computer, where there are several accounts, and among them are administrators. Therefore, such a notification does not mean that the process is blocked by any person. This is done by an application that has certain rights in the operating system.
These include the following:
- built-in Google services (phone search, etc.);
- antiviruses;
- opposite to the previous one - viruses;
- programs that restrict access (parental controls).
The first two types of utilities will not give the owner any trouble. All you need to do is make a few settings. The last two groups can force you to tinker with settings and permissions. In the case of Google services and antiviruses:
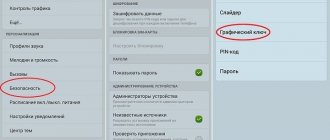
- Settings.
- Item "Security".
- "Administrators"
On the ninth version of the OS:
- Go to the settings menu.
- Find the Biometrics and Security section.
- Select the option at the bottom - Other Security Settings.
- Find the Administrators tab.
You need to find a potential blocker in the list and disable its rights. You should be careful with antiviruses because they can block malware. Instead of disabling them, it's worth looking for a feature that allows you to allow specific files to install. If it does not exist, exclude the antivirus from the list of administrators. It is advisable to return the parameters later.
Once potential interfering programs have been disabled, you need to return to the installation. Try again.
Speaking of a more complex case, when the user knows which administrator prohibits the application from being installed on the internal memory, and the disable function is not available, then more time will have to be spent on settings. Here are some effective methods:
Bypassing these restrictions is only possible by jailbreaking - hacking iOS to gain access to the file system of Apple mobile devices. You can even jailbreak gadgets running iOS 13.3, the latest stable version of Apple’s mobile OS.